Once upon a time ransomware was a keyword in the cyber security alphabet that simply existed but never quite posed a threat. Fast forward to the present and ransomware has become a massive threat to individuals, businesses, institutions and even governments.
While ransomware is not the most prevalent type of malware currently facing end users, the potential for damage is high and the threat is growing every day.
Ransomware has been really evolving for nearly two decades now, and it doesn’t show signs of slowing down anytime soon. Let’s take a look at this evolution and follow up with an outlook on the future of ransomware.
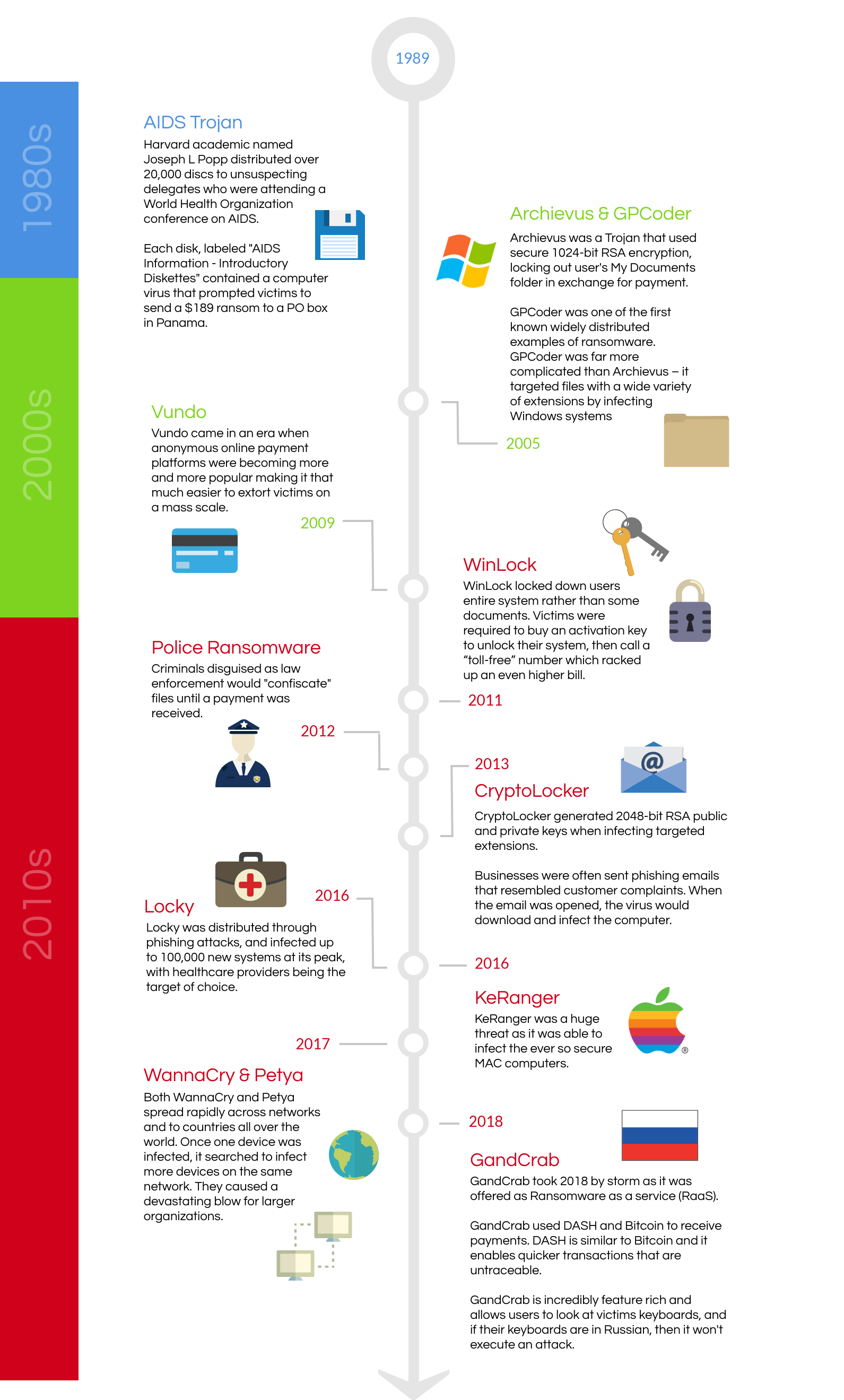
1989 – AIDS Trojan
Ransomware, or at least a very early form of it, appeared two decades ago. In 1989, a Harvard academic named Joseph L Popp distributed over 20,000 discs to unsuspecting delegates who were attending a World Health Organization conference on AIDS.
Each disk, labeled “AIDS Information – Introductory Diskettes” contained a computer virus that silently inserted itself into the user’s computer. After the host computer was rebooted 90 times the virus-activated, promptly hiding away vital directories and encrypting files.
A message box then appeared on the screen prompting victims to send a ransom of $189 to a PO Box in Panama. Popp was eventually arrested, but due to his poor mental health he never stood trial.
2005 – The Year Ransomware Resurfaced
Popp was truly ahead of his time. It would take another 15 years before ransomware would resurface once more. In 2005 the internet had evolved, and the idea of ransomware was revisited once more by hackers who saw an opportunity to make money off unsuspecting victims. This opportunity, however, was now bolstered by new technology the likes Popp could only imagine in 1989.
Archievus
Archievus was a Trojan that used secure 1024-bit RSA encryption. In true ransomware fashion, Archievus locked out the user’s My Documents folder in exchange for payment. While technically the victim still had access to the rest of their folders and subsequent files on their computer, the fact that most users store essential files in the “My Documents” folder still made Archievus a particularly nasty piece of ransomware.
GPCoder
Discovered in 2005, GPCode was one of the first known widely distributed examples of ransomware. GPCoder was far more complicated than Archievus – it targeted files with a wide variety of extensions by infecting Windows systems.
The targeted files were copied and encrypted and the originals were promptly deleted. These new files, which used RSA-1024 encryption, were unreadable and difficult to crack without advanced knowledge.
Victims were then presented with a message across their home screens that directed them to a .txt file (conveniently posted to their desktop) that contained the details needed to pay the ransom and unlock the files that were affected.
2009 – 2012 – Ransomware Undergoes yet another Transformation
It took some time, but it was eventually discovered that GPCoder and Archievus could be detected and removed from a user’s system by running a simple antivirus program. Thus, ransomware once again fell somewhat into obscurity once more.
2009 – Vundo
However, ransomware would undergo yet another transformation soon enough. In 2009 a scareware virus known as Vundo stopped “scaring” its victims into performing a desired action (such as generating a fake security message to guide users to implement a fake fix) and began acting as ransomware, encrypting files on a user’s computer and selling a fix to unlock it.
Vundo’s transformation came at an opportune time for enterprising criminals — anonymous online payment platforms were becoming more and more popular making it that much easier to extort victims on a mass scale.
Furthermore, the technology and sophistication behind ransomware had also vastly improved between 2005 and 2009. By the tail end of 2012, Ransomware had become such a massive threat that it had a black market value worth $5 million.
2011 – Locking Down the Entire System
Ransomware underwent yet another transformation in 2011. This was the year that the WinLock Trojan was unleashed on the world. Unlike previous iterations of ransomware the Winlock Trojan didn’t simply lock out a user from a few files — it locked down the entire system.
The WinLock Trojan targeted Windows operating systems and copied the product activation system, keeping users locked out until they bought an activation key. After a series of steps users were eventually prompted to call a “toll-free” number — one that racked up a significant bill by the time the call was finished.
2012 – Police Ransomware
Police ransomware came into prominence in 2012. This form of ransomware would send messages masquerading as a law enforcement agency (such as the FBI) and making claims that illegal files had been found on a user’s system. The system would then be “confiscated” (locked down) until payment was received.
2013 – 2015 – Stronger faster crypto-encryption
2013 brought with it a far more aggressive iteration of ransomware — CryptoLocker. Gone were the scare tactics of the WinLock Trojan and police ransomware. 2013 criminals were far more straightforward with their demands. The user had two choices — either pay the ransom within three days or lose every file on their system.
CryptoLocker generated 2048-bit RSA public and private keys when infecting targeted extensions. That meant savvy users would have to locate both keys to unlock their systems on their own. However, with such strong encryption, the likelihood of that happening was slim to none.
CryptoLocker was initially distributed via the Gameover Zeus botnet (a network of infected computers whose sole purpose was to spread malware online). Another preferred method of delivering CryptoLocker was spear phishing. Businesses were often sent emails that resembled customer complaints. When the email was opened, the virus would download and infect the computer.
2016 – Ransomware Evolves Once More
With each passing year technology continues to improve and as a result, ransomware becomes more sophisticated. With new platforms to dissect and new modes of delivery to exploit it was only a matter of time before ransomware became a global threat.
Locky
Distributed through phishing attacks, Locky was one of the most dangerous examples of ransomware to date due to the scale and speed at which it infected computers. It’s reported that Locky infected up to 100,00 new systems every day at its peak.
Health-care providers were Locky’s target of choice, as the perpetrators behind the malware caught onto the fact that healthcare providers paid quickly to regain control of their systems.
KeRanger
Up until this point, Mac users were likely feeling very safe. After all, every instance of ransomware to date had only targeted PC users. However, even Mac users weren’t safe from the latest iteration of ransomware, known as KeRanger.
KeRanger was the ransomware that was successful at targeting Mac files. Not only were Mac files capable of being targeted, but also Mac’s restore system “Time Machine” which hindered the user’s ability to roll their system back to an earlier save to overcome any potential problems.
2017 – Global Exploitation
Ransomware had made massive strides in 2016, and it was only a matter of time before a global incident occurred. 2017 was the year that a truly global threat emerged.
WannaCry
The ransomware that practically held the world hostage was called WannaCry. The virus first showed up on May 12, 2017, in Spain. It only took a few hours before WannaCry had spread to hundreds of computers in over a dozen countries. It only took a few days before it had infected more than a quarter of a million computers.
The speed and scale of WannaCry made headlines, raising the alarm to the world at large to the threat of ransomware. The most alarming aspect about WannaCry was the fact that it wasn’t distributed in the same manner as previous ransomware.
It targeted exploits in older versions of Windows. Once one device in a network was infected, WannaCry searched for more devices with the same exploit. This was an especially devastating blow for larger organizations such as hospitals, universities, and financial institutions and one of the reasons WannaCry was so widely publicized.
Petya
Petya was yet another ransomware worm similar to WannaCry — so similar that it also attacked thousands of computers around the world exploiting the same weakness as its predecessor despite security patches having been released to fix the issue.
Users were undoubtedly aware of one thing in the wake of Petya — security patches were no longer something that could be put off for later. The threat had become too great.
2018 – GandCrab
Discovered in 2018, GandCrab ransomware has become the most widespread ransomware of the year. GandCrab’s popularity has grown for a number of reasons, especially because it’s offered as Ransomware as a service (RaaS), which allows any cyber criminal to use the software platform to perform attacks.
GandCrab is spread via spam emails where a user is prompted to download a zip file containing the ransomware. It is also spread via exploit kits, and other various malware. To receive payments from victims, GandCrab uses Bitcoin or Dash. Dash is similar to Bitcoin and it enables quicker transactions that are untraceable.
GandCrab is incredibly advanced and comes packed with loads of features. One of the most interesting features is the ability to look at a victim’s computer keyboard layout before encrypting any files to see if it’s in Russian. If it’s in Russian, it will not affect that user’s computer.
Future of Ransomware
The future of ransomware looks grim (for the good guys anyway). Criminals realize that ransomware is capable of netting them a pretty penny with the average successful attack yielding approximately $1,077 on average.
More facts support the fact that ransomware use will continue to be on the rise. Ransomware attacks rose 350% in 2017.
The success of ransomware such as WannaCry and Petya will likely spawn similar attacks in the future utilizing self-replicating worm technology that exploit the vulnerabilities in computer systems.
However, as we’ve seen over the years, it’s only a matter of time before ransomware makes yet another evolution. With more of our items digitizing every day (such as microwaves, cars, and watches) we may see ransomware begin to target our everyday items as well.
No matter what type of evolution ransomware makes you should do everything in your power to avoid becoming a victim. Update your system whenever a new security patch rolls out, always be suspicious of unknown emails and use caution when surfing online.
Will these measures protect you from becoming a victim of ransomware with 100% certainty? No, but they will certainly lessen your chances of becoming a victim. Stay smart. Stay vigilant.







