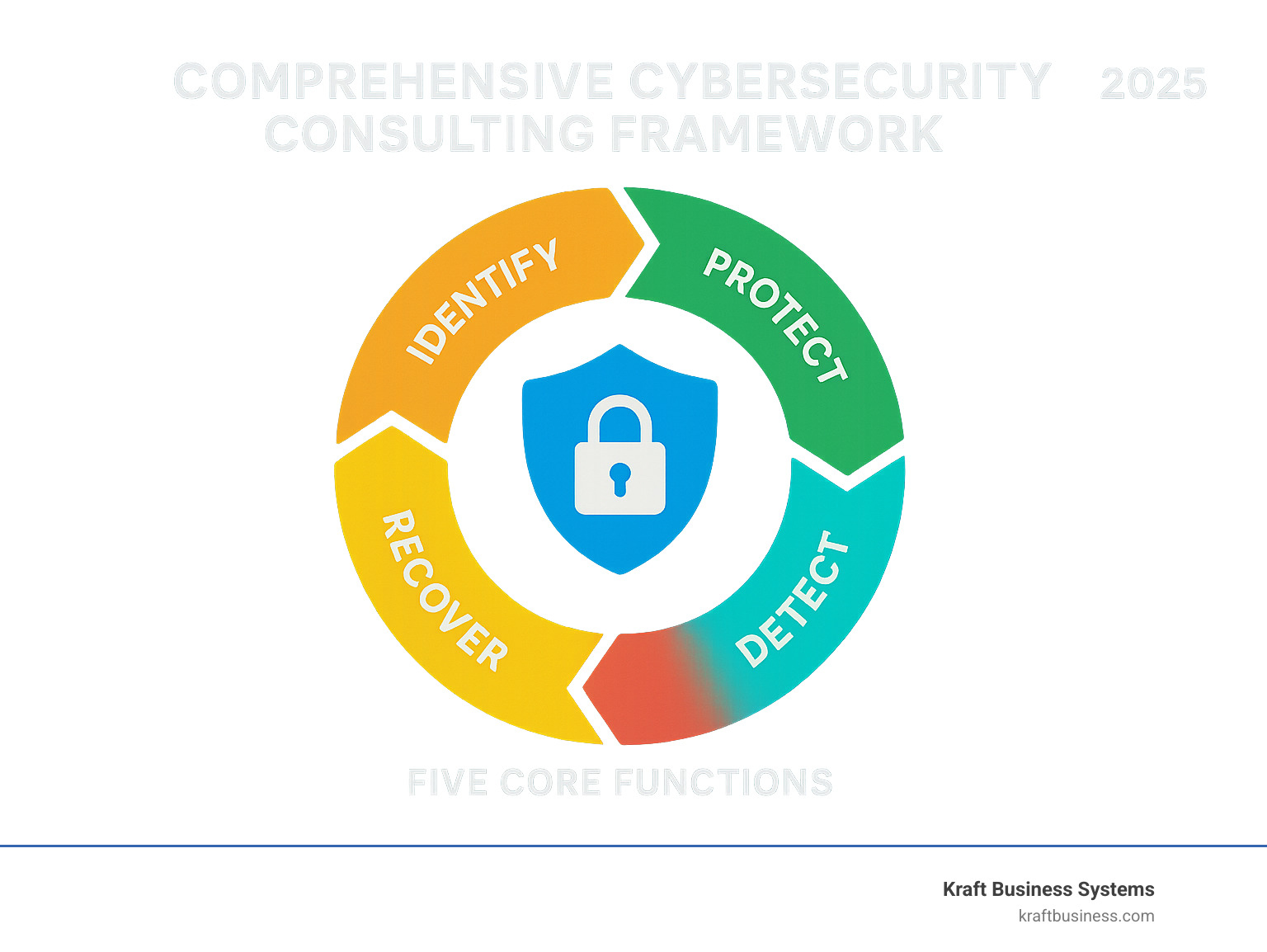
Cybersecurity consulting helps businesses protect their digital assets, ensure compliance, and turn security into a competitive advantage through expert guidance and custom solutions.
Key benefits of cybersecurity consulting include:
- Risk Assessment & Management – Identify vulnerabilities and quantify business risks
- Strategic Security Planning – Align cybersecurity with business objectives
- Compliance Support – Steer regulations like PCI-DSS, HIPAA, and GDPR
- Incident Response – Rapid threat detection and recovery planning
- Virtual CISO Services – Access C-level security expertise without full-time costs
- Technology Integration – Implement advanced security tools and automation
The global cybersecurity consulting market is projected to reach $100 billion by 2025, driven by increasing cyber threats and digital change needs. Small and mid-sized businesses face particular challenges – they’re now prime targets for cybercrime, with 90% of successful attacks caused by human error.
Modern cybersecurity consulting goes beyond traditional defense, positioning security as an enabler of innovation rather than just protection. As one industry expert notes: “Organizations that do not involve cybersecurity in decision-making are exposed to new vulnerabilities.”
The consulting approach has evolved from reactive problem-solving to proactive business enablement. Consultants help companies take calculated risks, accelerate digital change, and build resilience that supports growth rather than limiting it.
Cybersecurity consulting terminology:
- cybersecurity and risk management services for financial institutions
- cybersecurity posture management services
- managed cybersecurity service providers
Cybersecurity Consulting Services: Enhance Security & Compliance
The Spectrum of Cybersecurity Consulting Services
Think of cybersecurity consulting as your business’s personal security team – one that knows exactly where to look for trouble and how to fix it before it becomes a real problem. The range of services available is pretty impressive, covering everything from basic security checkups to advanced threat hunting.
Most consulting engagements start with a Risk Assessment. This is where consultants roll up their sleeves and dig into your systems, looking for potential weak spots. It’s like having a security expert walk through your digital “building” and point out where someone might try to break in. From there, Vulnerability Management kicks in – think of it as ongoing maintenance to keep those weak spots patched up and secure.
Penetration Testing is where things get interesting. Consultants essentially become ethical hackers, trying to break into your systems the same way a real attacker would. It sounds scary, but it’s actually reassuring – you want to know if your defenses will hold up when it really matters.
When something does go wrong (and let’s be honest, it sometimes does), Incident Response planning becomes your lifeline. Good consultants help you create a clear playbook for handling security incidents quickly and efficiently. The faster you can respond, the less damage you’ll face.
Security Program Strategy is about the bigger picture. Rather than just fixing problems as they pop up, consultants help you build security into your business operations from the ground up. With more companies moving to the cloud, Cloud Security expertise has become essential. And as digital interactions get more complex, Digital Identity Management ensures only the right people can access your sensitive information.
The compliance side of things can feel overwhelming. There’s PCI-DSS for payment processing, HIPAA for healthcare data, GDPR for European privacy requirements, and plenty more depending on your industry. Good consultants don’t just help you check the boxes – they help you build sustainable compliance programs that actually make sense for your business.
The goal isn’t to overwhelm you with security measures. It’s to create practical, custom solutions that protect your business while still letting you operate and grow effectively.
Strategic Guidance and Virtual CISO (vCISO) Support
Here’s the thing about the CISO role – it’s incredibly important, but not every business can justify hiring a full-time Chief Information Security Officer. That’s where Virtual CISO services come in, and they’re honestly one of the smartest developments in cybersecurity consulting.
A vCISO gives you access to on-demand expertise and security leadership without the full-time salary and benefits package. Think of it as having a seasoned security executive in your corner who knows your business inside and out, but works with you on a fractional basis.
The real value comes from having someone who can speak both languages – technical security and business strategy. Your vCISO handles the complex stuff like budgeting for security investments and translating technical risks into terms that make sense to your leadership team. They’re also great at stakeholder communication, helping explain why certain security measures matter to people who might not have a technical background.
What makes this model work so well is that you get C-level strategic thinking without C-level overhead. Your vCISO becomes genuinely invested in your success, helping align your cybersecurity efforts with your actual business objectives. They’re not just checking boxes – they’re helping you build a security program that actually enables growth rather than slowing it down.
Proactive Defense: From Threat Hunting to Resilience Planning
The best defense is a good offense, and that’s exactly what proactive cybersecurity is all about. Instead of waiting for something bad to happen, smart businesses are getting ahead of threats with threat intelligence and advanced testing methods.
Attack simulation through Red Team and Purple Team exercises might sound like military operations, but they’re actually pretty straightforward. Red Teams act like attackers, trying to break into your systems using real-world techniques. Purple Teams take it a step further by having your internal security team work directly with the “attackers” to improve your defenses in real-time.
Business continuity planning and disaster recovery are where the rubber meets the road. These aren’t just technical exercises – they’re about making sure your business can keep running when things go sideways. Good consultants help you figure out what’s truly critical to keep your doors open and how to get back up and running as quickly as possible.
Zero Trust architecture has become the gold standard for modern security. The basic idea is simple: don’t trust anyone or anything by default, even if they’re already inside your network. Everyone and everything gets verified before they can access your systems. It sounds paranoid, but it’s actually quite practical and effective.
The beauty of proactive defense is that it builds genuine resilience into your business. You’re not just hoping nothing bad happens – you’re actively preparing for challenges and building systems that can adapt and respond when the unexpected occurs.
Cybersecurity Consulting Services: Enhance Security & Compliance
Aligning Security with Business Objectives for a Competitive Edge
Here’s something many business leaders don’t realize: cybersecurity consulting isn’t just about keeping the bad guys out. It’s actually one of the most powerful tools you have for growing your business and staying ahead of the competition.
Think about it this way: when your security is rock-solid, you can take smart risks that your competitors might be too scared to take. You can adopt new technologies faster, expand into new markets with confidence, and innovate without constantly looking over your shoulder.
Business strategy integration means weaving security into every major decision your company makes. Instead of treating cybersecurity as something that slows you down, it becomes the foundation that lets you move faster and bolder than ever before.
When you have the right security framework in place, you’re enabling innovation rather than blocking it. Your team can explore cutting-edge solutions, your customers trust you with their most sensitive data, and your day-to-day resilience gives you the peace of mind to focus on what really matters – growing your business.
The key is understanding your risk appetite. Every business needs to take some risks to grow, but with expert cybersecurity guidance, you can take the right risks while protecting what matters most. This strategic approach to security becomes your competitive advantage – while your competitors are dealing with breaches and compliance headaches, you’re busy serving customers and expanding your market share.
How expert cybersecurity consulting mitigates financial and reputational risk
Let’s be honest – one major cyber incident can wipe out years of hard work and success. The financial hit alone can be devastating, but the damage to your reputation? That can be even worse.
Risk quantification helps you understand exactly what you’re dealing with. Expert consultants don’t just tell you that cyber threats are scary – they show you the real numbers. What would a breach actually cost your business? How long would it take to recover? These aren’t comfortable conversations, but they’re necessary ones.
The cost of a breach goes way beyond the immediate damage. There are recovery expenses and potential fines, but think about the long-term impact. Lost customers who no longer trust you with their information. Partnerships that fall through because your security reputation is damaged. New business opportunities that disappear because prospects question your reliability.
Customer trust is everything. When customers know you take their data protection seriously, they’re more likely to do business with you, recommend you to others, and stick with you even when competitors come knocking. Your brand reputation becomes a powerful asset instead of a liability.
Insider threat detection is another crucial piece of the puzzle. Sometimes the biggest risks come from inside your own organization – whether it’s a disgruntled employee or someone who accidentally clicks the wrong link. Expert consulting helps you spot these threats before they become major problems.
Leveraging Technology and Expertise for Custom Solutions
The cybersecurity world moves incredibly fast, and keeping up with all the latest tools and techniques can feel overwhelming. That’s where the magic of combining advanced analytics with real human expertise comes in.
Intelligent automation doesn’t replace human judgment – it makes it more powerful. Think of it as giving your security team superpowers. They can process huge amounts of data, spot patterns that would be impossible to catch manually, and respond to threats faster than ever before.
Proprietary assessments mean you’re not getting a one-size-fits-all solution. Every business is different, and your security strategy should reflect your unique challenges, goals, and industry requirements. Expert consultants take the time to understand your specific situation and build something that actually works for you.
Technology partnerships are where things get really interesting. Instead of trying to figure out which security tools are worth your investment, experienced consultants already know what works and what doesn’t. They have relationships with the best vendors and can help you cut through all the marketing noise to find solutions that deliver real value.
Custom solutions are the end goal. You’re not just buying software or services – you’re getting a complete security strategy designed specifically for your business. It’s like having a custom-custom suit instead of something off the rack. It fits better, works better, and makes you look good while keeping you protected.
The cybersecurity world never stands still. Every day brings new threats, fresh attack methods, and evolving challenges that can catch businesses off guard. This is where skilled cybersecurity consulting becomes your compass through an increasingly complex digital maze.
Ransomware attacks continue to be one of the most devastating threats we see. These aren’t the simple “spray and pray” attacks of years past. Modern ransomware is targeted, sophisticated, and designed to cause maximum disruption. Attackers research their victims, understand their business operations, and strike at the most vulnerable moments.
The explosion of connected devices has created another headache: IoT security. Your smart thermostat, security cameras, and even coffee makers can become entry points for cybercriminals. Each connected device is potentially another door that needs to be secured, monitored, and managed.
Then there’s the rise of AI-driven threats. Cybercriminals are using artificial intelligence to create more convincing phishing emails, generate realistic fake voices for social engineering, and automate attacks at scale. It’s like giving criminals a superpower – they can now attack faster and more convincingly than ever before.
Supply chain vulnerabilities add another layer of complexity. You might have excellent security, but if your vendor gets compromised, attackers can use that relationship to reach you. It’s like having a strong front door but leaving the back gate open uped because your neighbor has the key.
The rapid shift to digital operations has expanded attack surfaces dramatically. More cloud services, more remote workers, more digital touchpoints – all of which need protection and oversight.
Achieving and Maintaining Regulatory Compliance
Staying compliant isn’t just about avoiding hefty fines (though those can be painful). It’s about building trust with your customers and proving you take their data seriously. Cybersecurity consulting helps turn the overwhelming world of regulations into manageable, practical steps.
Our approach starts with thorough compliance audits that examine how well your organization meets various regulatory requirements. Whether you’re dealing with PCI-DSS for payment processing, HIPAA for healthcare data, GDPR for European customers, or other frameworks like GLBA, SOX, CCPA, NERC CIP, CIS, and ISA99, we help you understand what’s required and how to get there.
Building strong governance structures is crucial. This means creating clear policies, defining roles and responsibilities, and establishing processes that support ongoing compliance. It’s not enough to check the boxes once – you need systems that keep you compliant as your business grows and changes.
Risk management processes form the backbone of any compliance program. We help you identify where your sensitive data lives, how it moves through your systems, and what could go wrong. This understanding allows you to implement appropriate controls and monitoring.
Continuous monitoring is essential because compliance isn’t a one-time achievement. Regulations change, your business evolves, and new risks emerge. We help establish systems that keep watch over your compliance posture and alert you to any issues before they become problems.
From enhancing consent management for privacy regulations to building comprehensive data protection programs, we make compliance less scary and more manageable. The goal is to operate confidently while meeting all your legal and ethical obligations.
Future-Proofing Your Business: The Forward-Looking Approach of cybersecurity consulting
Looking ahead in cybersecurity can feel like trying to predict the weather in five years. But that’s exactly what good cybersecurity consulting does – it helps you prepare for threats that haven’t fully materialized yet.
Quantum computing risks represent a perfect example of future challenges. When quantum computers become powerful enough, they could potentially crack the encryption we rely on today. That sounds like science fiction, but smart organizations are already planning for this possibility.
Deepfake technology is becoming more sophisticated and accessible. Soon, criminals might use AI-generated videos or audio to impersonate executives, creating convincing social engineering attacks that could fool even careful employees.
OT/ICS security (Operational Technology and Industrial Control Systems) is becoming critical as more industrial systems connect to networks. A cyberattack on these systems doesn’t just steal data – it can shut down production lines, disrupt utilities, or even cause physical damage.
These future challenges require a different mindset. Instead of just reacting to current threats, we help businesses build adaptable security frameworks that can evolve with new risks.
Continuous learning is built into our approach. Our team stays connected to security R&D efforts, emerging threat intelligence, and industry developments. We attend conferences, participate in security communities, and maintain relationships with researchers and other experts.
This forward-looking approach helps our clients balance innovation with security. You don’t want security concerns to prevent you from adopting beneficial new technologies, but you also can’t ignore the risks. We help you explore new opportunities while building in appropriate safeguards.
The goal is simple: ensure your business not only survives but thrives as the digital world continues to evolve. By thinking ahead and preparing for tomorrow’s threats, you can focus on growing your business with confidence.
Frequently Asked Questions about Cybersecurity Consulting
We know that exploring cybersecurity consulting can feel overwhelming at first. You’re probably wondering about costs, what success looks like, and what you’ll need to do as our partner. Let’s tackle the questions we hear most often from business owners just like you.
Is cybersecurity consulting affordable for small and medium-sized businesses (SMBs)?
Here’s something that might surprise you: cybersecurity consulting isn’t just for Fortune 500 companies anymore. We’ve actually seen a major shift where SMBs have become prime targets for cybercriminals. Why? Because hackers know smaller businesses often have fewer defenses but still handle valuable data.
The cost of doing nothing far outweighs the investment in proper security. Think about it this way – one successful cyber attack can wipe out years of hard work and growth. We’ve designed our services to be scalable, which means we can work within your budget while still providing meaningful protection.
Our fractional models are particularly popular with growing businesses. Instead of hiring a full-time security executive (which can cost six figures annually), you get access to expert-level guidance through our fractional CISO services. It’s like having a security expert on speed dial without the overhead costs.
The return on investment becomes clear when you consider what you’re protecting: your customer data, your reputation, your ability to operate without interruption, and your future growth potential.
How is the success of a consulting engagement measured?
Great question – and one that shows you’re thinking like a smart business owner. We don’t just hand you a thick report and call it done. Success in cybersecurity consulting is measured through concrete improvements you can actually see and feel.
We track reduced incidents over time. Fewer security alerts, less downtime, and fewer “fire drill” moments mean our partnership is working. We also focus on speed metrics like time to detection and time to response. When something does happen, how quickly can we spot it and shut it down?
Compliance scores provide another clear benchmark. Whether you need to meet PCI-DSS, HIPAA, or other regulatory requirements, we measure how well you’re maintaining those standards. But beyond the technical metrics, we look at business alignment.
Are you able to pursue new opportunities with confidence? Are your customers more trusting? Can you sleep better at night knowing your business is protected? These softer measures often matter just as much as the hard numbers when it comes to ROI and overall success.
What is our role as the client in a consulting partnership?
This is where the magic happens – when we work together as true partners. Cybersecurity consulting isn’t something we do to you; it’s something we do with you.
Your most important role is honest collaboration. We need you to share the real challenges you’re facing, not just the ones that sound good in meetings. The more transparent you are about your concerns, budget constraints, and business goals, the better we can tailor our approach.
Information sharing is crucial too. We can’t protect what we don’t know about. This means giving us access to systems, explaining your workflows, and helping us understand how your team actually works day-to-day.
When we make recommendations, we need you to help with the decision-making process. You know your business better than anyone, so your input shapes which solutions will actually work in your environment.
Implementing recommendations is where the rubber meets the road. We can design the perfect security strategy, but it only works if it gets put into practice. This often means making some changes to how things are done, and that requires buy-in from your team.
Finally, fostering a security culture within your organization amplifies everything we do together. When your entire team understands their role in keeping the business secure, you’ve created a human firewall that’s incredibly powerful. We’ll help you build this culture through training and awareness programs that actually engage people rather than putting them to sleep.
The best partnerships happen when both sides are invested in the outcome. We bring the expertise and you bring the business knowledge – together, we build something stronger than either could create alone.
Conclusion: Your Strategic Partner in Digital Resilience
Throughout this guide, we’ve seen how cybersecurity consulting transforms from a necessary expense into a strategic investment that drives real business value. It’s not just about building walls around your data – it’s about creating a foundation that lets your business grow, innovate, and compete with confidence.
The world of cyber threats will keep evolving, but you don’t have to face these challenges alone. A proactive partnership with the right consulting team means you’re not just reacting to problems as they arise. Instead, you’re staying ahead of the curve, turning potential vulnerabilities into competitive strengths.
Cybersecurity consulting becomes truly powerful when it enables your business rather than limiting it. When security is woven into your business strategy from the ground up, you can take calculated risks, explore new markets, and accept digital change without constantly looking over your shoulder.
At Kraft Business Systems, we understand that every business in Michigan – from the busy streets of Detroit to the growing tech scene in Grand Rapids, from established companies in Ann Arbor to emerging businesses in Traverse City, Lansing, Wyoming, and Acme – faces unique challenges. Our team of consultants and industry experts takes the time to understand what makes your business tick.
We’re not just here to check boxes or deliver reports that sit on shelves. We’re here to be your strategic partner, helping you steer the complexities of cybersecurity while keeping your business goals front and center. Whether you need a virtual CISO to guide your security strategy or comprehensive managed services to handle the day-to-day details, we’re committed to making security work for your business, not against it.
Your digital future doesn’t have to be uncertain. With the right partnership, robust planning, and proactive approach, you can build the kind of resilience that not only protects your business but propels it forward.
Secure your business with managed cybersecurity services