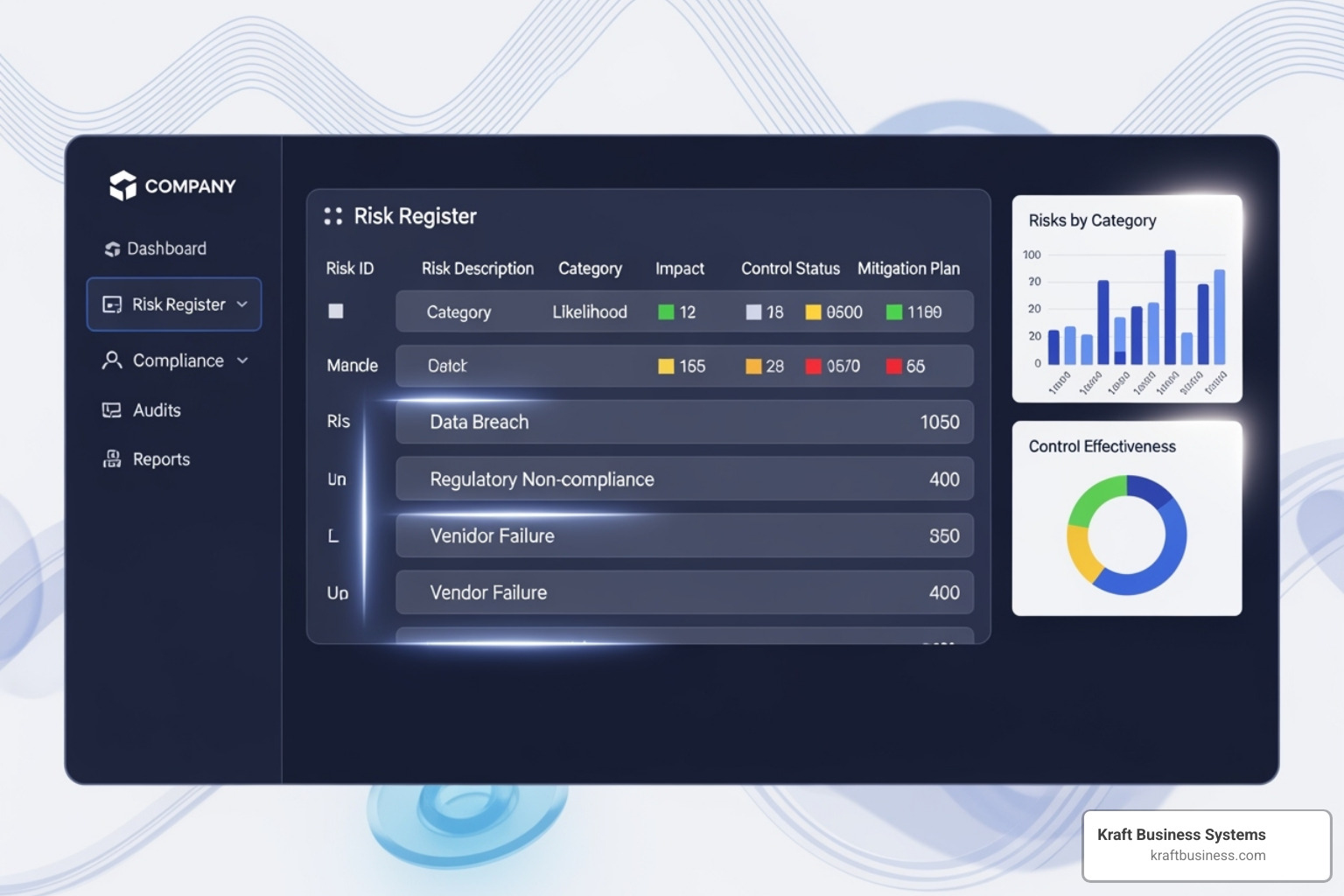
A GRC risk register is a central document for tracking, monitoring, and managing all identified risks within your Governance, Risk, and Compliance framework. It provides the operational foundation for making informed decisions about potential threats to your business.
Key components of a GRC risk register:
- Risk identification and description: What could go wrong and why.
- Impact and likelihood assessment: How severe and how probable.
- Risk prioritization: Which risks require immediate attention.
- Mitigation strategies: The action plan to reduce threats.
- Risk ownership: Who is accountable for each risk.
- Status tracking: The current state and progress of mitigation.
In today’s complex business environment, managing risk is essential for survival. Research shows that 65% of senior finance leaders agree that the volume and complexity of corporate risks have changed “mostly” or “extensively” over the last five years. Many organizations, however, struggle to keep their risk management processes current.
Without a risk register, you cannot effectively protect your assets or prioritize threats. A GRC risk register transforms scattered concerns into actionable intelligence, serving as an early warning system, a decision-making compass, and a roadmap for building organizational resilience against cybersecurity threats, operational disruptions, and compliance challenges.
Essential grc risk register terms:
What is a Risk Register and Why Is It a GRC Cornerstone?
Think of a GRC risk register as your organization’s early warning system. It’s a centralized document that captures potential threats—from cyberattacks and equipment failures to regulatory changes and supply chain disruptions. More than a list, it’s a dynamic tool that transforms vague concerns into actionable intelligence through a systematic approach to risk identification.
A risk register’s power lies in its role as a centralized repository. When risks are scattered across departments and emails, you lose the big picture. A well-maintained register creates a single source of truth, which leads directly to improved decision-making. Leadership can allocate resources and respond to threats with clear, comprehensive data.
The register also drives increased accountability. With a designated owner and clear mitigation steps for each risk, everyone knows their role in keeping the organization safe. This is critical, as the old ways of managing risk—sticky notes and siloed spreadsheets—can’t keep up with today’s fast-moving threat landscape.
The Anatomy of an Effective Risk Register
An effective GRC risk register captures key information for each risk:
- Risk ID: A unique identifier for easy tracking.
- Risk Description: A clear cause-and-effect statement, such as, “Lack of multi-factor authentication could lead to unauthorized access to customer data.”
- Risk Category: Helps organize risks (e.g., Operational, Financial, Cybersecurity) to spot trends.
- Likelihood & Impact: Ratings that quantify how probable a risk is and the potential damage, providing a basis for prioritization.
- Risk Score/Priority: A calculated score (e.g., Likelihood x Impact) to rank risks from most to least critical.
- Mitigation Plan: Specific actions, timelines, and success metrics to address the risk.
- Risk Owner: The individual accountable for ensuring the mitigation plan is executed.
- Status: The current state of the risk (e.g., Identified, In Progress, Mitigated).
- Residual Risk: The risk that remains after mitigation efforts, helping leadership make informed risk acceptance decisions.
Key Benefits of a Well-Maintained Risk Register
A properly maintained GRC risk register delivers organization-wide benefits:
- Improved visibility: Provides a full view of the threat landscape, revealing connections between risks.
- Proactive threat management: Shifts the organization from reactive firefighting to strategic preparation.
- Better resource allocation: Focuses limited budgets on the most significant threats.
- Streamlined compliance: Serves as clear evidence to auditors of your risk management processes.
- Improved communication: Creates a shared understanding of risks across departments and stakeholders.
- A risk-aware culture: Encourages everyone to think about potential problems before they escalate.
When to Implement a Risk Register
Integrate a risk register into regular business processes:
- Strategic planning: Identify potential roadblocks to long-term goals from the start.
- Project initiation: Address risks introduced by new initiatives, such as new software or market expansion.
- Responding to environmental changes: Quickly assess new risks from regulations, technology, or market shifts.
- Regular business reviews: Keep risk management a central part of operational thinking.
For comprehensive risk management, the register is the foundation of a formal GRC Risk Management program and is crucial for maintaining ongoing Risk Management and Compliance efforts.
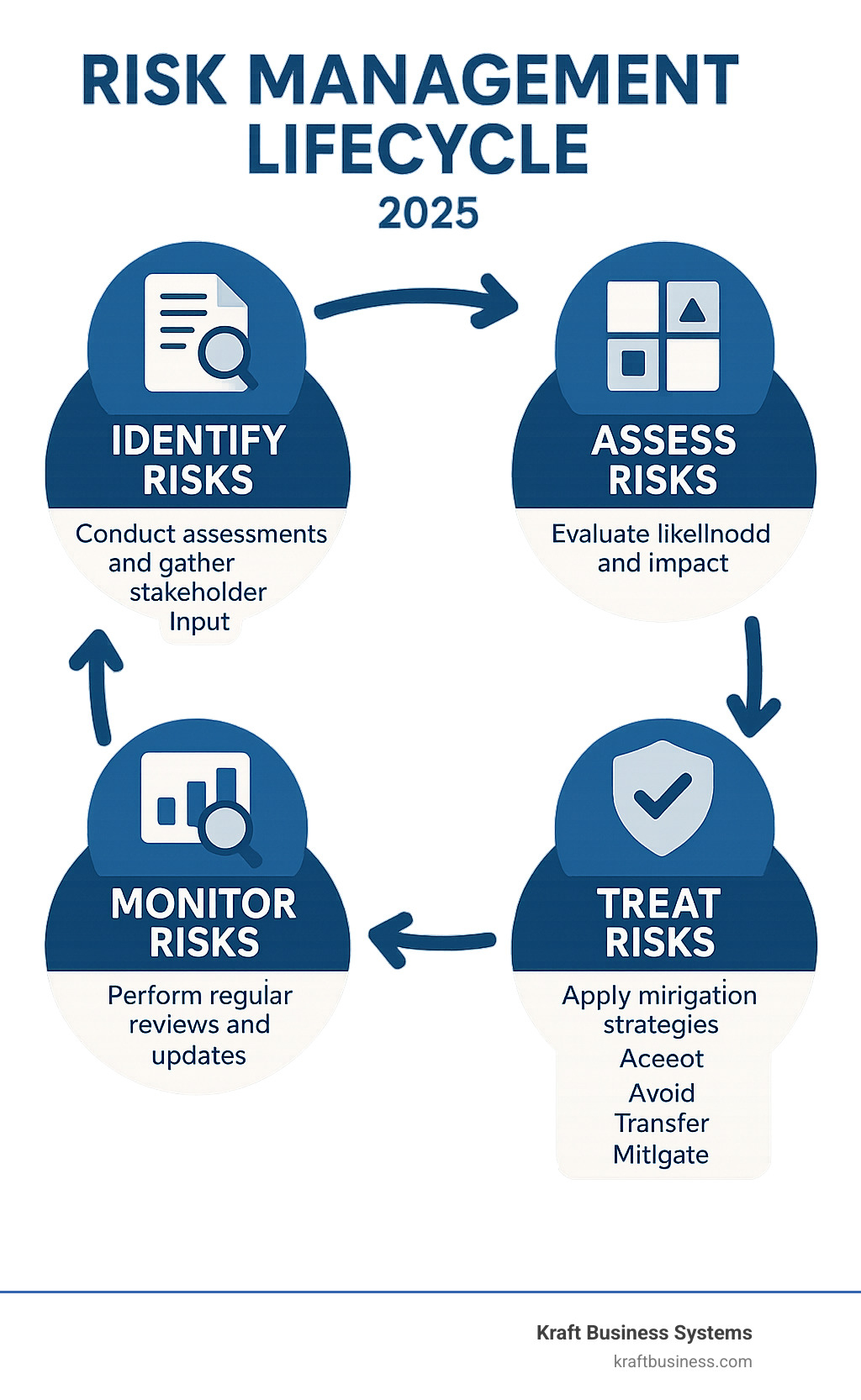
Building and Maintaining Your GRC Risk Register: A Step-by-Step Guide
Creating an effective grc risk register requires a solid blueprint. We follow a practical, NIST-aligned approach that turns this task into manageable steps. Your risk register should be a living document that evolves with your business, not a one-time project.
Step 1: Identify and Describe Risks
The foundation of your risk register is capturing all potential threats. This requires input from across your organization.
- Conduct brainstorming sessions with cross-functional teams from IT, HR, finance, and operations to gain diverse perspectives.
- Review past incidents, near misses, and audit findings to identify recurring issues.
- Use a cause-and-effect format for clarity. Instead of “data breach,” write “Outdated software could allow unauthorized access, resulting in customer data exposure and regulatory penalties.” This explains the what, why, and potential consequences.
- Cover a full spectrum of threats, including operational, financial, and cybersecurity risks. With 54% of organizations experiencing cyberattacks in the past year, these deserve special attention.
For more on this process, see our guide on Cybersecurity Risk Assessment.
Step 2: Assess, Analyze, and Prioritize
Once risks are identified, determine which ones need immediate attention.
- Use qualitative analysis (e.g., Low, Medium, High) for a quick assessment of likelihood and impact. For critical risks, consider quantitative analysis with specific financial figures.
- Create clear criteria for your scales to ensure consistency. Define what “High Impact” means in dollar amounts or operational downtime.
- Calculate risk exposure by multiplying likelihood and impact to get a risk score for prioritization.
- Develop a risk heat map to visually represent your critical vulnerabilities, allowing you to focus on high-scoring risks first.
For authoritative guidance, NISTIR 8286 offers excellent frameworks for managing risk registers.
Step 3: Develop a Response and Assign Ownership
Now, decide what to do about each risk. This turns your grc risk register into a strategic tool.
- Choose a response strategy: Accept the risk if the impact is low. Avoid it by changing a process. Transfer it via insurance. Or mitigate it by implementing controls to reduce its likelihood or impact.
- Assign a risk owner for every risk. This person is accountable for ensuring the risk is managed and the mitigation plan is executed.
- Create detailed action plans for mitigated risks, including specific steps, timelines, and required resources. Vague plans like “improve security” are ineffective.
Step 4: Monitor, Review, and Maintain
Your grc risk register must be a living document.
- Perform continuous monitoring to watch for new threats and changes in existing risks.
- Establish a regular review cadence, such as quarterly reviews with risk owners and key stakeholders, to keep the register accurate.
- Engage stakeholders to get real-world insights on whether mitigation strategies are working.
- Update risk status as actions are completed or circumstances change. An outdated register provides a false sense of security.
Integrate your register with broader IT Compliance and Risk Management efforts for a cohesive approach.
Beyond the Spreadsheet: Integrating the Risk Register into ERM and Compliance
The true power of a grc risk register is open uped when it’s integrated into core processes, supported by technology, and used to satisfy auditors. While a spreadsheet may work for small businesses, growing organizations need a more sophisticated approach to manage risk effectively.
How a Risk Register Powers Enterprise Risk Management (ERM)
In Enterprise Risk Management (ERM), your grc risk register is the foundational building block. ERM aims to manage risks that could interfere with organizational objectives, and the register is where this work begins.
- It’s the foundational ERM tool, providing the granular data that feeds your enterprise-wide risk profile.
- It facilitates risk aggregation by using a standardized format, allowing you to compare and prioritize risks from different business areas (IT, finance, operations).
- It provides a holistic risk view, revealing how different risks might interact or cascade across the organization.
- It aligns IT risk with business objectives, linking technical risks like cyberattacks to their potential impact on revenue, customer satisfaction, or operational continuity.
- It supports strategic decisions by giving leadership a clear, aggregated understanding of enterprise risks.
To improve your ERM capabilities, consider exploring Enterprise GRC Software.
The Role of Technology and GRC Platforms
While a spreadsheet might suffice initially, managing a comprehensive grc risk register effectively demands specialized technology as your program matures.
- Moving beyond spreadsheets is necessary when manual processes become unwieldy and error-prone. They lack real-time capabilities and robust version control.
- GRC platforms offer automation, handling routine tasks like sending reminders and calculating risk scores, freeing your team for strategic work.
- They provide standardized workflows, enforcing consistent processes for risk identification, assessment, and mitigation across the organization.
- Real-time dashboards offer immediate insights into your current risk posture and mitigation progress, enabling faster decision-making.
- Control libraries with pre-built regulatory frameworks help you map risks to controls and identify coverage gaps.
A dedicated GRC Tool streamlines your entire risk management process and provides a single source of truth.
Streamlining Audits and Ensuring Compliance
A well-maintained grc risk register is invaluable for compliance and audits, serving as powerful evidence of your commitment to responsible risk management.
- It demonstrates due diligence by showing auditors you have a systematic process for identifying, assessing, and responding to risks.
- It provides a clear audit trail, logging all changes, assessments, and mitigation actions for complete transparency.
- It helps map risks to controls, directly linking identified risks to specific internal controls and external regulatory requirements.
- It helps meet regulatory requirements like SOX, ISO 27001, and HIPAA, which mandate a structured approach to risk management.
- It simplifies GRC audit management by centralizing all necessary risk and control information, leading to more efficient audits.
For more on streamlining your audit process, explore our guide on GRC Audit Management.
Common Pitfalls and Best Practices
Building a successful grc risk register means avoiding common mistakes while embracing proven best practices. This is the key to creating a strategic tool rather than a document that gathers dust.
Common Pitfalls to Avoid
These preventable mistakes can derail your risk management efforts:
- Vague risk descriptions: Avoid generic entries like “system failure.” Be specific: “Aging server hardware could fail, causing a 4-hour outage and disrupting customer service.”
- Inconsistent scoring: Using different scales (e.g., 1-10 vs. low-medium-high) across teams makes it impossible to prioritize risks effectively.
- Lack of ownership: If a risk has no clear owner, it becomes no one’s responsibility and is likely to go unaddressed.
- “Set it and forget it” mentality: A risk register must be a living document. An outdated register provides a false sense of security as your risk landscape changes.
- Poor communication: If the register is not shared and understood by front-line employees and executives, it fails to foster a risk-aware culture.
- Overly complex registers: An overly burdensome register with too many categories or complex scoring will be abandoned. Start simple and add complexity only as needed.
Best Practices for Success
Organizations with successful grc risk registers share these characteristics:
- Foster a risk-aware culture: Leadership should encourage open communication about risks and near-misses at all levels.
- Keep it simple and clear: A practical, usable register is better than a complex one that no one uses. Focus on the essentials: the risk, its likelihood and impact, the owner, and the plan.
- Ensure strong leadership buy-in: When leaders use the register for strategic planning and resource allocation, it demonstrates its importance to the entire organization.
- Integrate with other business processes: Link risk assessments to project approvals, budget planning, and performance evaluations to embed risk management into daily operations.
- Provide regular training: Ensure staff and risk owners understand their responsibilities and how to use the register effectively.
- Use a structured framework: Leverage established approaches like the NIST Cybersecurity Framework to build a credible and consistent risk management process.
Frequently Asked Questions about the GRC Risk Register
Here are answers to common questions we receive from clients about implementing and managing a grc risk register.
What is the difference between a risk register and a risk assessment?
A risk assessment is the active process of identifying and analyzing potential threats to determine their likelihood and impact. It’s the investigation phase.
The grc risk register is the structured document or tool where you log, track, and manage the findings from that assessment. The assessment feeds the register, which becomes the living repository for managing those risks over time. One is a process; the other is the record of that process.
How often should a risk register be updated?
Your grc risk register should be a living document. We recommend a formal review at least quarterly. However, it should be updated immediately whenever significant changes occur in your business, such as launching a new system, experiencing a security incident, or facing new regulations.
An outdated register is like a smoke detector with dead batteries—it provides a false sense of security. Quarterly reviews keep you current, but real-time updates keep you protected.
Who is responsible for the risk register?
Ownership operates on two crucial levels:
- Strategic Ownership: A single person, like a Risk Manager or CISO, should own the entire grc risk register as a system. This person ensures the process is consistent and the register is maintained.
- Operational Ownership: Every single risk in the register must have an assigned owner at the operational level (e.g., an IT Director for a cyber risk, a CFO for a financial risk). This individual is responsible for monitoring their assigned risk and executing the mitigation plan.
This dual-ownership model creates both centralized oversight and distributed accountability, ensuring nothing falls through the cracks.
Conclusion
A robust grc risk register is more than a compliance checkbox—it’s a strategic tool that transforms how your organization manages uncertainty. It acts as an early warning system, helping you spot potential issues before they escalate.
By systematically identifying, assessing, and treating risks, you build genuine resilience, make better data-driven decisions, and create a secure foundation that supports growth. A well-maintained grc risk register turns scattered worries into actionable intelligence, giving you a clear picture of your risk landscape and your plan to address it.
This proactive approach embeds risk management into your organizational DNA. Your team begins to think ahead, decisions are made with a clearer understanding of trade-offs, and you are better prepared for unexpected challenges.
For organizations in Grand Rapids and across Michigan, implementing these practices can feel overwhelming. You don’t have to do it alone. Kraft Business Systems provides comprehensive IT security and compliance services to help you build a GRC framework that truly protects your business.
Our team works with you to create a grc risk register and risk management approach that fits your reality. Whether you’re just starting your GRC journey or strengthening an existing program, we’re here to help you build the resilient, secure foundation your business deserves.