AI Overview:
IT compliance and certification services are now strategic investments that drive business growth, not just legal necessities. Beyond meeting regulatory requirements, they protect sensitive data, build customer trust, and unlock market opportunities. Frameworks like SOC 2, ISO 27001, HIPAA, and FedRAMP have become essential for demonstrating credibility and security readiness in today’s digital economy.
Why IT Compliance and Certification Services Are Your Business’s Best Investment: Top 7 Essential Guide
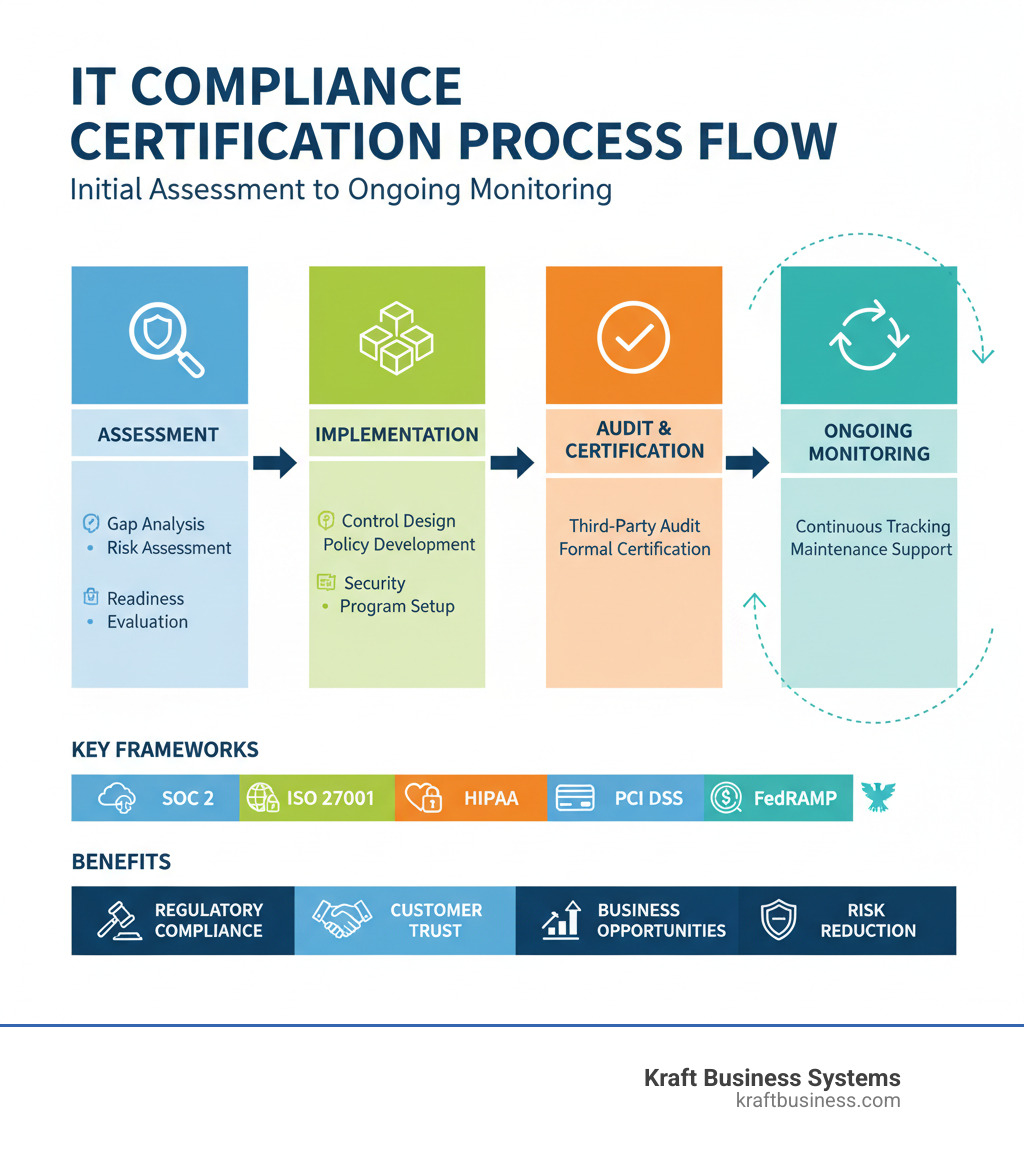
IT compliance and certification services help organizations meet regulatory requirements, protect sensitive data, and demonstrate security standards to customers and partners. These services encompass everything from initial assessments and gap analyses to ongoing monitoring and formal certification processes across frameworks like SOC 2, ISO 27001, HIPAA, and FedRAMP.
Quick Overview of IT Compliance Services:
- Assessment Services: Gap analysis, risk assessments, and readiness evaluations
- Implementation Support: Control design, policy development, and security program setup
- Audit and Certification: Third-party assessments leading to formal certifications
- Ongoing Monitoring: Continuous compliance tracking and maintenance support
- Multi-Framework Management: Streamlined approach to handle multiple standards simultaneously
If you’re a business owner juggling outdated systems and cybersecurity threats, you’ve probably wondered: “Do I really need all these compliance certifications?” The short answer is yes – but not necessarily all at once, and definitely not without the right guidance.
Here’s the reality: compliance isn’t just about avoiding fines anymore. It’s about opening doors to new business opportunities, building unshakeable trust with clients, and creating a competitive advantage that your competitors can’t easily replicate.
As one technology manager noted about working with compliance experts: “You’re not my vendor. You’re not somebody I tell what to do or you tell me what to do. You’re somebody who cares about my business.”
The compliance landscape has evolved dramatically. What used to require armies of consultants and months of painful audits can now be streamlined through automation platforms, expert partnerships, and strategic approaches that tackle multiple frameworks simultaneously.
But here’s what nobody talks about: 75% of compliance projects run over budget because organizations dive in without understanding the hierarchy of certifications or how to leverage modern tools effectively.
This guide cuts through the confusion. We’ll rank the most demanding certifications, show you how to streamline the process with the right partners, and help you stay ahead of emerging trends that could impact your compliance strategy.
It compliance and certification services further reading:
- IT compliance and governance
- it compliance and risk management
- information technology audit services
The Hierarchy of IT Compliance: From Most to Least Demanding
Picture this: you’re standing at the base of Mount Everest, looking up at various climbing routes. Some are gentle slopes perfect for beginners, while others are sheer cliff faces that challenge even the most experienced mountaineers. IT compliance and certification services work the same way – each framework has its own level of difficulty, cost, and complexity.
Understanding this hierarchy is crucial because it helps you make smart decisions about where to invest your time, money, and resources. You wouldn’t start with the most challenging certification if your business doesn’t need it, just like you wouldn’t use a sledgehammer to hang a picture frame.
Let’s break down the landscape from the most demanding certifications to the more manageable ones:
| Certification | Who Needs It | Relative Difficulty | Typical Cost Range | Primary Focus |
|---|---|---|---|---|
| FedRAMP | Cloud Service Providers (CSPs) serving U.S. federal agencies | Very High | Hundreds of thousands to over a million dollars | Federal Government Data Security |
| HITRUST CSF | Healthcare organizations, their business associates, and technology providers | High | Tens to hundreds of thousands of dollars | Protecting Electronic Protected Health Information (ePHI) |
| CMMC | Organizations in the Defense Industrial Base (DIB) and their supply chain | High | Hundreds of thousands to millions of dollars | Protecting Controlled Unclassified Information (CUI) |
| PCI DSS | Any organization handling payment card data | Medium-High | Varies based on transaction volume and level | Securing Cardholder Data |
| SOC 2 | Service organizations (e.g., SaaS providers, data centers) | Medium | Tens of thousands to hundreds of thousands of dollars | Security, Availability, Processing Integrity, Confidentiality, Privacy |
| ISO 27001 | Organizations seeking international recognition for their Information Security Management System (ISMS) | Medium | Tens of thousands of dollars | Holistic Information Security Management |
| HIPAA | Healthcare providers, health plans, and healthcare clearinghouses | Medium-Low | Varies based on organization size and complexity | Protecting Protected Health Information (PHI) |
1. FedRAMP (Federal Risk and Authorization Management Program)
If compliance certifications were Olympic sports, FedRAMP would be the decathlon – it tests everything and demands peak performance across all areas. This certification sits at the top of our difficulty mountain for good reason.
FedRAMP isn’t just about checking boxes; it’s about earning an Authorization to Operate (ATO) that proves your cloud services are secure enough for federal agencies. Think of it as getting a security clearance for your technology platform.
The challenge comes from the sheer scope of requirements. Depending on your impact level, you’ll need to implement anywhere from 125 controls for low-impact systems all the way up to 421 controls for high-impact systems. Each control requires detailed documentation, implementation, and ongoing monitoring.
What makes FedRAMP particularly demanding is the continuous monitoring requirement. This isn’t a “get certified and forget it” situation. You’re committing to ongoing security assessments, vulnerability scanning, and prompt remediation of any issues that arise. It’s like having a security guard who never takes a break.
The recent updates aligning FedRAMP with NIST SP 800-53 Rev. 5 have added new controls and improved guidance on privacy and supply chain risk management. The FedRAMP Authorization Act formalized this as the primary evaluation program for cloud service providers in December 2022, making it even more critical for organizations serving federal clients.
2. HITRUST CSF (Health Information Trust Alliance Common Security Framework)
Healthcare data is some of the most sensitive information on the planet, which is why HITRUST certification sits near the top of our difficulty hierarchy. This framework doesn’t just focus on one standard – it’s like a Swiss Army knife that combines HIPAA, PCI DSS, and ISO requirements into one comprehensive approach.
What makes HITRUST particularly challenging is its prescriptive nature. While some frameworks give you flexibility in how you meet requirements, HITRUST provides detailed, specific guidance on exactly what you need to do. This can be helpful, but it also means there’s less wiggle room.
The framework offers different assessment levels based on your risk exposure. The e1 Assessment covers 44 essential controls – think of this as the foundation level. The i1 Assessment steps up to 187 intelligent, risk-based controls. At the top, the r2 Assessment includes over 400 controls across 19 domains, providing comprehensive risk management.
Healthcare organizations love HITRUST because it demonstrates robust commitment to protecting patient data. When you’re dealing with electronic Protected Health Information (ePHI), having this certification sends a clear message to patients, partners, and regulators that you take data protection seriously.
The framework continues evolving with CSF version 11 released in 2023, and they even launched an AI Security Assessment in November 2024 to address emerging AI-related risks. Organizations must use the MyCSF tool for assessment reporting, which helps streamline the process.
3. CMMC (Cybersecurity Maturity Model Certification)
If you’re in the Defense Industrial Base (DIB), CMMC isn’t optional – it’s your ticket to continue doing business with the Department of Defense. This certification focuses on protecting Controlled Unclassified Information (CUI), which might sound boring but is actually critical to national security.
The beauty of CMMC 2.0 is its simplified three-level approach. Level 1 (Foundational) requires annual self-assessment for basic cyber hygiene – think of this as making sure you lock your doors and windows. Level 2 (Advanced) aligns with NIST SP 800-171 and may require third-party assessment. Level 3 (Expert) implements improved controls from NIST SP 800-172 and definitely requires government assessment.
What makes CMMC challenging isn’t just the technical requirements – it’s the supply chain implications. If you’re a subcontractor working with a prime contractor who has DoD contracts, you’ll need appropriate CMMC certification too. This creates a ripple effect throughout the entire defense supply chain.
The stakes are high because without proper CMMC certification, you’ll be ineligible for DoD contracts once the requirements are fully implemented. The final CMMC Program Rule became effective in December 2024, with mandatory certification for contract awards beginning in Spring 2025.
4. PCI DSS (Payment Card Industry Data Security Standard)
Every time someone swipes, dips, or taps a credit card at your business, PCI DSS compliance becomes your responsibility. This standard exists for one simple reason: to reduce credit card fraud and protect cardholder data.
The framework revolves around 12 fundamental requirements that cover everything from building secure networks to maintaining information security policies. These aren’t suggestions – they’re mandatory requirements that can significantly impact your business if ignored.
Your compliance level depends on your annual transaction volume. Level 1 organizations processing over 6 million transactions annually face the most stringent requirements, while Level 4 organizations handling fewer than 20,000 transactions have lighter requirements. Regardless of your level, everyone must complete quarterly vulnerability scans.
The recent PCI DSS v4.0.1 update in June 2024 clarified existing requirements and built upon the significant changes in v4.0, which strengthened authentication, encryption, and monitoring procedures. Organizations had to transition from v4.0 to v4.0.1 as v4.0 was retired in December 2024.
Non-compliance can be costly, leading to fines, increased transaction fees, and potentially losing the ability to process credit card payments entirely. For businesses in Grand Rapids and beyond, having robust managed cybersecurity services can help maintain PCI compliance while focusing on your core business operations.
5. SOC 2 (System and Organization Controls 2)
In today’s world where businesses rely heavily on cloud services and SaaS platforms, SOC 2 certification has become the gold standard for service organizations. If you’re storing, processing, or transmitting customer data, your clients want proof that you’re handling it responsibly.
SOC 2 focuses on the Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. You don’t need to address all five – you can choose which criteria apply to your services. Most organizations start with Security since it’s typically required by customers.
The key difference between Type I and Type II reports is time. A Type I report is like a photograph – it shows your controls at a specific point in time. A Type II report is more like a movie, demonstrating that your controls operated effectively over a period (typically 3-12 months).
What makes SOC 2 valuable is its customer-facing nature. This isn’t just about compliance – it’s about competitive advantage. When prospects are evaluating vendors, having a clean SOC 2 Type II report can be the deciding factor.
The updated SOC 2 Audit Guide from October 2022 improved reporting quality and consistency, making these reports even more valuable for building customer trust and meeting contractual obligations.
6. ISO 27001
Think of ISO 27001 as the international passport for information security. This certification demonstrates that your organization has implemented a comprehensive Information Security Management System (ISMS) that follows globally recognized best practices.
What sets ISO 27001 apart is its risk-based approach. Instead of prescribing specific controls, it requires you to identify your information security risks, assess their potential impact, and implement appropriate controls to manage them. This flexibility makes it suitable for organizations of all sizes and industries.
The heart of ISO 27001 is Annex A, which contains a comprehensive menu of security controls. You don’t need to implement every control, but you must justify why certain controls aren’t applicable to your organization.
The latest version, ISO 27001:2022, reflects evolving security challenges with a restructured Annex A, 11 new controls, and revisions to existing controls for clarity. These updates address emerging threats and provide better guidance for modern security challenges.
Global recognition is one of ISO 27001’s biggest advantages. Whether you’re doing business in Europe, Asia, or anywhere else, this certification is understood and respected worldwide.
7. HIPAA (Health Insurance Portability and Accountability Act)
HIPAA compliance sits at the foundation of our hierarchy not because it’s easy, but because it’s legally required for anyone handling Protected Health Information (PHI) in the United States. There’s no “opting out” of HIPAA if you’re a covered entity or business associate.
The framework consists of three main components: the Privacy Rule governs how PHI can be used and disclosed, the Security Rule addresses technical, administrative, and physical safeguards for electronic PHI, and the Breach Notification Rule requires prompt notification when data breaches occur.
The Security Rule’s administrative safeguards include policies and procedures for managing security measures and workforce security. Physical safeguards control access to electronic information systems and workstations. Technical safeguards involve technology controls like access controls, audit controls, and transmission security.
While HIPAA allows flexibility in implementation based on your organization’s risk assessment, it still requires significant dedication. You must conduct regular risk assessments, maintain detailed documentation, and continuously review and update your security measures.
Recent developments include a Notice of Proposed Rulemaking (NPRM) issued by HHS in January 2025 to strengthen the HIPAA Security Rule, responding to increasing cybersecurity threats in healthcare.
The beauty of understanding this hierarchy is that it helps you make strategic decisions about your compliance journey. You might find that achieving one certification creates a foundation for others, or that your industry requirements naturally point you toward specific frameworks. Either way, you’re now equipped to steer this complex landscape with confidence.
Streamlining the Journey with the Right IT Compliance and Certification Services
Achieving compliance doesn’t have to feel like climbing Mount Everest in flip-flops. The good news? Modern tools, platforms, and expert partners have completely transformed what used to be a grueling solo journey into a strategic advantage. At Kraft Business Systems, we’ve seen how the right approach to IT compliance and certification services can turn what feels like an impossible mountain into a manageable hill.
The secret isn’t working harder – it’s working smarter with the right team and technology on your side.
The Role of Cloud Providers and Security Platforms
Think of cloud providers as your compliance foundation. They’ve already done much of the heavy lifting, operating under what’s called a shared responsibility model. Essentially, they handle the security of the cloud infrastructure, while you focus on security in the cloud for your specific applications and data.
Major cloud platforms maintain compliance with an impressive array of standards – ISO certifications, PCI DSS, SOC reports, FedRAMP, HIPAA, and CMMC requirements. This means you’re building on a foundation that’s already been rigorously tested and validated. It’s like starting a house with professionally poured concrete instead of mixing your own cement.
But the real game-changer comes from specialized security platforms that work alongside your cloud infrastructure. These platforms provide externally validated and accredited solutions specifically designed to help you meet regulatory requirements. For instance, modern endpoint security solutions can address significant portions of various compliance frameworks – supporting multiple CMMC 2.0 requirements, helping with HIPAA technical safeguards, and covering numerous NIST control families.
The beauty of this approach? You’re not reinventing the wheel. These platforms have been through thousands of audits and serve thousands of clients globally. They’ve earned certifications like FedRAMP High authorization and accreditations from agencies like the NSA, which means they’ve already proven their worth in the most demanding environments.
The Rise of Compliance Automation
Remember the days of drowning in spreadsheets and chasing down evidence in email threads? Those days are rapidly becoming a distant memory thanks to compliance automation platforms.
These modern solutions tackle the most time-consuming aspects of IT compliance and certification services by automating repetitive tasks like evidence collection and tracking. Instead of manually gathering screenshots and documents every few months, the system continuously monitors your environment and automatically collects the proof you need.
Real-time gap identification is perhaps the most valuable feature. Rather than finding compliance issues during an audit (when it’s too late and expensive to fix), automation platforms flag problems as they occur. This means you can address issues immediately, maintaining continuous audit readiness year-round.
The result? You move from that stressful, last-minute scramble before an audit to a calm, confident state where you’re always ready. It’s the difference between cramming for finals and staying caught up all semester.
These platforms also provide a single source of truth for managing multiple frameworks simultaneously. Instead of juggling separate processes for SOC 2, ISO 27001, and HIPAA, you can manage everything from one dashboard with pre-configured templates and expert guidance built right in.
Leveraging Audit Partners for a Smoother Experience
While automation handles the heavy lifting, experienced audit partners bring something equally valuable: wisdom. The best audit firms don’t just check boxes – they understand your business and help you build a strategic compliance journey that actually strengthens your organization.
Here’s where the magic happens: audit harmonization or “crosswalking.” Experienced partners can take evidence from one certification (like ISO 27001) and apply it to satisfy requirements for another framework (like SOC 2). This approach can save months of work and significant resources by maximizing the value of each piece of evidence you collect.
Quality audit partners also bring technology integration to streamline the entire process. Modern audit management platforms centralize communication, track progress, and organize evidence collection, making the experience far less chaotic than traditional approaches.
But perhaps most importantly, the right audit partner becomes a true collaborator. As one of our clients noted, they’re not just a vendor you direct or who directs you – they’re someone who genuinely cares about your business success. This partnership approach means you get proactive advice and support rather than just compliance checking.
The credibility factor can’t be overlooked either. A high-quality audit from a reputable firm carries significantly more weight with customers, partners, and stakeholders. When you’re competing for business, having recognized certifications from respected audit firms can be the deciding factor.
The combination of automation, cloud-based security platforms, and experienced audit partners transforms compliance from a necessary evil into a competitive advantage. Instead of dreading your next audit, you’ll find yourself confident and prepared – maybe even looking forward to showcasing your security posture.
Staying Ahead: Key Trends and Updates in IT Compliance
The world of IT compliance and certification services never sits still. Just when you think you’ve mastered one framework, new regulations emerge, technologies evolve, and cyberthreats find fresh ways to keep us on our toes. It’s like trying to hit a moving target while riding a rollercoaster – challenging, but not impossible with the right approach.
At Kraft Business Systems, we’ve learned that staying ahead of these changes isn’t just about survival; it’s about turning regulatory evolution into competitive advantage. The organizations that thrive are those that accept change rather than react to it.
The Shift to Continuous Compliance
Remember when compliance meant that frantic scramble once a year? Teams would work nights and weekends, pulling together evidence and documentation while auditors waited impatiently. Those days are becoming ancient history, and frankly, we’re all better for it.
The shift toward continuous compliance represents one of the most significant changes in how organizations approach regulatory requirements. Instead of treating compliance as an annual event, forward-thinking companies are embedding it into their daily operations.
Real-time monitoring has become the new standard. Modern platforms automatically track control effectiveness, flag potential issues, and maintain evidence collection throughout the year. This means no more desperate searches through email chains looking for that one document the auditor requested.
The benefits go far beyond convenience. Proactive risk management allows organizations to identify and address vulnerabilities before they become problems. When your compliance monitoring runs continuously, you catch issues while they’re still small and manageable.
Perhaps most importantly, maintaining audit readiness year-round transforms the entire compliance experience. Instead of dreading audit season, organizations with continuous compliance programs welcome auditors with confidence. They know their controls are working, their documentation is current, and their security posture is strong.
This approach significantly reduces both stress and costs. No more hiring temporary staff for audit preparation, no more paying premium rates for rushed remediation work, and no more sleepless nights wondering if you’ll pass the audit.
The Impact of AI and Emerging Technologies
Artificial Intelligence is reshaping every aspect of business, and compliance is no exception. But here’s the thing about AI – it’s simultaneously making compliance easier and more complicated. It’s like having a incredibly smart assistant who occasionally makes decisions you don’t quite understand.
New risks and opportunities emerge with every AI advancement. These systems can process vast amounts of compliance data, identify patterns humans might miss, and automate routine compliance tasks. However, they also introduce questions about algorithmic bias, data privacy, and decision transparency that didn’t exist just a few years ago.
The emergence of ISO 42001 for AI management signals how seriously the industry takes these challenges. This new standard provides a framework for organizations to manage their AI systems responsibly. We expect to see increasing demand for AI-specific compliance frameworks as more businesses integrate artificial intelligence into their operations.
Securing AI systems requires a different mindset than traditional IT security. These systems learn and adapt, which means their behavior can change over time. Compliance programs must account for this dynamic nature while ensuring consistent security standards.
Future-proofing compliance programs has become essential. Organizations need to build flexibility into their compliance strategies, anticipating how emerging technologies might impact their regulatory obligations. The companies that succeed will be those that view compliance as an adaptive capability rather than a fixed checklist.
Recent Framework Updates You Should Know
The past year has brought significant changes across major compliance frameworks. These updates reflect the evolving threat landscape and the lessons learned from recent cybersecurity incidents.
The CMMC 2.0 final rule became official in October 2024, with mandatory implementation beginning in Spring 2025. This isn’t just another regulatory update – it fundamentally changes how defense contractors approach cybersecurity. Organizations in the Defense Industrial Base need to start their CMMC journey now, not later.
PCI DSS v4.0.1 updates arrived in June 2024, bringing important clarifications to the previous version. While these changes might seem incremental, they address real-world implementation challenges that organizations have faced. The retirement of v4.0 in December 2024 means companies need to transition to the latest version promptly.
FedRAMP’s alignment with NIST SP 800-53 Rev. 5 introduced new controls focused on privacy and supply chain risk management. These updates reflect the increasing sophistication of cyber threats and the need for more comprehensive security measures. Organizations pursuing FedRAMP authorization must account for these improved requirements in their planning.
HITRUST CSF v11 brought selectable compliance factors and updated mappings to authoritative sources. The addition of the AI Security Assessment in November 2024 shows how quickly the healthcare sector is adapting to emerging technologies while maintaining strict security standards.
ISO 27001:2022 restructured its control framework with 11 new controls addressing modern security challenges. Organizations with existing certifications need to understand how these changes impact their current programs.
The proposed HIPAA Security Rule strengthening announced in January 2025 signals the government’s response to increasing cyberattacks on healthcare organizations. These changes will likely require significant updates to existing healthcare compliance programs.
These updates underscore a critical truth: IT compliance and certification services require ongoing attention and expertise. The organizations that partner with knowledgeable providers like Kraft Business Systems are better positioned to steer these changes smoothly and maintain their competitive edge.
Frequently Asked Questions about IT Compliance and Certification Services
If you’re navigating IT compliance and certification services, you probably have questions. We hear these same concerns from business owners in Grand Rapids and across Michigan almost daily. Let’s clear up the confusion with straightforward answers to the most common questions we encounter.
What is the difference between being compliant and being certified?
Think of compliance and certification like the difference between being a good driver and having a driver's license. Compliance means you're actually following the rules - you're adhering to the requirements of laws, regulations, or frameworks like HIPAA, GDPR, or PCI DSS. Your organization has the right policies, procedures, and safeguards in place to protect data and meet regulatory requirements.
Certification, on the other hand, is the formal recognition that proves you're compliant. It's when an independent third party - like an auditing firm - comes in, examines your organization against specific standards (such as ISO 27001 or SOC 2), and issues a certificate that says "Yes, these folks are doing it right."
Here's the interesting part: you can absolutely be compliant without being certified. Many organizations follow HIPAA requirements perfectly but never get a formal HIPAA certification (which doesn't actually exist in the traditional sense). However, certification provides something invaluable - external validation that customers, partners, and stakeholders can trust. It's like having a referee confirm you're playing by the rules.
How long does it take to get a compliance certification?
The honest answer? It depends - and anyone who gives you a one-size-fits-all timeline probably hasn't done this before. We've seen organizations achieve simple certifications in a few months and others spend over a year preparing for complex frameworks like FedRAMP or HITRUST.
Several factors determine your timeline. The certification's complexity plays a huge role. A SOC 2 Type I report might take 3-6 months from start to finish, while SOC 2 Type II requires monitoring your controls for 3-12 months before the audit can even be completed. HITRUST readiness alone can consume up to a year of preparation time.
Your organization's current security maturity is equally important. If you already have solid security policies, documented procedures, and established controls, you're starting the race halfway to the finish line. But if you're building from scratch - which is more common than you might think - expect a longer journey.
Resource allocation makes or breaks timelines. Organizations that dedicate internal teams and work with experienced partners move much faster than those trying to tackle certification as a side project. The size and complexity of your IT environment also matters - a small SaaS company will naturally move faster than a large healthcare system with multiple locations.
The key is realistic planning. We always tell our clients that quality preparation beats rushed execution every time. A well-prepared audit process is smoother, less stressful, and more likely to result in successful certification on the first attempt.
Can I use one audit for multiple certifications?
This is one of our favorite questions because the answer is a resounding yes - and it's exactly the kind of strategic thinking that separates smart organizations from those that burn through compliance budgets unnecessarily.
The magic happens through something called "crosswalking" or "audit harmonization." Experienced audit partners can map controls from different frameworks, allowing you to leverage evidence collected for one certification to satisfy requirements for another. For example, documentation and controls you develop for ISO 27001 can often be reused for SOC 2, HIPAA compliance, or even portions of FedRAMP requirements.
This approach transforms IT compliance and certification services from a series of separate, expensive projects into a coordinated strategy. Instead of undergoing multiple redundant audits that ask similar questions and require similar evidence, you can streamline the entire process. The time savings alone are substantial, but the real benefit is reducing "audit fatigue" - that exhausted feeling your team gets from constantly preparing for the next compliance review.
Here's how it works in practice. Let's say you start with SOC 2 because your customers are demanding it. The security policies, risk assessments, and control documentation you create don't disappear after that audit. A skilled compliance partner can help you map those same materials to ISO 27001 requirements or HIPAA safeguards, significantly reducing the effort needed for additional certifications.
The key is working with audit partners who understand multiple frameworks and have the technology to manage complex, multi-certification programs efficiently. This is where expertise really pays off - both in time savings and in ensuring nothing falls through the cracks.
At Kraft Business Systems, we've seen how this strategic approach can turn compliance from a burden into a competitive advantage. It's not just about checking boxes; it's about building a robust security program that opens doors to new business opportunities while protecting what matters most.
Conclusion
After walking through the complex world of IT compliance and certification services, one thing becomes crystal clear: this isn’t a “set it and forget it” checkbox exercise. It’s an ongoing journey that, when approached strategically, can transform from a necessary burden into one of your business’s most powerful competitive advantages.
Think about it this way: while your competitors are scrambling to meet basic regulatory requirements, you could be leveraging compliance as a trust-building machine that opens doors to new partnerships, federal contracts, and enterprise clients who won’t even consider vendors without proper certifications.
The landscape we’ve explored—from the rigorous demands of FedRAMP and HITRUST to the essential protections of HIPAA and PCI DSS—might seem overwhelming at first glance. But here’s the encouraging truth: you don’t have to tackle everything at once, and you definitely don’t have to go it alone.
The game has changed dramatically in recent years. What used to require armies of consultants and months of painful manual audits can now be streamlined through smart automation platforms, strategic partnerships, and crosswalking approaches that let you knock out multiple certifications with overlapping effort. The shift toward continuous compliance means you’re building a security posture that protects you year-round, not just during audit season.
As AI and emerging technologies continue reshaping the business landscape, staying ahead of trends like continuous monitoring and automated evidence collection isn’t just smart—it’s essential for future-proofing your organization. The frameworks themselves are evolving too, with updates to CMMC 2.0, PCI DSS v4.0.1, and new standards like ISO 42001 for AI management reflecting the realities of modern business.
For businesses throughout Michigan and beyond, having a trusted partner who understands both the technical complexities and the strategic value of compliance makes all the difference. At Kraft Business Systems, we’ve seen how the right approach to IT compliance and certification services can turn regulatory requirements into business enablers that build trust, reduce risk, and fuel growth.
The question isn’t whether you need compliance—it’s whether you’ll approach it as a strategic advantage or a reactive scramble. With the right guidance, tools, and timeline, you can transform this journey from a source of stress into a source of competitive strength.
Ready to simplify your compliance journey? Contact us today.