24/7 Proactive Network Monitoring & Alerts for Michigan Businesses
Today’s businesses depend on reliable networks. When those networks fail, productivity and revenue stop. Continuous, proactive 24/7 network monitoring and alerting is the practical way to keep operations running and sensitive data protected. Below, we explain why always-on monitoring matters, what it covers, and the advantages of a managed approach. We also outline how Kraft Business Systems customizes monitoring programs for Michigan organizations so you can protect your IT infrastructure and keep work moving.
Why 24/7 Proactive Network Monitoring Is Critical to Business Continuity
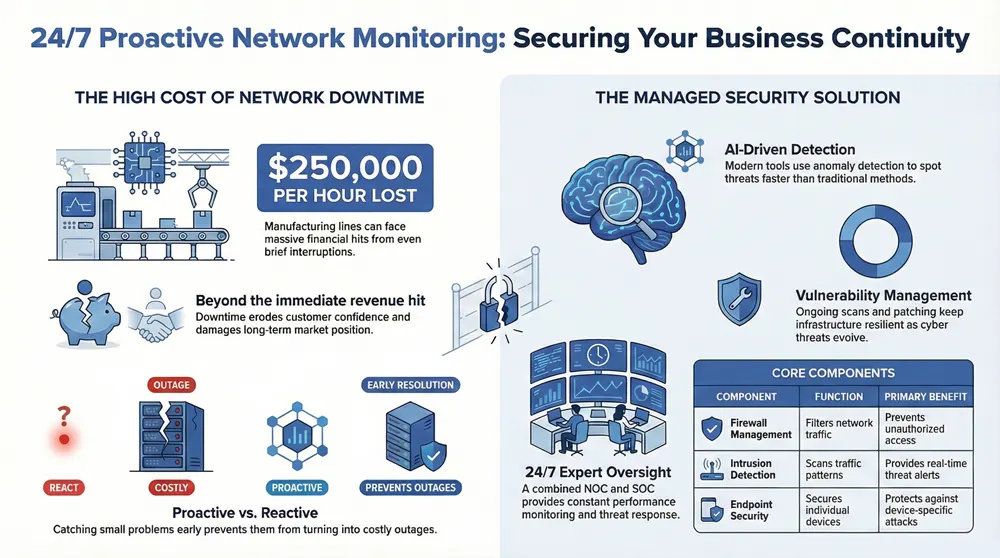
Monitoring your network around the clock means catching small problems before they turn into outages. That early detection lowers the risk of costly downtime, preserves customer trust, and prevents interruptions to everyday operations. With downtime costs high across industries, proactive monitoring is a core part of keeping your business resilient.
Proactive monitoring is widely recognized as a foundational practice in business continuity planning.
Proactive IT Monitoring for Business Continuity
One of the core elements of business continuity planning is proactive — or intelligent — monitoring, which helps organizations avoid unexpected outages and respond faster to issues.
Proactive IT/IS monitoring for business continuity planning, S Šimonová, 2011
What are the costs and impacts of network downtime?
The costs add up quickly. Depending on the industry, downtime can run into thousands per minute. For example, a halted manufacturing line can lose roughly $250,000 an hour, and a retail operation can suffer immediate revenue losses from interrupted sales. Beyond the immediate hit, downtime erodes customer confidence and market position — so preventing it protects both operations and reputation over the long term.
What Proactive 24/7 Network Monitoring & Alerting Covers
Proactive 24/7 monitoring means continuously watching network systems for anomalies, threats, and performance degradation. It combines automated detection, performance analysis, and dependable alerting so your IT team — or ours — can act fast. The objective is simple: find issues early and resolve them before your users or business processes are affected.
Whether your systems sit on-site or in the cloud, safeguarding data is essential. Strong cloud security practices help meet compliance requirements and reduce exposure in distributed environments.
How does real-time threat detection and alerting protect your network?
Real-time detection pairs analytics with automated alerts so suspicious activity is flagged the moment it appears. That gives IT teams time to investigate and contain issues before they escalate into breaches or major outages. With clear alerting rules, the right people are notified quickly and can respond in a coordinated way.
Key Benefits of Managed Network Security Solutions
Managed network security solutions strengthen defenses, stabilize costs, and give you access to specialized expertise. Handing monitoring and response to a trusted provider lets your internal team focus on strategic priorities while your infrastructure is protected from evolving threats.
- Enhanced Security: Managed services deliver layered defenses against malware, phishing, data breaches, and other cyber threats.
- Cost Efficiency: Outsourcing reduces hiring and training needs for an in-house security team and avoids large upfront tooling costs.
- Access to Expertise: A managed provider brings specialists who track the latest threats and best practices, so your defenses stay current.
Kraft Business Systems builds managed network security programs tailored to Michigan organizations, combining local experience with proven security practices to keep clients protected.
How Kraft Business Systems Delivers Customized 24/7 Monitoring in Michigan
We combine local, hands-on service with modern tools to deliver monitoring that fits each client. Whether you’re a single-office operation or a multi-site organization across Michigan, we design monitoring and alerting around the systems you rely on.
What tools and AI technologies enhance Kraft’s monitoring services?
Kraft uses a mix of proven monitoring platforms and AI-driven analytics to speed detection and reduce false positives. These tools give us real-time visibility into performance and threats, letting us make proactive recommendations and contain incidents faster to minimize downtime.
Using AI in monitoring follows industry trends toward automated, intelligence-driven threat detection.
AI-Driven Cyber Threat Detection for Real-Time Network Security
AI and machine learning techniques are transforming threat detection by automating intelligence, speeding response, and adapting to new attack methods. These systems use models like deep learning and anomaly detection to spot and respond to threats faster than traditional rule-based tools.
AI-driven cyber threat detection: enhancing security through intelligent engineering systems, 2025
How do Kraft’s local NOC and SOC support rapid issue resolution?
Our Network Operations Center (NOC) monitors performance 24/7 while our Security Operations Center (SOC) focuses on threat detection and response. Together they enable quick identification and escalation of incidents, with remediation handled by engineers who understand local business needs and compliance requirements.
Which Managed Network Security Components Are Included in 24/7 Monitoring?
A complete managed monitoring program combines multiple defenses: firewall oversight, intrusion detection, endpoint protection, and more. Each piece helps reduce risk and keep your environment stable and compliant.
What roles do firewall management, intrusion detection, and endpoint security play?
- Firewall Management: Firewalls enforce network access rules and filter traffic to block unauthorized connections.
- Intrusion Detection: IDS tools scan traffic patterns for suspicious behavior and alert teams to potential intrusions.
- Endpoint Security: Endpoint solutions protect laptops, servers, and devices—closing common attack routes and stopping malware at the source.
How does vulnerability management strengthen IT infrastructure resilience?
Vulnerability management is the ongoing work of finding and fixing known weaknesses. Regular scans, prioritized patching, and configuration hardening lower the chances attackers can exploit systems—keeping your infrastructure more resilient as threats evolve.
Research supports vulnerability management as a proactive strategy for reducing known risks and improving resilience.
Proactive Vulnerability Management for Business Resilience
This review compares risk management, vulnerability management, agility, and resilience, highlighting that proactive vulnerability management focuses on identifying and addressing known issues to better withstand disruptions.
Risk and vulnerability management, project agility and resilience: a comparative analysis, K Rahi, 2021
How Can Michigan Businesses Customize IT Infrastructure Monitoring Plans?
Monitoring shouldn’t be one-size-fits-all. Custom plans let businesses choose the right mix of coverage and support based on systems, size, and budget—especially useful for small and mid-sized organizations with specific operational needs.
What scalable options are available for small and medium-sized businesses?
- Basic Monitoring Packages: Start with core monitoring for mission‑critical systems and scale up as needs grow.
- Advanced Security Solutions: For deeper protection, add advanced detection and automated response features.
- Tailored Support Plans: Pick response times, escalation paths, and service levels that match your operational priorities.
With scalable options, Michigan businesses can balance protection and cost while improving their ability to prevent and recover from incidents.
In short, proactive 24/7 monitoring and alerting are essential for maintaining business continuity in today’s threat landscape. By knowing what to monitor and using managed network security wisely, organizations reduce downtime and protect their data. Contact Kraft Business Systems to discuss a monitoring plan built for your Michigan operations.
Frequently Asked Questions
What types of businesses benefit most from 24/7 network monitoring?
Any business that relies on systems or handles sensitive data benefits from continuous monitoring. It’s especially valuable for finance, healthcare, e‑commerce, and other sectors with strict compliance or heavy online activity. If downtime or data loss would seriously harm your operations, 24/7 monitoring is worth considering.
How can businesses assess their current network security posture?
Start with a security audit: review policies, check configurations, run vulnerability scans and penetration tests, and map critical assets. Security assessment tools and an outside review from a managed provider can reveal gaps you might miss internally.
What are the signs that a business needs to upgrade its network monitoring services?
Watch for frequent outages, slow performance, repeated security incidents, or monitoring tools that don’t deliver timely, actionable alerts. Business growth, new technology adoption, or rising threat levels are also good triggers to upgrade monitoring.
How does employee training factor into network security?
People are still a primary risk. Regular training on phishing, password hygiene, and data handling reduces human error and complements technical controls. A security-aware team makes monitoring and response far more effective.
What role does incident response play in network monitoring?
Monitoring identifies problems; incident response defines the next steps. A clear response plan — who acts, how incidents are contained, and how recovery proceeds — helps teams resolve events faster and with less business impact.
Can small businesses afford 24/7 network monitoring services?
Yes. Scalable plans and flexible pricing make continuous monitoring accessible for small businesses. The investment often pays for itself by preventing costly downtime and breaches while giving owners greater peace of mind.
Conclusion
Proactive 24/7 monitoring and alerting are practical, necessary steps to protect Michigan businesses from disruption. With a customized monitoring plan, you strengthen security, reduce downtime, and free your team to focus on the work that grows your business. Reach out to Kraft Business Systems to design a monitoring approach that fits your needs.