Best practices for database application security are essential for protecting your business from the growing threat of data breaches and cyberattacks. Database security combines tools, controls, and policies that protect your data, database management systems, and supporting infrastructure from unauthorized access, corruption, and attacks.
Essential database security practices include:
- Physical security – Secure data centers with locks, cameras, and access controls
- Network segmentation – Separate database servers from web servers and public networks
- Strong authentication – Multi-factor authentication (MFA) and role-based access control
- Data encryption – Encrypt data at rest and in transit using TLS and database encryption
- Regular patching – Keep database software and systems updated with security patches
- Access monitoring – Log all database activity and monitor for suspicious behavior
- Secure backups – Encrypt backups and test recovery procedures regularly
- Vulnerability testing – Conduct regular security assessments and penetration tests
The stakes have never been higher. Statista shows data compromises nearly doubled from 1,802 to 3,205 between consecutive years, while human error causes nearly half (49%) of all reported data breaches. A single breach can result in massive financial losses, legal penalties, and permanent damage to your reputation.
Database security protects three critical elements: confidentiality (keeping sensitive data private), integrity (ensuring data accuracy and preventing unauthorized changes), and availability (maintaining system uptime and access for legitimate users).
Database security is not just a technical concern – it’s a business-critical priority that affects every aspect of your operations.
Best practices for database application security word roundup:
Identifying and Mitigating Common Database Threats
Think of database security as a chess game where you’re constantly anticipating your opponent’s next move. Cybercriminals are always refining their tactics, and since databases hold the crown jewels of sensitive information, they’ve become the ultimate prize. The good news? Once you understand their playbook, you can stay several moves ahead.
SQL Injection remains the heavyweight champion of database attacks. This sneaky technique involves slipping malicious SQL code into input fields, essentially tricking your database into running commands it was never meant to execute. The famous “Bobby Tables” comic from bobby-tables.com perfectly captures how a simple input field can become a digital wrecking ball. Best practices for database application security always start with addressing this fundamental vulnerability through query parameterization and rigorous input validation.
Credential theft has become alarmingly common, with stolen or weak passwords serving as the front door for most attacks. When 67% of data breaches stem from compromised credentials, it’s clear that traditional password protection isn’t cutting it anymore. Strong authentication paired with Multi-Factor Authentication (MFA) creates multiple barriers that make attackers work much harder for access.
Insider threats present a particularly complex challenge because they come from within your own organization. Whether it’s a disgruntled employee with malicious intent or someone who accidentally misconfigures a system, internal risks require a different approach. Insider Threat Detection becomes crucial when you consider that human error accounts for nearly half of all reported data breaches.
Malware continues to evolve, with new variants designed specifically to target database environments. These digital parasites can steal data, disrupt operations, or hold your entire system hostage through ransomware. Advanced anti-malware solutions and regular security scans help keep these threats at bay.
Unpatched software vulnerabilities create an open invitation for attackers who actively scan for known security holes. Research reveals that 88% of codebases contain outdated software components, making regular patching absolutely essential. A strict update schedule ensures that known vulnerabilities don’t become your downfall.
Denial of Service (DoS) attacks might not steal your data, but they can cripple your operations by making database services unavailable. These attacks cause significant operational disruption and financial losses, making query optimization and rate limiting important defensive measures.
Physical attacks often get overlooked in our digital-first world, but physical access to database servers can bypass every digital security control you’ve implemented. Stringent physical security measures for data centers, including restricted access and surveillance, provide essential protection.
Top 5 Database Security Threats and Mitigation Strategies:
- SQL Injection – Use parameterized queries and input validation
- Credential Theft – Implement MFA and strong password policies
- Insider Threats – Apply least privilege principles and conduct regular access reviews
- Unpatched Vulnerabilities – Maintain strict patching schedules
- Exposed Databases – Implement network segmentation and proper firewall configuration
Understanding these threats transforms you from a reactive defender into a proactive security strategist. Each vulnerability represents an opportunity to strengthen your defenses and stay ahead of potential attackers. For a comprehensive overview of security challenges, explore Most Common Cybersecurity Threats to deepen your understanding of the broader threat landscape.
Database Security Best Practices: Stay Several Moves Ahead
A Deep Dive into Best Practices for Database Application Security
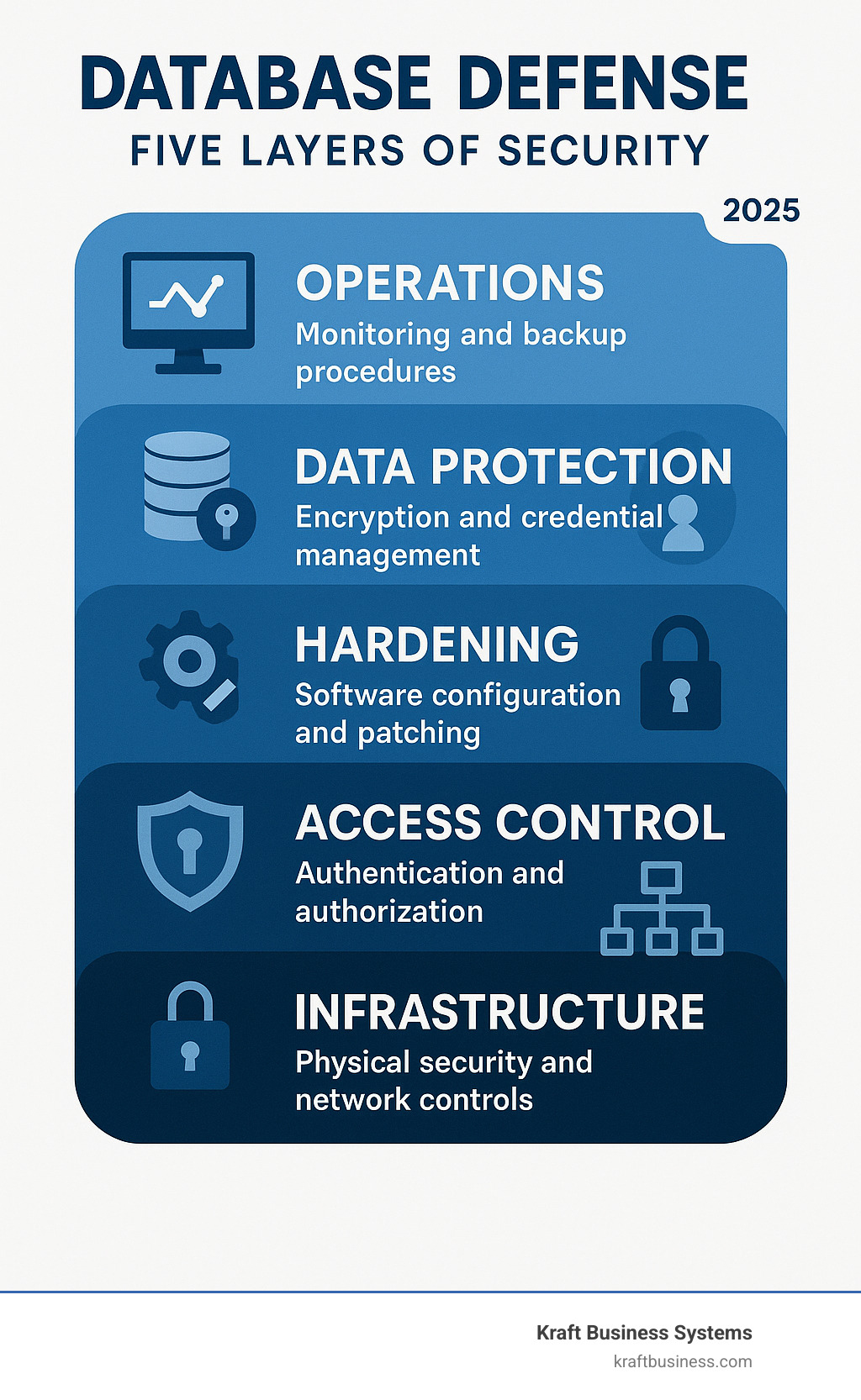
Think of database security like building a fortress. You wouldn’t rely on just a strong front gate – you’d want multiple layers of defense, from the outer walls to the inner keep. Best practices for database application security follow this same principle, creating a comprehensive defense-in-depth strategy that protects your valuable data at every level.
When one security layer fails (and eventually, something will), the others step in to prevent a complete breach. This multi-layered approach addresses everything from the physical infrastructure housing your servers to the code running your applications.
Secure the Foundation: Infrastructure and Network Controls
Your database security is only as strong as the foundation it sits on. The physical and network environments supporting your databases form the bedrock of your entire security posture. Even the most sophisticated software protections can crumble if the underlying infrastructure is compromised.
Physical security might seem old-fashioned, but it’s absolutely critical. If an attacker can physically access your server, they can bypass most digital controls entirely. We ensure database servers are housed in secured, locked environments with cameras, security staff, and detailed access logs. Our data centers in Grand Rapids, MI, and across Michigan follow stringent physical security standards because we know that a locked door can be just as important as a firewall.
Server separation creates vital barriers between your database and potential attackers. We never place database servers alongside web servers or other public-facing components. This separation means that even if your website gets compromised, the attacker still faces significant problems to reach your actual data. It’s like having multiple locked doors between the street and your most valuable possessions.
Network segmentation and firewalls act as your digital moat. We place database servers behind robust firewalls configured with “deny-all” rules by default. This means only explicitly approved traffic can reach your database – typically just your application servers, never direct client connections. We regularly review these firewall rules to prevent configuration drift, which is when security settings gradually weaken over time without anyone noticing.
Proxy servers add another protective layer by ensuring all data transmission between your application and database stays encrypted through HTTPS. Even if your application server gets compromised, the data flowing to and from your database remains protected. It’s an extra insurance policy that costs little but provides significant protection.
Avoiding default network ports makes your database harder to find and target. While attackers can still find non-standard ports, using them instead of defaults (like 3306 for MySQL or 1433 for SQL Server) deters basic automated attacks. Think of it like not putting your house number on the mailbox – it won’t stop a determined burglar, but it makes casual troublemakers move on to easier targets.
Cloud security considerations require understanding the shared responsibility model. Your cloud provider secures the underlying infrastructure, but you’re responsible for securing the data, configurations, and access controls within your database. It’s like renting an apartment in a secure building – the landlord provides the locks and security guards, but you still need to lock your own door. Our expertise in Cloud Security for Businesses helps steer these shared responsibilities effectively.
We also implement comprehensive Network Security Best Practices to ensure your entire network infrastructure supports your database security goals.
Harden the Core: Database Software and Configuration
Database hardening is like reinforcing the walls of your fortress. It involves strengthening your database system to make it more resistant to attacks by reducing the “attack surface” – essentially, fewer doors and windows for attackers to try.
Operating system hardening starts with the foundation beneath your database. We secure the underlying OS using established baselines like CIS Benchmarks, which provide detailed security configuration guidelines. This involves removing unnecessary services, securing system files, and configuring the OS for maximum security. A compromised operating system can undermine even the most secure database configuration.
Removing default accounts and databases eliminates well-known entry points. Database systems often ship with default accounts like ‘root’ or ‘sa’ and sample databases that attackers know about. We remove or disable these entirely, or at minimum, change their passwords to strong, unique ones. It’s like changing the locks when you move into a new house – you don’t know who else might have keys.
Disabling unnecessary services reduces potential attack vectors. Database software often includes features and services you don’t actually need. Each active service represents a potential entry point for attackers. We systematically disable unused database services and functions, keeping only what’s essential for your application to function properly.
Timely patching and updates represent one of your most critical defenses. Software vulnerabilities are finded constantly, and vendors release patches to fix them. Unfortunately, research shows that 88% of codebases contain outdated software components, leaving systems exposed to known attacks. We maintain rigorous patching schedules, ensuring all database software, drivers, and related components stay current with the latest security updates.
Principle of least privilege for service accounts limits potential damage if a service gets compromised. Database services should run under accounts with only the minimum permissions needed to function. If an attacker compromises a service account, the damage they can inflict is limited to only what that account can access. We configure database service accounts with minimal privileges, restricting them to specific hosts and databases.
Specific hardening guides address the unique security considerations of different database systems. Microsoft SQL Server requires disabling features like xp_cmdshell and CLR execution. MySQL and MariaDB benefit from running the mysql_secure_installation script. PostgreSQL, MongoDB, and Redis each have their own specific hardening requirements. We apply these database-specific security measures systematically, using Database Vulnerability Assessment Tools to identify and address configuration weaknesses.
Control Access: Authentication and Authorization
Controlling who can access your database and what they can do once inside forms the heart of your security strategy. This goes far beyond simple passwords – it’s about creating a comprehensive system for managing identities and permissions.
Strong authentication provides your first line of defense against unauthorized access. We enforce strong, unique passwords for all database accounts, but passwords alone aren’t enough anymore. Multi-Factor Authentication (MFA) adds a crucial second layer of security, requiring users to provide additional verification beyond just their password. Given that 67% of data breaches result from compromised credentials, MFA has become essential rather than optional. We also consider restricting access to validated IP addresses for an additional layer of control.
Role-Based Access Control (RBAC) simplifies permission management while improving security. Instead of assigning permissions to individual users, we manage them through roles or groups. A ‘read-only’ role might only have SELECT permissions, while an ‘admin’ role would have broader privileges. This systematic approach reduces the risk of misconfigurations and makes it easier to maintain consistent security policies across your organization.
Principle of least privilege ensures users and applications only get the minimum permissions necessary to perform their required tasks. A microservice designed to read customer data shouldn’t have the ability to delete financial records. We vigilantly enforce this principle, regularly reviewing and fine-tuning permissions to prevent accounts from accumulating unnecessary privileges over time.
Privileged Access Management (PAM) provides improved control for highly sensitive administrative accounts. These systems monitor and audit privileged sessions, ensuring that only authorized personnel can access critical database functions under controlled conditions. It’s like having a security guard who not only checks IDs but also watches what people do once they’re inside.
Continuously revoking privileges combats “privilege creep” – the common problem where users accumulate more permissions over time than they actually need. We regularly review and remove unnecessary access, especially when employees change roles or leave the organization. This proactive management prevents former employees from retaining access and reduces the risk of over-privileged accounts.
Secure user account management extends beyond initial setup to include clear policies for the entire account lifecycle. We establish procedures for deactivating accounts when employees change roles or leave the company. We also implement automatic account locking after failed login attempts to deter brute-force attacks. Our comprehensive Identity and Access Management Solutions provide the tools and policies needed for effective access control.
Protect the Data Itself: Encryption and Credential Management
Even with robust infrastructure and access controls, protecting the data itself represents your final and most critical line of defense. Encryption renders data unreadable to unauthorized parties, while secure credential management prevents attackers from gaining initial access in the first place.
Encryption in transit protects data as it travels across networks. We encrypt all database connections using Transport Layer Security (TLSv1.2 or higher) with modern ciphers like AES-GCM or ChaCha20. This ensures that any data exchanged between your application and database – including login credentials – remains confidential and protected from eavesdropping. We also configure client applications to verify database server certificates, preventing man-in-the-middle attacks where attackers impersonate your database server.
Encryption at rest protects stored data even if the underlying storage gets compromised. We use various methods including disk encryption, Transparent Data Encryption (TDE) provided by database management systems, and column-level encryption for highly sensitive data fields. This means that if an attacker somehow gains access to your database files, the data itself remains encrypted and unintelligible without the proper decryption keys.
Secure credential storage addresses one of the most common security vulnerabilities. We never hardcode database credentials directly into application code or store them in source code repositories. Instead, we use configuration files located outside the web root with appropriate read-only permissions, or better yet, dedicated secrets management tools like HashiCorp Vault or cloud provider secret managers. The principle is simple: if your server needs credentials to function, it must have them, but we focus on rapid intrusion detection and limiting potential damage.
Data masking and tokenization protect sensitive information in non-production environments. We never use real sensitive data for development or testing. Instead, we employ data masking or tokenization techniques to replace sensitive information with realistic but non-sensitive data. This ensures that even if a test environment gets breached, no actual sensitive data is compromised. This approach is fundamental to maintaining Database Privacy.
Key management ensures that encryption remains effective over time. Encryption is only as strong as its key management procedures. We implement secure key management that properly stores, rotates, and backs up encryption keys. Multiple authorized personnel must have access to decrypt data, with appropriate approval from data owners. This comprehensive approach helps maintain Database Confidentiality.
Understanding the relationship between these concepts helps create more effective security strategies. For a deeper exploration of how these elements work together, check out Comparing Data Privacy vs Data Security.
Database Security Best Practices: Stay Several Moves Ahead
Integrating Security into Your Operations and Development Lifecycle
Security isn’t something you set up once and forget about. It’s like tending a garden – it requires constant attention, regular maintenance, and ongoing care to flourish. The most effective best practices for database application security weave protection seamlessly into every aspect of your operations and development processes.
Shift Left: Adopting best practices for database application security in your SDLC
The best time to fix a security vulnerability is before it ever reaches production. This approach, called “shifting left,” means building security into your Software Development Lifecycle (SDLC) from the very beginning. It’s much easier (and cheaper) to prevent problems than to fix them later.
Secure coding practices form the foundation of this approach. We train our developers to write code that’s secure by design, focusing on the most common database vulnerabilities. Query parameterization is our golden rule for preventing SQL injection – instead of mixing user input directly into SQL queries, we treat all input as data, not executable code. It’s like having a bouncer at the door who checks everyone’s ID before letting them into the club.
Input validation and output encoding work together to ensure that all external input meets our expectations and that any data displayed to users is rendered safely. Think of it as quality control for your data pipeline – nothing gets through without proper inspection.
We never allow developers to hardcode database credentials or other sensitive secrets directly into their code. Instead, we use environment variables or dedicated secrets management services to securely provide credentials to applications at runtime. This prevents the embarrassing situation where someone accidentally commits passwords to a public code repository.
Automated security testing catches problems before they can cause real damage. We integrate Static Application Security Testing (SAST) tools into our development pipelines to analyze source code for vulnerabilities before the application even runs. Software Composition Analysis (SCA) tools help us identify outdated or vulnerable open-source components – crucial since 88% of codebases contain outdated software components.
Separating test and production environments is non-negotiable. Our development, staging, and production environments are completely distinct, with different credentials, roles, and access controls. Test environments use synthetic or anonymized data, never real production information. This way, if a test environment gets compromised, no actual sensitive data is at risk. Our Cybersecurity Solutions help implement these practices effectively.
Maintain Vigilance: Continuous Monitoring and Auditing
Even with the best preventative measures, threats can still emerge. Continuous monitoring is like having a security guard who never sleeps – always watching for suspicious activity and ready to sound the alarm.
Database Activity Monitoring (DAM) solutions track every interaction with your database in real-time. We monitor user logins, queries executed, data accessed, and changes made. This comprehensive logging creates a detailed audit trail that’s invaluable for both security and compliance purposes.
We ensure that all successful and unsuccessful logins, as well as operations on sensitive data, are logged and stored securely for at least one year. These logs integrate seamlessly with our Security Information and Event Management (SIEM) system, which centralizes security data from across your entire IT environment.
Regular log reviews by knowledgeable, independent individuals help identify unusual or risky behavior patterns. We configure automatic notifications to security administrators for critical events like locked accounts due to failed logins or unauthorized access attempts. This proactive approach means potential threats are identified and addressed quickly.
Automated alerting for suspicious activity – such as numerous failed login attempts, unusual data access patterns, or unexpected database modifications – ensures our security team receives immediate notification. We can even conduct a Dark Web Scan to identify if your credentials have been compromised externally. Our IT Security Audit Services include thorough log analysis to keep your systems secure.
Plan for the Worst: Secure Backups and Recovery
Hope for the best, but plan for the worst. A comprehensive security strategy isn’t complete without a robust backup and recovery plan. Data breaches and system failures can happen to anyone, and your ability to restore data quickly and completely is what separates a minor inconvenience from a business catastrophe.
We follow the industry-standard 3-2-1 backup rule: keep three copies of your data, store backups on at least two different types of media, and keep at least one copy offsite and offline. This approach ensures that even if multiple systems fail simultaneously, your data remains safe and recoverable.
Encrypting backups is just as important as encrypting your primary database. Your backups contain the same valuable data, so they need the same stringent protection. We ensure all database backups are stored in encrypted format, with decryption keys securely managed and stored separately from the backups themselves.
Testing backup integrity regularly is crucial – it’s not enough to just make backups. We periodically test our backup and recovery procedures to verify they work correctly and meet defined recovery benchmarks. This aligns with CIS Control 11: Data Recovery and ensures that when disaster strikes, we can restore operations quickly and efficiently.
We carefully document all backup and recovery procedures, including retention intervals and key management. This documentation ensures that during a crisis, our team can efficiently restore operations without confusion or delays. Our Data Backup and Recovery: A Comprehensive Guide provides comprehensive details on these critical processes.
Validate Your Defenses: A key component of best practices for database application security
No security measure is perfect, and the threat landscape constantly evolves. Regularly testing your defenses helps identify weaknesses before attackers do. It’s like stress-testing a bridge before opening it to traffic – you want to know how it performs under pressure.
Vulnerability assessments involve regular scans of our database systems and applications to identify known security flaws, misconfigurations, and outdated components. These assessments provide a snapshot of potential weaknesses that need attention.
Penetration testing goes beyond automated scans by simulating real-world attacks. Ethical hackers attempt to exploit vulnerabilities to gain unauthorized access to your databases, providing valuable insights into how your systems would perform against actual threats. These tests often uncover complex vulnerabilities that automated tools might miss.
Regular security reviews of database configurations, access controls, and security policies ensure they align with current best practices for database application security and organizational requirements. The security landscape changes rapidly, and what was secure yesterday might not be secure tomorrow.
Most importantly, we don’t just identify problems – we fix them. Findings from vulnerability assessments and penetration tests are used to prioritize and implement remediation actions. This iterative process of testing, identifying, and fixing weaknesses continuously improves your database application security posture.
We also provide Cybersecurity Training for Employees to strengthen your human firewall and offer Data Breach Prevention Tips to further fortify your defenses. Our Cybersecurity Risk Assessment can help you understand your current vulnerabilities and create a roadmap for improvement.
Database Security Best Practices: Stay Several Moves Ahead
Frequently Asked Questions about Database Application Security
We get a lot of questions about database security from businesses just like yours. Let me address the most common concerns that come up in our conversations with clients.
What is the most common database security vulnerability?
SQL Injection (SQLi) takes the crown as the most persistent and dangerous database vulnerability we see. It’s surprisingly easy for attackers to exploit, and the damage can be devastating – complete data theft, unauthorized modifications, or even total data destruction.
The attack works by tricking your database into executing malicious commands. Attackers simply inject code through input fields in your web applications or APIs. Think of it like the famous “Bobby Tables” comic – improper input handling can literally drop your entire database.
The good news? SQL injection is completely preventable with proper coding practices. Parameterized queries are your best friend here – they treat all user input as data, never as executable code. Input validation adds another layer of protection by ensuring only expected data formats reach your database. Stored procedures can help too, though they’re not bulletproof if built incorrectly.
These prevention methods are core components of best practices for database application security, and they should be non-negotiable in your development process.
How does the cloud impact database security?
Cloud computing introduces what we call the “shared responsibility model” – basically, security becomes a partnership between you and your cloud provider. Understanding who’s responsible for what is crucial.
Your cloud provider handles the infrastructure side – the physical data centers, network hardware, virtualization layers, and the underlying database services themselves. They’re securing the foundation, but that’s where their responsibility ends.
You’re responsible for everything above that layer. This includes your data, configurations, access controls, network settings like firewalls and VPCs, encryption key management, and application-level security. If you accidentally misconfigure a security group and expose your database to the internet, that’s on you, not your cloud provider.
The cloud makes deploying databases incredibly easy, but that same ease can lead to dangerous misconfigurations. We’ve seen databases accidentally exposed because someone clicked the wrong checkbox during setup. That’s why robust configuration management and continuous monitoring are essential when you move to the cloud.
Is encryption a complete solution for database security?
While encryption is absolutely critical, it’s not a magic bullet that solves all your database security problems. Think of it as one essential layer in your security cake, not the entire dessert.
Encryption protects your data from prying eyes, both when it’s stored and when it’s moving across networks. But it won’t stop an authorized user from misusing data. If an attacker steals legitimate credentials through phishing and logs into your database, the data gets decrypted for them automatically. Encryption can’t tell the difference between a legitimate user and an attacker using stolen credentials.
Key management is another challenge. Encryption is only as strong as how you protect those encryption keys. If your keys get compromised, your encrypted data becomes an open book.
Encryption also doesn’t protect against other common threats like SQL injection, unpatched software vulnerabilities, or insider threats from employees who already have legitimate access to your data.
That’s why we always recommend a defense-in-depth approach. Encryption works beautifully alongside strong authentication, least privilege access controls, network segmentation, regular patching, and continuous monitoring. It’s like building a vault – you need the strong walls, the alarm system, the locked door, AND the secure box inside. Each layer makes the others more effective.
Conclusion: Building a Resilient Database Security Strategy
Think of database security like protecting your home – you wouldn’t rely on just one lock on the front door. You’d want security cameras, an alarm system, motion sensors, and maybe even a guard dog. The same principle applies to your database applications.
The best practices for database application security we’ve explored work together as a comprehensive defense system. Each layer – from securing your physical infrastructure and network controls to hardening your database software, controlling access with strong authentication, and protecting data through encryption – serves a specific purpose in your overall security strategy.
Security isn’t a “set it and forget it” solution. It’s an ongoing process that requires vigilance, regular testing, and continuous improvement. Cyber threats are constantly evolving, which means your defenses need to evolve too. The good news? You don’t have to tackle this alone.
Taking a proactive approach means staying ahead of threats rather than scrambling to respond after an attack. It means integrating security into your development lifecycle from day one, monitoring your systems continuously, and regularly testing your defenses to identify weaknesses before attackers do.
We know that implementing these security measures can feel overwhelming, especially when you’re trying to run a business. That’s where having the right partner makes all the difference. Our team at Kraft Business Systems brings decades of experience helping businesses in Grand Rapids and across Michigan build robust security frameworks that actually work.
Defense-in-depth isn’t just a buzzword – it’s a proven strategy that acknowledges no single security measure is perfect. By layering multiple controls and continuously monitoring their effectiveness, you create a security posture that can withstand even sophisticated attacks.
The cost of prevention is always less than the cost of a breach. Whether it’s financial losses, regulatory penalties, or damage to your reputation, the consequences of inadequate database security can be devastating to your business.
For expert guidance in implementing a robust security framework for your database applications, explore our Managed Cybersecurity Services. We’re here to help you build a resilient security posture that protects your most valuable assets while allowing your business to thrive.