AI Overview:
An IT compliance assessment is a structured evaluation of your organization’s technology systems, policies, and procedures to verify they align with industry regulations and data protection standards. It ensures you meet frameworks such as HIPAA, PCI DSS, GDPR, SOC 2, and ISO 27001, helping prevent costly fines, breaches, and reputational damage.
Think of it as a health check for your IT infrastructure—a diagnostic process that reveals weaknesses, verifies your defenses, and strengthens your security posture.
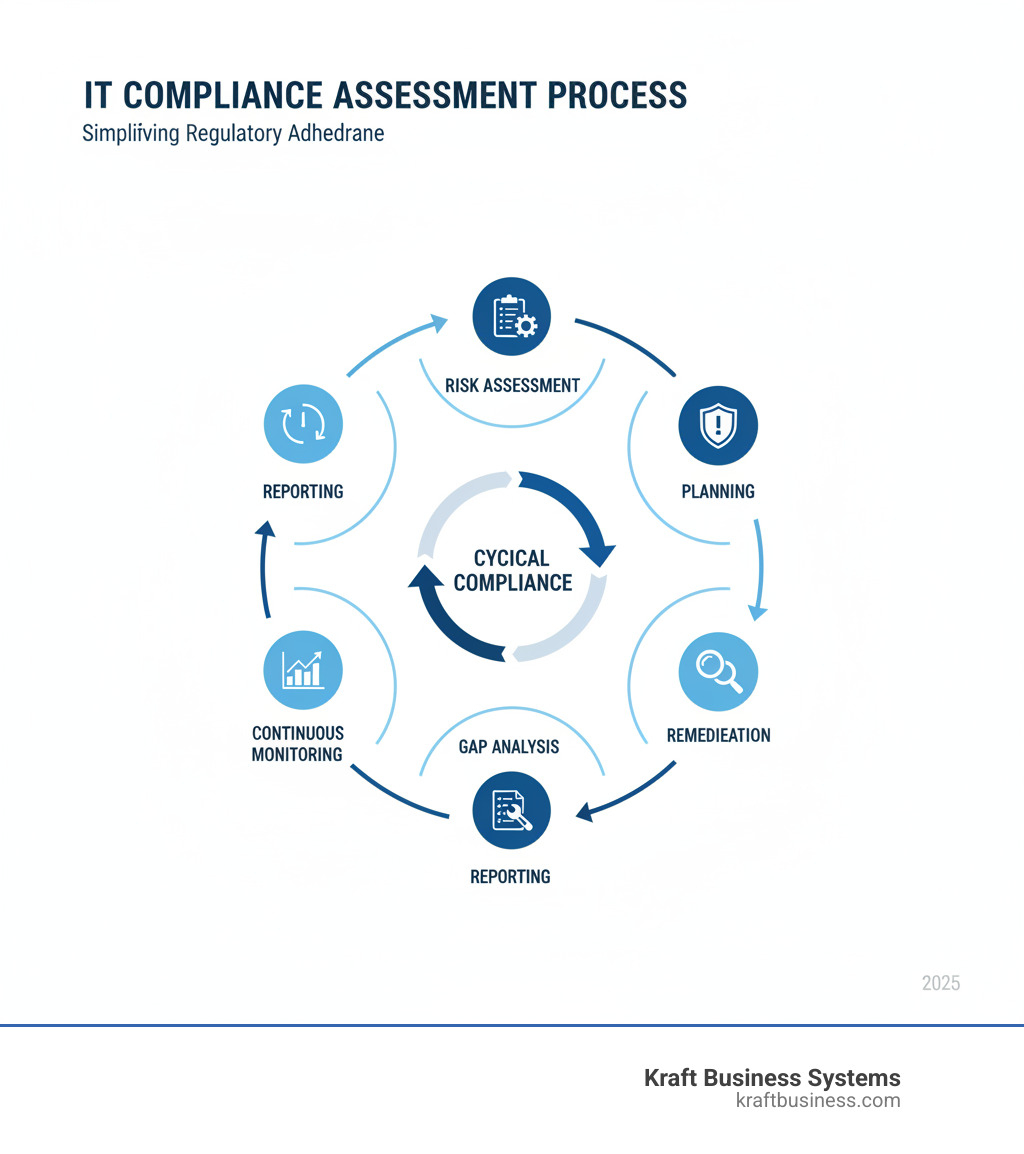
IT Compliance Assessment: 6 Easy Steps
Why IT Compliance Assessment Is Your Business’s Safety Net
An IT compliance assessment is a systematic evaluation of your organization’s technology systems, policies, and procedures to ensure they meet regulatory requirements and industry standards. This process identifies gaps in your current security posture and provides a roadmap for maintaining compliance with frameworks like HIPAA, PCI DSS, or GDPR.
Quick Overview of IT Compliance Assessment:
- What it is: Independent review of IT systems against regulatory standards
- Primary objectives: Verify data security, ensure regulatory adherence, improve governance
- Key benefits: Avoid fines, build customer trust, strengthen security posture
- Frequency: Annually or after major IT changes
- Types: ITGC audits, cybersecurity audits, regulatory compliance audits
Picture yourself walking through a factory with visible safety protocols – that’s compliance in action. But IT compliance operates behind the scenes, making it harder to visualize yet equally critical for your business operations.
With cyber threats occurring every 39 seconds and data breach costs averaging $4.88 million, a proactive IT compliance assessment isn’t just about checking boxes. It’s about protecting your business from devastating financial losses and reputational damage.
The challenge? Many mid-sized businesses view compliance assessments as overwhelming technical exercises. The reality is simpler – with the right approach, you can turn this complex process into a manageable project that strengthens your entire organization.
Whether you’re preparing for your first assessment or looking to streamline your existing process, understanding the fundamentals will help you steer this critical business requirement with confidence.
It compliance assessment word roundup:
What is an IT Compliance Assessment (and Why Bother)?
Think of an IT compliance assessment as a comprehensive health check for your business’s digital nervous system. Just like you wouldn’t skip your annual physical, your technology infrastructure needs regular examinations to ensure it’s operating safely and legally.
At its heart, an IT compliance assessment is a systematic review that verifies your organization’s technology systems, policies, and procedures meet regulatory requirements and industry standards. It’s not just about ticking boxes – it’s about creating a secure foundation that protects your business from costly mistakes and builds trust with your customers.
Here’s where things get interesting: many business owners confuse IT security with IT compliance, but they’re actually complementary partners in your business protection strategy. IT security focuses on the technical tools and practices that defend against cyber threats – think firewalls, encryption, and multi-factor authentication. IT compliance, on the other hand, ensures you’re following the specific rules and regulations that govern your industry, like GDPR for data privacy or HIPAA for healthcare information.
Imagine IT security as the locks on your doors and compliance as making sure those locks meet building code requirements. You need both to truly protect your business.
This relationship fits within what we call Governance, Risk, and Compliance (GRC) – a framework that helps organizations make smart decisions about managing risks and following rules. When these three elements work together, they create a robust shield around your business operations.
Why Should You Care About IT Compliance?
The numbers tell a sobering story. Cyber threats strike every 39 seconds, and the cost of non-compliance can range from $14 million to nearly $40 million according to a study on the cost of non-compliance. That’s not just fines – it includes legal fees, operational chaos, and the devastating impact of lost customer trust.
Data breaches have reached an all-time high cost of $4.88 million on average, representing a 10% increase from the previous year. For businesses across Michigan, from small Grand Rapids startups to established Detroit enterprises, these aren’t just statistics – they represent real threats that could shut down operations overnight.
But here’s the encouraging news: proactive risk management through regular compliance assessments transforms these overwhelming threats into manageable challenges. Instead of playing defense after a problem occurs, you’re building strength from the ground up.
Key Objectives and Benefits
An effective IT compliance assessment serves several critical purposes that directly impact your bottom line. Data security verification ensures your sensitive information stays protected through proper encryption, access controls, and monitoring systems. Regulatory adherence keeps you aligned with laws like HIPAA, PCI DSS, or GDPR, depending on your industry and customer base.
Governance improvement aligns your IT processes with your business goals, while risk identification spots potential vulnerabilities before they become expensive problems. Think of it as finding and fixing small leaks before your roof caves in.
The benefits extend far beyond avoiding penalties. Improved credibility with customers and partners opens doors to new opportunities, while operational efficiency often improves as streamlined, compliant processes eliminate redundancies and confusion.
Industries that particularly need robust IT compliance include healthcare organizations handling patient data, finance companies managing sensitive financial information, e-commerce businesses processing payments, government contractors working with classified information, and SaaS companies storing customer data in the cloud.
Categories of IT Compliance Audits
Different businesses need different types of assessments, much like different vehicles need different maintenance schedules. IT General Controls (ITGC) audits examine the foundational elements – how you manage access to programs and data, how you develop and change systems, and how reliable your financial reporting systems are.
Cybersecurity audits dive deep into your defenses against digital threats, evaluating everything from firewalls to encryption protocols. Regulatory audits focus on specific industry requirements, ensuring you meet the exact standards that apply to your business sector.
Governance audits assess how well your IT strategy aligns with your business goals, while third-party vendor audits examine the security practices of your external partners – because their vulnerabilities can become your problems. Disaster recovery audits test your ability to bounce back from IT disruptions, ensuring your backup systems and recovery plans actually work when you need them most.
Each type of audit plays a vital role in creating a comprehensive compliance program that protects your business from multiple angles, giving you confidence that your digital infrastructure can support your growth ambitions safely and legally.
The 6-Step IT Compliance Assessment Process
Conducting an IT compliance assessment doesn’t have to feel like climbing Mount Everest in business attire. While the process might seem overwhelming at first glance, breaking it down into six manageable steps transforms this critical business requirement into a structured project that your team can tackle with confidence.
Think of it like renovating your home – you wouldn’t start tearing down walls without a blueprint, and you certainly wouldn’t want to find structural issues after you’ve already hung the drywall. The same logic applies to compliance assessments. By following a systematic approach, you’ll identify issues early, address them efficiently, and build a stronger foundation for your business operations.
Step 1: Plan and Scope Your IT Compliance Assessment
Every successful IT compliance assessment begins with crystal-clear planning. This isn’t the time to wing it – we need a roadmap that guides every decision along the way.
Defining your objectives sets the entire tone for the assessment. Are you preparing for an upcoming external audit? Seeking certification for a specific framework? Or perhaps you’re simply looking to strengthen your overall security posture? Each objective requires a slightly different approach, so clarity here saves countless hours later.
Identifying applicable regulations comes next, and this step often surprises business owners with its complexity. A healthcare practice in Ann Arbor faces different requirements than an e-commerce business in Grand Rapids. Your industry, location, and the type of data you handle all influence which frameworks apply to your situation. HIPAA might be your primary concern if you’re handling patient information, while PCI DSS takes priority if you’re processing credit card payments.
Determining scope requires honest conversations about your IT environment. Will you assess your entire infrastructure, or focus on specific systems that handle sensitive data? The scope decision impacts everything from timeline to resource allocation, so it’s worth getting input from various departments to ensure nothing critical gets overlooked.
Assembling your assessment team means bringing together voices from across your organization. Your IT team understands the technical landscape, but legal knows the regulatory nuances, HR understands employee-related risks, and senior management provides the business context. This diverse perspective prevents blind spots that could derail your assessment.
Securing leadership support isn’t just about getting approval – it’s about ensuring your team has the authority and resources needed to implement changes. When leadership champions the process, other departments take it seriously and provide the cooperation necessary for success.
Step 2: Conduct a Risk Assessment and Controls Review
This step involves rolling up your sleeves and diving deep into your IT environment. As industry experts emphasize, an IT risk assessment is something you can’t afford to skip – it forms the foundation of your entire compliance program.
Identifying information assets starts with cataloging everything that matters to your business. Your customer database, financial records, intellectual property, and employee information all qualify as critical assets. The trick is getting input from every department because different teams prioritize different assets. Sales might focus on the CRM system, while accounting emphasizes financial data, and HR protects employee records.
Classifying data helps you understand what you’re protecting and how much protection it needs. Public information requires minimal safeguards, while restricted data demands your strongest security measures. This classification drives many of your subsequent security decisions.
Identifying threats and vulnerabilities means looking at your environment through an attacker’s eyes. External threats like malicious hackers grab headlines, but internal risks like employee errors or system failures can be equally damaging. We examine everything from outdated software and weak passwords to inadequate backup procedures and insufficient employee training.
Analyzing existing controls involves evaluating both your preventive measures (firewalls, encryption, access controls) and detective capabilities (monitoring systems, log analysis, intrusion detection). This analysis reveals whether your current security investments are actually protecting what matters most to your business.
At Kraft Business Systems, our expertise in managed cybersecurity services helps businesses steer this complex landscape, ensuring no critical vulnerability goes unnoticed.
Step 3: Perform Gap Analysis
Now comes the moment of truth – comparing where you are with where you need to be. Think of this as holding up your current practices against a compliance ruler to see where you measure up.
Documenting findings from your risk assessment creates the baseline for comparison. Every observation, every control, every vulnerability gets recorded in detail. This documentation becomes crucial evidence of your compliance efforts.
Comparing current state to framework requirements is where the rubber meets the road. We take each requirement from your chosen compliance framework – whether it’s NIST, ISO 27001, or industry-specific standards – and evaluate how well your current practices align. This systematic comparison reveals exactly where you stand.
Identifying compliance gaps highlights the specific areas needing attention. Maybe your password policy doesn’t meet the framework’s complexity requirements, or your incident response plan lacks required documentation. Each gap represents a potential compliance violation that needs addressing.
Prioritizing gaps based on risk level ensures you tackle the most critical issues first. A missing firewall rule that exposes sensitive data to the internet demands immediate attention, while updating an internal policy might wait until next quarter. This risk-based prioritization helps you allocate limited resources where they’ll have the greatest impact.
Step 4: Develop a Remediation Plan
Identifying gaps is only half the battle – closing them requires a well-structured remediation plan that transforms findings into actionable improvements.
Creating an action plan means developing specific, measurable steps for addressing each identified gap. If multi-factor authentication is missing from critical systems, your action plan might include selecting an MFA solution, configuring it for key applications, training users, and establishing ongoing maintenance procedures.
Assigning responsibilities ensures accountability throughout the remediation process. Each action item needs a clear owner who understands their role and has the authority to implement changes. Without clear ownership, even the best plans can stall indefinitely.
Setting deadlines and milestones creates momentum and helps track progress. Realistic timelines acknowledge the complexity of implementation while maintaining urgency around critical security gaps. Breaking larger projects into smaller milestones makes progress visible and keeps teams motivated.
Allocating resources involves more than just budgeting for new technology. Consider the time your staff will need for training, the potential disruption to business operations during implementation, and any external expertise required for specialized tasks.
Documenting all remediation activities creates an audit trail that demonstrates your commitment to compliance. This documentation proves invaluable during external audits and helps maintain institutional knowledge as your team evolves.
Step 5: Report and Communicate Findings
Clear communication transforms your assessment findings into business intelligence that drives informed decision-making across your organization.
Creating a comprehensive report means compiling all findings, analyses, and recommendations into a document that tells the complete story of your compliance posture. This report becomes a reference point for future assessments and a roadmap for ongoing improvements.
Tailoring reports for different stakeholders acknowledges that different audiences need different information. Your technical team wants detailed implementation guidance, while executive leadership focuses on business risks, costs, and strategic implications. A good report serves both audiences without overwhelming either.
Presenting findings clearly means avoiding technical jargon when communicating with business stakeholders and providing sufficient detail when addressing technical teams. Visual elements like charts and graphs can help communicate complex information more effectively.
Highlighting risks and business impact connects technical findings to business outcomes. Instead of simply noting that patch management needs improvement, explain how unpatched systems could lead to data breaches, regulatory fines, and reputational damage.
Recommending improvements goes beyond identifying problems to suggest practical solutions. These recommendations should consider your organization’s resources, risk tolerance, and business objectives to ensure they’re both effective and achievable.
Step 6: Implement Continuous Monitoring and Training
Compliance isn’t a destination – it’s an ongoing journey that requires sustained attention and regular course corrections.
Establishing ongoing monitoring processes recognizes that both cyber threats and regulatory requirements constantly evolve. Continuous monitoring helps you detect new vulnerabilities, track the effectiveness of implemented controls, and identify emerging risks before they become serious problems.
Automating evidence collection reduces the manual burden of compliance reporting while improving accuracy and consistency. Modern compliance tools can automatically gather logs, generate reports, and track control effectiveness, freeing your team to focus on strategic improvements rather than administrative tasks.
Employee training and awareness transforms your workforce from a potential vulnerability into your strongest defense. Regular training sessions on cybersecurity best practices, phishing awareness, and social engineering help employees recognize and respond appropriately to threats. Phishing simulations provide safe opportunities to practice these skills and identify areas needing additional attention.
Updating processes for new regulations ensures your compliance program remains current as requirements change. This proactive approach prevents compliance gaps from developing and positions your organization to adapt quickly to new regulatory demands.
For comprehensive support with your ongoing IT compliance needs, explore our full range of IT solutions designed to keep your business secure and compliant.
Navigating Key Compliance Frameworks
Understanding which compliance framework applies to your business is a critical first step in your IT compliance assessment journey. While regulations can seem like a tangled web, a few frameworks serve as cornerstones for most industries. The good news? You don’t need to master every framework out there – just the ones that matter for your specific business.
Think of compliance frameworks as different languages that all say the same basic thing: “protect your data and prove you’re doing it right.” Each framework has its own accent and vocabulary, but they’re all working toward similar goals of security, privacy, and accountability.
Comparing Popular Compliance Frameworks
| Framework | Primary Focus | Key Industries | Example Requirement |
|---|---|---|---|
| HIPAA | Protected Health Information (PHI) | Healthcare, Business Associates | Encrypt patient data in transit and at rest |
| PCI DSS | Cardholder Data Protection | E-commerce, Retail, Financial | Maintain secure network with firewalls |
| GDPR | Personal Data of EU Citizens | Any business processing EU data | Obtain explicit consent for data collection |
| SOC 2 | Trust Services Criteria | SaaS, Cloud Providers, Data Centers | Implement logical access controls |
| ISO 27001 | Information Security Management | Manufacturing, Technology, Finance | Establish risk management processes |
This table gives you a quick snapshot, but let’s dive deeper into the frameworks that matter most for Michigan businesses and beyond.
Health Insurance Portability and Accountability Act (HIPAA)
If your business touches healthcare data in any way, HIPAA compliance is non-negotiable. This framework protects Protected Health Information (PHI) and applies not just to healthcare providers like hospitals and clinics, but also to business associates – companies that handle PHI on behalf of covered entities.
Many businesses don’t realize they fall under HIPAA’s umbrella. If you’re an IT support company working with medical practices, a cloud storage provider hosting patient records, or even a billing company processing healthcare payments, you’re likely a business associate subject to HIPAA requirements.
The official HIPAA information from the CDC provides comprehensive guidance, but the core principle is straightforward: patient data privacy must be maintained through technical, physical, and administrative safeguards. This means encrypting data, controlling access, training employees, and having clear procedures for handling breaches.
Payment Card Industry Data Security Standard (PCI DSS)
Processing credit card payments? Then PCI DSS is your reality. This framework focuses specifically on cardholder data protection and applies to any business that accepts, processes, stores, or transmits credit card information – from large e-commerce sites to small retail shops.
The PCI Security Standards Council maintains these standards, which require secure payment processing through twelve core requirements. These include maintaining secure networks, protecting stored cardholder data, implementing strong access controls, and regularly monitoring networks.
What makes PCI DSS unique is its tiered approach based on transaction volume. A small boutique in downtown Grand Rapids processing 20,000 Visa transactions annually has different requirements than a major e-commerce platform processing millions. However, the fundamental principle remains the same: if you touch card data, you must protect it.
General Data Protection Regulation (GDPR)
Don’t think GDPR only applies to European companies. If your business processes personal data of EU citizens – whether through website visitors, customers, or employees – GDPR compliance is required. This includes something as simple as having EU visitors fill out a contact form on your website.
The GDPR official text is comprehensive, but the framework centers on data subject rights and consent management. EU citizens have the right to know what data you collect, how you use it, and they can request deletion or corrections. You must obtain explicit consent for data collection and processing, and you need clear procedures for handling these requests.
For Michigan businesses, GDPR often comes into play through digital marketing, e-commerce sales, or international partnerships. The key is understanding that geographic location of your business doesn’t matter – it’s about whose data you’re processing.
SOC 2 and ISO 27001
These frameworks often go hand-in-hand for service organizations, particularly SaaS companies and data centers. While they have different origins and structures, both focus on systematic approaches to information security.
SOC 2 evaluates controls based on Trust Services Criteria, focusing on Security, Availability, Processing Integrity, Confidentiality, and Privacy. It’s particularly valuable for companies that need to demonstrate their security practices to customers and partners. The assessment results in a report that you can share with stakeholders as proof of your security posture.
ISO 27001, meanwhile, requires implementing an Information Security Management System (ISMS) – a systematic approach to managing sensitive information. This framework is more prescriptive than SOC 2, requiring specific policies, procedures, and continuous improvement processes.
Many businesses pursuing one of these frameworks find value in pursuing both, as they complement each other well and demonstrate a comprehensive commitment to information security.
The reality is that most growing businesses will encounter multiple frameworks. A healthcare technology company might need HIPAA for patient data, PCI DSS for payment processing, and SOC 2 for customer trust. The good news? Many controls overlap between frameworks, so implementing one often helps with others.
Understanding these frameworks is just the beginning of your IT compliance assessment journey, but it’s a crucial foundation for protecting your business and building trust with customers and partners.