AI Overview:
Financial institutions are 300x more likely to be attacked by cybercriminals than other industries. The average cost of a data breach is $5.97 million, and 62% of consumers lose trust after a compliance failure. In today’s environment, IT compliance isn’t just about avoiding fines—it’s about building trust, resilience, and competitive advantage.
It compliance financial services: Master 2025 Compliance
Why IT Compliance is Critical for Financial Services
IT compliance financial services represents one of the most challenging yet essential aspects of running a modern financial institution. With financial organizations being targeted by cyberattacks 300 times more often than other industries, the stakes couldn’t be higher.
Key Components of Financial IT Compliance:
- Data Protection – Safeguarding customer information and financial records
- Regulatory Adherence – Meeting requirements from GDPR, SOX, PCI-DSS, and FinCEN
- Security Infrastructure – Implementing robust cybersecurity measures
- Audit Trails – Maintaining comprehensive logging and monitoring
- Risk Management – Continuously assessing and mitigating threats
The financial sector faces a perfect storm of challenges. The average cost of a data breach tops $5.97 million, while 62% of consumers lose trust in providers after compliance failures. With over 75% of European compliance leaders reporting a 35% rise in their workload, the pressure is mounting.
But here’s the reality: compliance isn’t just about avoiding penalties. It’s about building the foundation for customer trust, operational stability, and competitive advantage. When done right, IT compliance transforms from a burden into a business enabler.
This guide breaks down everything you need to know about financial IT compliance – from understanding key regulations to building a resilient infrastructure that protects your business and customers.
It compliance financial services terms at a glance:
- compliance services
- information technology audit services
- it governance risk and compliance management
Understanding the Regulatory Landscape for Financial Services
The financial services industry truly operates under a microscope, and for very good reasons! Your business handles so much sensitive data—from personal details to every transaction record. This makes financial institutions like yours a top target for cybercriminals. But it’s not just about warding off attacks. This industry is also heavily regulated. These rules are in place to keep consumers safe, ensure markets are stable, and prevent illegal activities. All of this means a significant regulatory burden for you. Every piece of your IT infrastructure, every process, and every bit of data must meet very strict standards.
The consequences of missing these standards are no joke. Think about the huge hit to consumer trust if a bank suffered a major data breach. Our research shows that a staggering 62% of consumers are less likely to trust a provider after a compliance breach. Beyond just damaging your reputation, the financial penalties can be devastating. The average cost of a data breach in the financial sector is a shocking $5.97 million. And this figure can soar even higher if non-compliance is a factor. It’s clear: in this landscape, being vigilant isn’t just a good idea; it’s absolutely essential for your business to thrive.
Key Regulations You Must Know
Feeling a bit overwhelmed by the maze of regulations? You’re not alone! But some frameworks are super important for it compliance financial services across the board. Let’s look at some of the most impactful ones.
First up is the General Data Protection Regulation (GDPR). Even though it’s an EU regulation, the GDPR has global reach. If your financial institution handles data from EU citizens, you must comply, no matter where your business is located. It sets strict rules for data privacy and security, focusing on principles like fairness, transparency, and keeping data to a minimum.
Then there’s the Sarbanes-Oxley Act (SOX), mainly for the United States. The SOX Act requires tough standards for how you handle accounting and financial reporting. For your IT team, this means making sure financial data is accurate, easy to access, and that the systems holding it are rock-solid. For example, SOX Section 404 demands measures to protect financial data’s authenticity and availability.
If you handle credit card transactions, the Payment Card Industry Data Security Standard (PCI-DSS) is absolutely critical. It lays out security standards to protect cardholder data, covering everything from building secure networks and strong access controls to regularly monitoring those networks.
The Financial Crimes Enforcement Network (FinCEN), a part of the U.S. Treasury, plays a big role in fighting financial crimes like money laundering and terrorism financing. The FinCEN requires financial institutions to have strong Anti-Money Laundering (AML) programs, including checking customers, watching transactions, and reporting anything suspicious.
In the U.S., the Gramm-Leach-Bliley Act (GLBA) governs how you collect, keep safe, and use private financial information. It requires you to tell customers how you share their data, offer them ways to opt-out, and protect their “nonpublic personal information” (NPI). This includes a “Safeguards Rule” that demands a complete information security program.
Finally, a newer and very important EU regulation is the Digital Operational Resilience Act (DORA). The DORA aims to boost the digital resilience and security of the EU’s financial sector. It really stresses managing risks with third-party tech vendors, reporting incidents, testing resilience, and sharing threat intelligence. It calls for a truly holistic approach to digital risk.
The High Cost of Non-Compliance
Let’s be clear: ignoring these regulations is simply not an option. The effects of non-compliance go way beyond just a small penalty; they can actually threaten your financial institution’s very existence.
One of the most immediate impacts is financial fines and penalties. Regulators aren’t shy about handing out hefty fines. Our research shows that 36% of UK firms received penalties for non-compliance in 2023. These aren’t minor fees; we’re talking millions, or even billions, of dollars. That can seriously hit your profits and capital.
Then there’s legal liability. Non-compliance can open the door to lawsuits from unhappy customers or investors, leading to expensive legal battles and settlements. In some cases, executives can even face jail time if their organization breaks laws like SOX.
A history of non-compliance also often brings increased audits and scrutiny. Regulatory bodies might start checking your business more often and more deeply. This pulls valuable time and resources away from your main business activities. You could also face business disruption. Penalties can include stopping operations, suspensions, or even losing your licenses. This can directly halt or severely limit your financial institution’s ability to operate.
As we touched on earlier, customer churn and reputational damage are huge concerns. 62% of consumers are less likely to trust a financial provider after a compliance breach. Winning back that trust after a major incident is an incredibly difficult climb, often leading to customers leaving and a damaged brand image.
Finally, non-compliance can lead to exacerbated breach costs. The IBM Cost of a Data Breach Report 2023 found that organizations with high non-compliance actually saw their breach costs increase by over 12.6%, averaging $5.05 million.
The bottom line is that the cost of non-compliance far outweighs the investment you make in robust it compliance financial services. It’s a powerful reminder that being proactive with compliance is truly an investment in your institution’s future.
Core Components of a Compliant IT Infrastructure
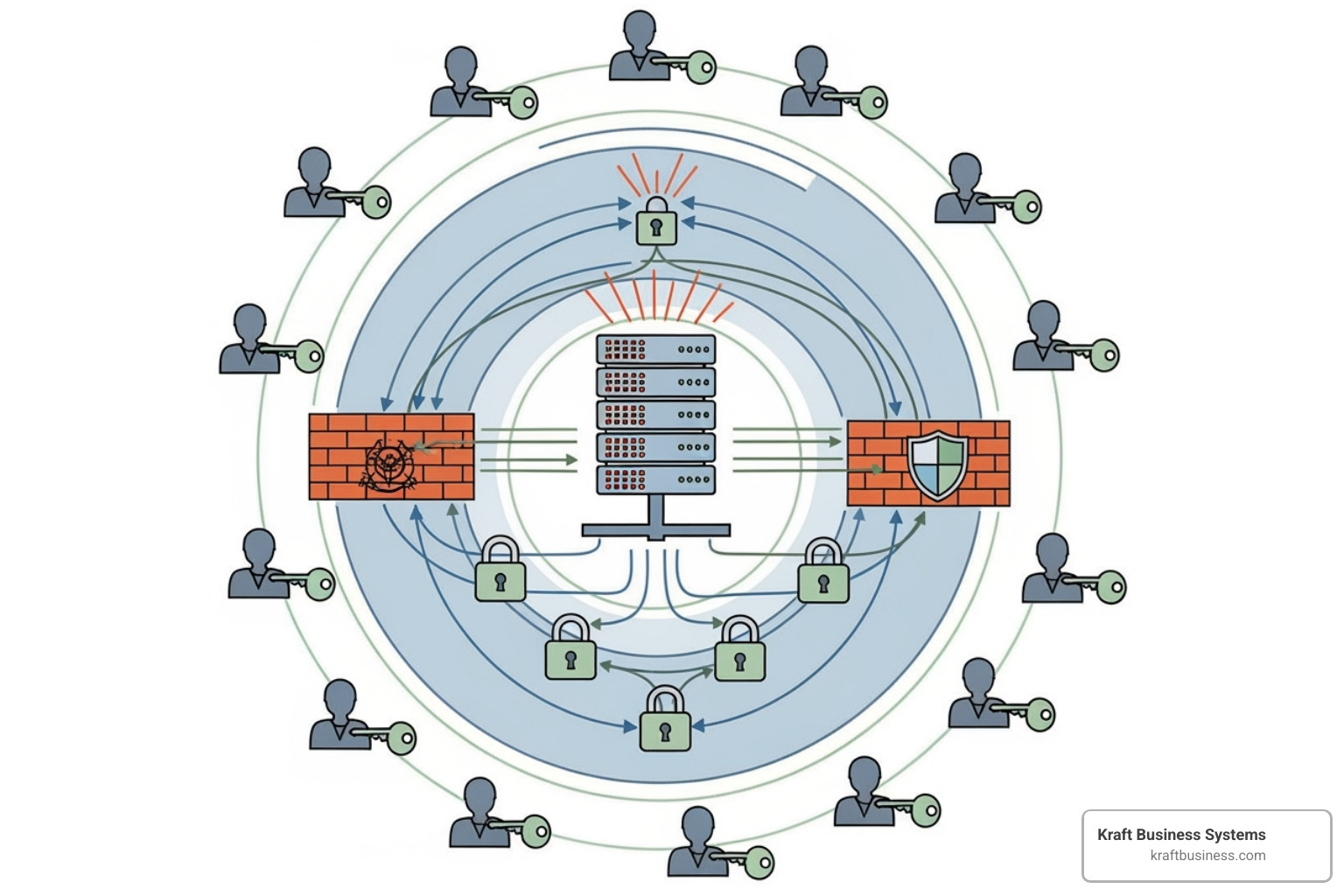
Building a compliant IT infrastructure is like constructing a digital fortress – every layer matters, and each component must work seamlessly with the others. For financial institutions, this isn’t just about meeting regulatory checkboxes; it’s about creating a security by design foundation that protects your most valuable assets: customer data and trust.
Think of compliance as your business insurance policy. When done right, a compliant infrastructure becomes more than a technical requirement – it transforms into a competitive advantage that demonstrates your commitment to security and reliability. Your customers sleep better at night knowing their financial information is protected, and your business operates with confidence.
Data Encryption and Protection
Imagine your customer data as precious cargo that needs protection whether it’s sitting in a vault or traveling across the country. That’s exactly how we need to think about data encryption and protection in it compliance financial services.
Data at rest – information stored on servers, databases, or backup systems – requires bulletproof protection. We recommend using Advanced Encryption Standard (AES) with at least 128-bit encryption, though many institutions opt for 256-bit for maximum security. It’s like having an unbreakable safe for your digital assets.
Data in transit presents different challenges. When information moves between systems during transactions or communications, it travels through potentially hostile territory. Secure protocols like SSL, TLS, SSH, and IPSEC create encrypted tunnels that keep prying eyes away from sensitive information.
The secret sauce lies in key management. Even the strongest encryption becomes worthless if the keys fall into the wrong hands. A robust key management system ensures that encryption keys are securely generated, properly stored, and regularly rotated – think of it as changing the locks on your most important doors.
For handling highly sensitive financial data, encryption must comply with Federal Information Processing Standards (FIPS). This government-validated standard ensures your cryptographic modules meet the highest security requirements.
Identity and Access Management (IAM)
The fundamental question in financial security is simple: Who gets access to what, and when? Identity and Access Management answers this question with precision and control.
Multi-factor authentication (MFA) adds crucial layers beyond traditional passwords. By requiring something you know (password), something you have (phone or token), or something you are (fingerprint), MFA dramatically reduces unauthorized access risks. It’s like having multiple locks on your front door – if one fails, others still protect you.
The principle of least privilege ensures users are granted only the access necessary to perform their job functions. This minimizes potential damage if an account gets compromised. Think of it as giving each employee only the keys they actually need, not the master key to everything.
Role-based access controls (RBAC) streamline this process by assigning permissions based on job roles rather than individual requests. A teller gets teller-level access, while a loan officer receives different permissions entirely. This approach ensures consistency and simplifies management across your organization.
Comprehensive Audit Trails and Logging
In the financial world, everything must be traceable. Comprehensive logging creates a detailed story of every action taken within your IT infrastructure – who did what, when they did it, and what happened as a result.
System activity logs capture the complete picture: user logins, access attempts (both successful and failed), data modifications, and system configuration changes. These logs become your digital witnesses, providing crucial evidence during investigations or audits.
Tamper-evident logs take security a step further by detecting unauthorized alterations. If someone tries to cover their tracks by modifying log files, these systems sound the alarm. It’s like having security cameras that can’t be turned off or edited.
Event monitoring transforms passive logging into active protection. By continuously analyzing log data, your systems can detect anomalies and potential security incidents in real-time, enabling swift response to threats.
When auditors come knocking or incidents require investigation, detailed logs provide the forensic analysis capabilities needed to understand exactly what happened. They’re essential for maintaining accountability and proving compliance with regulations like SOX.
Disaster Recovery and Business Continuity
Even the best-protected systems can face disasters – cyberattacks, natural catastrophes, or equipment failures. The question isn’t whether something will go wrong, but how quickly you can recover when it does.
Data backups form your safety net, but they’re only valuable if they work when needed. Regular, secure backups stored off-site provide the foundation for recovery, but they must be tested periodically to ensure integrity and recoverability.
Restoration plans turn backups into actionable recovery strategies. Having detailed, documented procedures for restoring systems and data ensures your team can act quickly and effectively during a crisis. These plans should be as familiar to your IT team as fire evacuation routes are to building occupants.
Incident response plans outline immediate steps following security incidents or disasters. From initial containment through complete recovery, these plans provide the roadmap for navigating chaos and returning to normal operations.
Operational resilience goes beyond simple data recovery to ensure critical business functions continue with minimal disruption. This means having redundant systems, alternative processing sites, and clear communication protocols that keep your business running even when primary systems are compromised.
The most important aspect of disaster recovery is regular testing. Plans that sit on shelves gathering dust often fail when needed most. Regular drills and simulations identify weaknesses and refine procedures, ensuring your team is prepared for real emergencies.
Together, these components create a resilient foundation for it compliance financial services that protects your business, satisfies regulators, and maintains the customer trust that’s essential for long-term success.
A Proactive Approach to IT Compliance
The financial world moves fast, and waiting for problems to happen before fixing them is like trying to stop a speeding train with your bare hands. We’ve learned this lesson the hard way. Cyber incidents in the financial sector doubled in Q3 2023 compared to the previous year, as reported by Positive Technologies. That’s not just a statistic—it’s a wake-up call.
IT compliance financial services can’t be something you do once and forget about. It’s more like tending a garden. You need to water it, weed it, and watch for pests every single day. The threats keep evolving, regulations keep changing, and your business keeps growing. A reactive stance is no longer sufficient in this environment.
Think about it this way: would you rather find a small leak in your roof during a routine inspection, or find it when water is pouring into your living room during a storm? The same principle applies to compliance. Continuous compliance and risk management aren’t just buzzwords—they’re your lifeline in an industry where adapting to change can mean the difference between thriving and barely surviving.
Assessing and Auditing Your Infrastructure for IT Compliance Financial Services
You can’t fix what you don’t know is broken. That’s why regular gap analysis and risk assessments form the backbone of any smart compliance strategy. We’re not talking about checking boxes on a form and calling it a day. This is about really understanding where your business stands.
Internal audits should happen regularly—think of them as your routine health checkups. Your team knows your systems inside and out, so they can spot the subtle changes that might signal trouble. But just like you wouldn’t diagnose yourself with a serious illness, external audits bring in fresh eyes and specialized expertise that can catch what you might miss.
Penetration testing takes this one step further. Instead of just looking for problems, it actively tries to exploit them. It’s like hiring a professional thief to test your home security—except this thief is on your side and will tell you exactly how they got in so you can fix it.
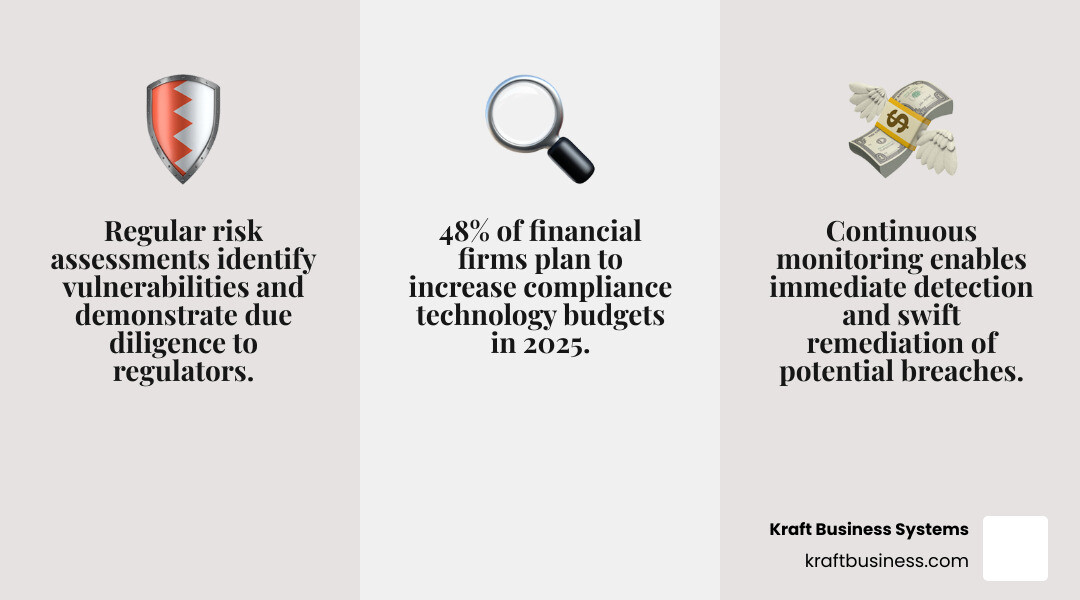
Regular assessments identify vulnerabilities before they can be exploited and demonstrate due diligence to regulators. More importantly, they give you the confidence that comes from knowing exactly where you stand. When audit season rolls around, you’re not sweating bullets—you’re ready.
The Role of Ongoing Monitoring
Imagine trying to drive a car with your eyes closed, only opening them once every few miles to check if you’re still on the road. Sounds terrifying, right? Yet that’s exactly what many financial institutions do with their IT compliance—they check in periodically but fly blind the rest of the time.
Real-time alerts and anomaly detection are like having your eyes wide open while driving. They spot the unusual before it becomes the catastrophic. Maybe it’s a login attempt from halfway around the world at 3 AM, or a sudden spike in data transfers that doesn’t match normal patterns. These systems catch the red flags before they become full-blown emergencies.
Security Information and Event Management (SIEM) solutions act like your central nervous system, pulling together information from every corner of your IT environment. They don’t just collect data—they make sense of it, connecting dots that human analysts might miss when they’re looking at thousands of events every day.
This proactive defense approach means you’re not just waiting for something bad to happen. Continuous monitoring allows for the immediate detection of potential breaches, enabling swift remediation before significant damage occurs. It’s the difference between stopping a burglar at the front door versus finding them in your safe.
Adapting to New Threats and Regulations like DORA
The only constant in financial IT compliance is change. New threats emerge daily, and regulators respond with new requirements that can reshape your entire compliance strategy overnight. Staying ahead means embracing threat intelligence and keeping your finger on the pulse of regulatory updates.
Take the EU’s Digital Operational Resilience Act (DORA), which highlights the growing focus on ensuring the entire digital ecosystem is secure and resilient. DORA isn’t just another acronym to memorize—it represents a fundamental shift toward digital resilience strategy that goes beyond traditional security measures.
Third-party risk management has become especially critical as financial institutions rely more heavily on external vendors and cloud services. Your compliance is only as strong as your weakest vendor link. When a third-party provider experiences a breach, regulators don’t just shrug and say “not your fault.” They hold you accountable for your vendor choices and oversight.
The key is building adaptability into your compliance framework from the ground up. Instead of scrambling to retrofit new requirements into old systems, proactive organizations design their infrastructure to flex and evolve. They treat compliance as a living, breathing part of their business strategy rather than a necessary evil to be minimized.
This proactive mindset transforms IT compliance financial services from a defensive reaction into a competitive advantage. When you’re ahead of the curve, compliance becomes less about avoiding problems and more about enabling your business to grow safely and confidently.
Leveraging Technology and Expertise for Financial IT Compliance Services
The world of IT compliance financial services can feel overwhelming – like trying to solve a thousand-piece puzzle while someone keeps changing the picture. Manual spreadsheets, endless email chains, and reactive approaches simply don’t cut it anymore. The good news? Technology has evolved to make compliance more manageable, and the right expertise can transform this complex challenge into a competitive advantage.
Nearly half of all financial firms plan to increase their compliance technology budgets, recognizing that manual processes are no longer sustainable. This shift isn’t just about spending more money – it’s about working smarter, not harder.
Essential Tools for Modern Compliance
Think of compliance management software as your digital command center – a place where all the moving pieces come together. These platforms give you a bird’s-eye view of your entire compliance landscape, tracking regulatory changes as they happen and mapping your controls to specific requirements automatically.
Automation tools are your secret weapon against human error. They handle the repetitive tasks that used to eat up hours of your team’s time – data classification, vulnerability scanning, log analysis, and even parts of incident response. This frees up your people to focus on strategy and problem-solving rather than data entry.
Artificial intelligence is starting to shine in compliance, particularly for spotting patterns humans might miss. AI-powered systems can detect anomalies, prevent fraud, and even predict potential compliance risks before they become problems. It’s like having a crystal ball, but one backed by data and algorithms.
Leveraging the right technology provides a centralized system to manage policies, track controls, and automate reporting. The result? Compliance becomes less of a daily struggle and more of a well-oiled machine running in the background.
The Power of Secure Cloud Services
The cloud has revolutionized how financial institutions handle their IT needs, offering the kind of scalability that would have been impossible just a decade ago. But here’s what makes it particularly attractive for IT compliance financial services: the heavy lifting is often already done for you.
Major cloud providers like AWS offer environments that meet numerous security certifications, allowing firms to operate securely and confidently in the cloud. These providers have invested billions in security infrastructure and maintain compliance with standards you’d spend years trying to achieve on your own.
The shared responsibility model is key to understanding cloud security. Think of it like living in a secure apartment building – the building owner handles the physical security, elevators, and utilities, while you’re responsible for locking your door and securing your belongings. The cloud provider secures the infrastructure, while you handle your data and applications.
This partnership approach means you get enterprise-grade security without the enterprise-grade headaches of managing it all yourself.
Why Partner with a Managed Service Provider (MSP) for IT compliance financial services?
Here’s the reality: building an in-house team with deep expertise in financial regulations, cybersecurity, and emerging technologies is expensive and time-consuming. By the time you’ve hired and trained everyone, the regulatory landscape has shifted again.
A specialized MSP brings years of focused experience in financial services compliance. We understand the nuances of GDPR, SOX, PCI-DSS, and newer regulations like DORA. More importantly, we’ve seen how these regulations play out in real-world scenarios across different types of financial institutions.
Cost-effectiveness is often the deciding factor. Instead of maintaining full-time salaries for specialized roles you might only need part-time, an MSP gives you access to an entire team of experts for a fraction of the cost. You get enterprise-level expertise without the enterprise-level overhead.
24/7 monitoring means threats are detected and addressed around the clock, not just during business hours. Cybercriminals don’t work 9-to-5 schedules, and neither do we. This continuous vigilance is especially crucial for financial institutions where downtime can mean lost revenue and damaged trust.
Beyond day-to-day management, a good MSP acts as your strategic partner. We help you anticipate regulatory changes, evaluate new technologies, and develop long-term compliance strategies. It’s like having a seasoned guide when you’re navigating unfamiliar territory.
At Kraft Business Systems, we understand the unique challenges facing financial institutions in Grand Rapids, MI, and beyond. We combine local knowledge with national expertise to help firms build robust, compliant IT infrastructures that protect both their operations and their customers’ trust.
Frequently Asked Questions about Financial IT Compliance
Navigating it compliance financial services can bring up a lot of questions. We’ve compiled some of the most common ones to help clarify key aspects and give you a clearer picture of what’s involved.
What is the most critical aspect of IT compliance for financial services?
At the very heart of it compliance financial services is one unwavering priority: protecting sensitive customer data. We're talking about nonpublic personal information (NPI), the kind of data that, if compromised, can shatter trust and cause significant damage. Safeguarding this information isn't just a regulatory checkbox; it's the foundation of your customer relationships and your institution's reputation.
Achieving this paramount protection requires a thoughtful, multi-layered security approach. This means implementing robust encryption, often requiring strict Federal Information Processing Standards (FIPS) compliance for highly sensitive data, to make sure information is unreadable to unauthorized eyes. Equally vital are strict access controls, built on the principle of least privilege, ensuring that only those who absolutely need access to specific data can get it. And because threats are constant, continuous monitoring is essential to detect and prevent unauthorized access and data breaches in real-time. Our goal is to safeguard not just the data itself, but the precious trust our customers place in us every single day.
How often should a financial institution conduct IT compliance audits?
Think of it compliance financial services as a continuous journey, not a one-time event. Therefore, best practices recommend a continuous cycle of assessments rather than isolated, infrequent checks. This typically involves several components:
Ongoing internal monitoring and vulnerability scanning: These are your daily checks, helping to identify potential weaknesses as they emerge.
Formal internal audits: These should be conducted at least annually. They're a deeper dive into your processes and controls, ensuring everything aligns with internal policies and regulatory requirements.
Periodic external audits: For an unbiased perspective, external audits are usually performed every one to three years, or as specifically mandated by certain regulations like PCI-DSS.
SOX audits: For instance, if you're subject to the Sarbanes-Oxley Act (SOX), you'll likely face an annual review of your internal controls related to financial reporting.
Regular penetration testing: Don't forget to include these! They simulate real-world cyberattacks to identify vulnerabilities before malicious actors do.
This layered approach ensures that your institution remains vigilant, adaptable, and consistently compliant in an ever-changing threat landscape.
Can a small financial firm achieve the same level of IT compliance as a large bank?
Absolutely! It's a common misconception that top-tier it compliance financial services are only within reach for large institutions with massive budgets. While resources may naturally differ, small financial firms can certainly achieve enterprise-grade compliance. The secret lies in smart strategies and leveraging the right partnerships.
One powerful avenue is to accept scalable cloud solutions. Major cloud providers like AWS offer environments that come with extensive built-in compliance frameworks and certifications. This means they've already handled much of the underlying infrastructure security and compliance, giving smaller firms a huge head start. Another game-changer is partnering with a Managed Service Provider (MSP). An MSP, like Kraft Business Systems, provides access to advanced security tools, specialized expertise in financial regulations, and continuous monitoring – all without the high cost of building and maintaining a large, in-house IT and compliance team. This smart approach allows smaller firms to focus on their core business activities while confidently knowing their it compliance financial services posture is robust, secure, and ready for any challenge.
Conclusion
Navigating it compliance financial services can feel like an endless quest, doesn’t it? But here’s the good news: it’s not a finish line you cross once, but rather a continuous journey of protecting what matters most. It’s all about staying proactive, safeguarding your precious data, nurturing the trust your customers place in you, and building an operational resilience that can stand strong against any challenge. With cyber threats constantly evolving and regulations always updating, constant vigilance isn’t just a buzzword – it’s your secret to success.
By thoughtfully blending a robust IT infrastructure, smart modern technology, and a little expert guidance, financial institutions can truly build a compliance framework that’s not just secure, but also future-proof. Think of it as laying down a strong foundation that will serve you well for years to come.
So, how do you keep moving forward on this journey? It comes down to a few key Best Practices for Continuous Compliance:
First off, you’ll want to conduct regular risk assessments and gap analyses. This helps you spot potential vulnerabilities and areas for improvement before they become bigger problems. It’s like checking your car’s oil before a long road trip!
Next, accept the power of technology. Leverage automation and compliance management software to streamline those complex processes and ensure everything is accurate and up-to-date. Why do manually what a smart system can do for you?
Don’t forget your most valuable asset: your people. Implement ongoing security awareness training for all employees. After all, a well-informed team is your best defense against many threats.
And finally, you don’t have to go it alone. Partner with experts who specialize in financial services IT to guide you through the intricate web of regulations and evolving threats. They’ve got the knowledge and experience to keep you on the right path.
Here at Kraft Business Systems, we truly get these challenges. Located right here in Grand Rapids, MI, and proudly serving businesses across Michigan, we’re dedicated to helping financial institutions steer this complex landscape. Our custom IT support and security solutions are designed to make your journey smoother, leveraging our diverse team of consultants and industry experts to provide innovative and secure technology that makes your IT infrastructure a real asset to your business.
Ready to strengthen your compliance posture and feel more confident about your future? Learn more about our managed cybersecurity services.