AI Overview:
Comprehensive IT compliance services transform regulatory obligations into a strategic advantage for businesses. By combining risk assessments, policy creation, monitoring, audits, and staff training, these services protect sensitive data, reduce penalties, and enhance operational efficiency — ultimately building trust and opening new markets.
Why Comprehensive IT Compliance Services Are Essential for Modern Businesses
Comprehensive IT compliance services help businesses steer complex regulatory requirements while protecting sensitive data and avoiding costly penalties. These services combine risk assessments, policy development, continuous monitoring, and audit preparation to ensure your technology meets industry standards.
What comprehensive IT compliance services include:
- Risk Assessment & Gap Analysis – Evaluate current systems against regulatory requirements
- Policy & Procedure Development – Create documentation for compliance frameworks
- Continuous Monitoring – Track compliance status in real-time across all systems
- Audit Preparation – Maintain audit-ready documentation and evidence
- Training & Support – Educate staff on compliance requirements and best practices
- Technology Implementation – Deploy security controls and automated compliance tools
The regulatory landscape is becoming more complex every year. As one compliance expert noted, “Without automation and practitioner expertise, compliance becomes reactive, resource-draining, and disconnected from day-to-day operations.”
The stakes are high. Research shows that 90% of small businesses experienced data breaches in 2023, with non-compliance penalties reaching millions of dollars. But there’s good news: businesses using comprehensive compliance services report 90% faster evidence collection, 100% asset coverage across environments, and significant improvements in operational efficiency.
Modern compliance isn’t just about avoiding penalties. It’s about changing regulatory requirements into business advantages that improve security, streamline operations, and build customer trust. Companies that get this right often find compliance opens doors to new contracts and markets that require strict security standards.
Comprehensive it compliance services word roundup:
- it governance risk and compliance management
- it compliance assessment
- it compliance standards
What Are IT Compliance Services and Why Are They Important?
Think of comprehensive IT compliance services as your business’s digital bodyguard—they’re always watching, always protecting, and always ready to step in when threats appear. Where cyber attacks happen every 39 seconds and regulations change faster than your morning coffee gets cold, these services have become absolutely essential for businesses of all sizes.
At their heart, IT compliance services ensure your business follows the rules—all the complex, ever-changing rules that govern how you handle technology and data. But here’s the thing: regulatory adherence isn’t just about avoiding trouble with the authorities. It’s about building a fortress around your most valuable assets: your data, your reputation, and your customers’ trust.
The risk mitigation aspect is where things get really interesting. Instead of waiting for problems to knock on your door, these services help you spot potential issues before they become expensive headaches. It’s like having a crystal ball, but one backed by solid technology and expertise rather than mystical powers.
Our comprehensive IT compliance services work through several core service components that fit together like pieces of a well-designed puzzle. Gap analysis forms the foundation—we look at where you are now versus where regulations say you need to be. Think of it as a health checkup for your IT systems, but instead of checking your blood pressure, we’re measuring how well your data protection measures stack up against industry standards.
Policy development comes next, where we help create clear, practical guidelines that your team can actually follow. Nobody wants policies that read like ancient legal texts—we focus on making them understandable and actionable. Continuous monitoring ensures you don’t just set it and forget it. Like tending a garden, compliance requires ongoing attention to flourish.
Audit preparation might sound intimidating, but it’s really about being ready to show off all the good work you’ve done. When auditors come knocking, you’ll have everything organized and ready to go, making the process smooth for everyone involved.
The statistics paint a clear picture of why this matters: 60% of small businesses experienced a data breach in 2023. That’s not just a number—it represents real companies, real people, and real consequences. But here’s the encouraging part: businesses that invest in proper compliance services significantly reduce their risk of joining those statistics.
Core Components of IT Compliance
Building effective IT compliance is like constructing a house—you need the right materials, a solid foundation, and skilled craftsmanship. The core components work together to create a structure that protects your business from regulatory storms and cyber threats.
Risk assessments serve as your blueprint. We examine every corner of your IT environment, from the servers humming in your office to the cloud services your team uses daily. This isn’t about finding fault—it’s about understanding your current security posture and identifying areas where improvements will have the biggest impact.
Security policy and procedure development transforms those assessment findings into actionable guidelines. We help you create policies that strike the right balance between security and usability. After all, the best security policy in the world is useless if your team can’t follow it in their daily work.
Compliance training ensures everyone on your team understands not just what to do, but why it matters. We’ve found that when people understand the reasoning behind security measures, they’re much more likely to accept them rather than try to work around them.
Documentation management might not sound exciting, but it’s absolutely crucial. Proper documentation proves you’re taking compliance seriously and makes audits much less stressful. We help you organize everything so you can find what you need when you need it.
Internal and external audits keep you on track. Internal audits are like practice runs—they help you identify and fix issues before external auditors arrive. When external audits do happen, you’ll be confident and prepared rather than scrambling to find documents at the last minute.
Incident response planning prepares you for the unexpected. Even with the best security measures, incidents can happen. Having a clear plan means you can respond quickly and effectively, minimizing damage and demonstrating to regulators that you take security seriously.
Vendor management extends your compliance efforts beyond your own walls. Your security is only as strong as your weakest link, and that includes the third-party services you rely on. We help you ensure your vendors meet the same high standards you’ve set for yourself.
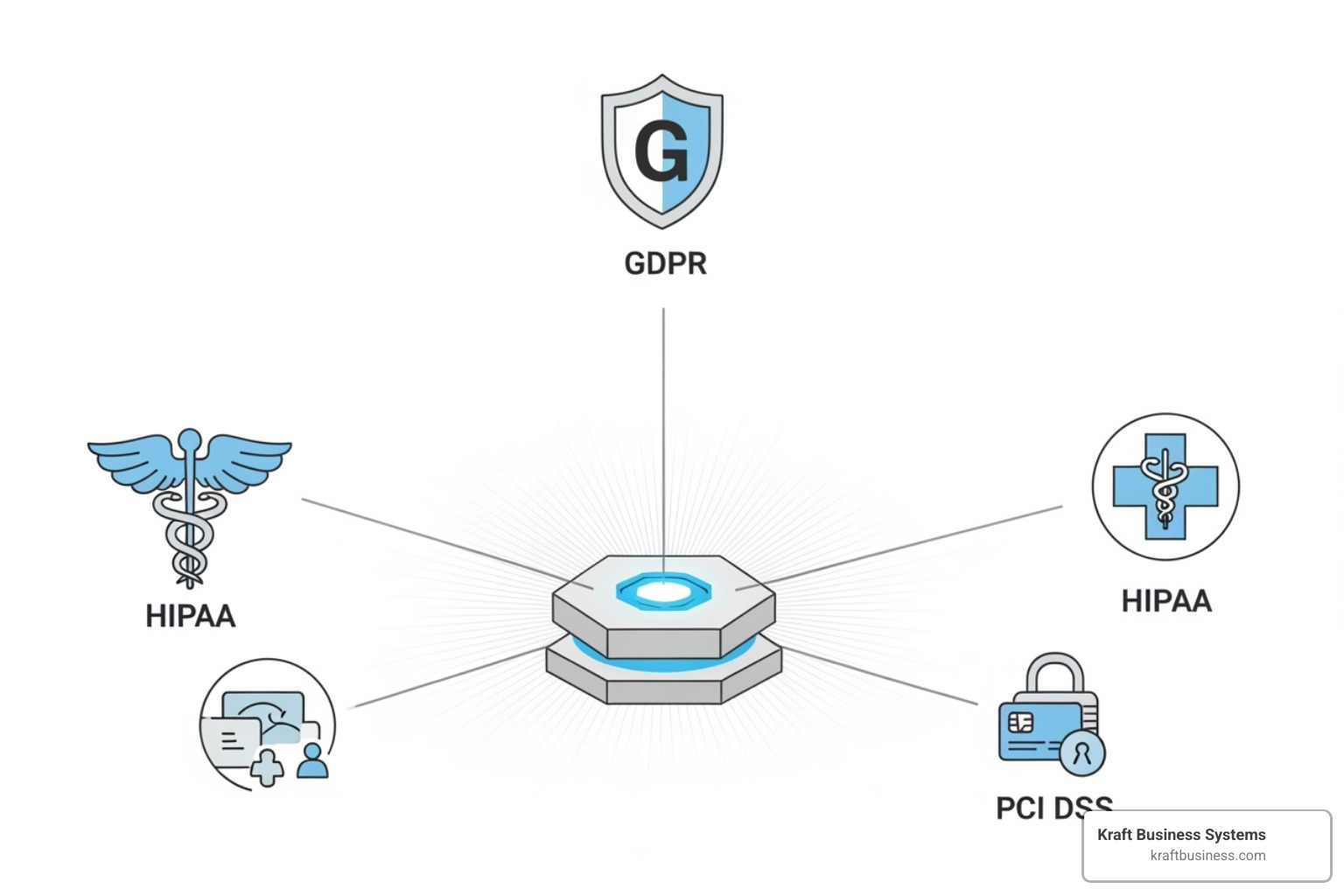
Common Regulatory Frameworks and Standards
The alphabet soup of compliance standards can make anyone’s head spin, but each one serves a specific purpose in protecting businesses and consumers. Understanding these frameworks helps you see the bigger picture of why compliance matters.
HIPAA protects healthcare information with the seriousness it deserves. If you handle protected health information, HIPAA compliance isn’t optional—it’s essential for maintaining patient trust and avoiding penalties that can reach into the millions.
PCI DSS keeps credit card information safe. Whether you’re a small retailer or a large e-commerce operation, if you process payments, PCI DSS compliance protects both you and your customers from fraud.
GDPR extends its protective reach far beyond European borders. Even Michigan businesses can find themselves subject to GDPR if they handle data from EU residents. The regulation’s focus on data processing purposes helps ensure personal information is used responsibly and transparently.
SOC 2 demonstrates your commitment to security, availability, and privacy. This certification is often required by enterprise clients and can open doors to new business opportunities that require high security standards.
CMMC is crucial for businesses working with the Department of Defense. This framework ensures that sensitive defense information receives the protection it deserves, helping maintain national security while enabling businesses to compete for valuable government contracts.
NIST Frameworks provide a flexible foundation that can adapt to various industries and business sizes. These guidelines from the National Institute of Standards and Technology offer a structured approach to cybersecurity that scales with your business needs.
Each framework addresses specific risks and requirements, but they all share a common goal: protecting valuable information and maintaining trust. At Kraft Business Systems, we help Grand Rapids area businesses steer these requirements, turning compliance from a burden into a competitive advantage.
The Strategic Business Benefits of Robust IT Compliance
Think of compliance as your business’s secret weapon rather than a regulatory burden. When you accept comprehensive IT compliance services, you’re not just checking boxes—you’re building a foundation for sustainable growth, operational excellence, and customer trust. It’s the difference between playing defense and taking control of your business’s future.
The most immediate benefit is risk mitigation. By identifying and addressing vulnerabilities before they become problems, you’re essentially building a protective shield around your business. This proactive approach saves you from the devastating costs of data breaches, cyberattacks, and operational disruptions that can cripple a business overnight.
Penalty avoidance might seem obvious, but the stakes are higher than many realize. With 60% of small businesses experiencing data breaches in 2023, the threat of hefty fines and legal consequences is very real. Our services ensure your activities align with legal requirements, dramatically reducing your risk of facing these costly consequences.
What surprises many business owners is how compliance actually improves operational efficiency. By streamlining processes, eliminating manual tasks, and standardizing security measures, we help optimize your IT operations. Your team spends less time on repetitive tasks and more time on what they do best—growing your business.
Here’s where it gets exciting: compliance can be your ticket to business growth. Many clients, especially larger enterprises and government entities, require their partners to meet strict security standards. Achieving certifications like SOC 2 or CMMC doesn’t just make you compliant—it makes you eligible for contracts and markets that were previously out of reach.
Customer loyalty follows naturally when people trust you with their data. In our current climate of constant data breaches, customers are increasingly selective about who they trust with their personal information. A strong compliance program signals that you take their privacy seriously, building the kind of trust that turns customers into advocates.
The competitive advantage is undeniable. Businesses with robust compliance programs stand out in their markets. They’re perceived as more reliable, secure, and professional. This reputation becomes a powerful differentiator when competing for new business.
More info about managed cybersecurity services can provide additional context on how a holistic approach strengthens your overall security posture and business resilience.
How IT Compliance Services Support Data Security and Privacy
Your data is your business’s most valuable asset, and protecting it requires more than good intentions. Our comprehensive IT compliance services create multiple layers of protection that work together to keep sensitive information secure and private.
Data encryption forms the foundation of our security approach. We implement robust encryption protocols for data both at rest and in transit. This means that even if unauthorized parties somehow access your data, it remains completely unreadable and useless to them. This protection is especially crucial for sensitive information like patient records under HIPAA regulations.
Access controls ensure that only the right people can view, modify, or transmit sensitive data. We establish multi-factor authentication and strong password policies that significantly reduce the risk of unauthorized access. But we go beyond basic access controls with role-based permissions—a system where individuals only access the specific data and systems necessary for their job functions.
Think of it this way: your finance team member won’t have access to patient medical records, and your healthcare staff won’t see financial data they don’t need. This principle of least privilege minimizes risk while maintaining operational efficiency.
Secure data storage protocols protect your information whether it lives on-premises or in cloud environments. We configure secure server settings, maintain regular system patches, and implement secure backup and disaster recovery solutions that ensure your data remains safe and accessible when you need it.
Proactive threat detection means we’re watching for problems before they become disasters. Our continuous monitoring looks for suspicious activities, vulnerabilities, and potential security threats, allowing us to respond quickly before issues escalate into major breaches.
Perhaps most importantly, we focus on employee security training because many data breaches start with human error. We provide comprehensive security awareness training that educates your team on phishing scams, social engineering tactics, and best practices for handling sensitive data. This transforms your employees from potential security risks into your first line of defense.
Our goal is building a culture of security where data protection becomes second nature throughout your organization. When security is a shared responsibility rather than just an IT concern, your entire business becomes more resilient and trustworthy.
How Compliance Drives Business Growth and Efficiency
Here’s where compliance gets really interesting—it’s not just about avoiding problems, it’s about creating opportunities. When approached strategically, comprehensive IT compliance services become a powerful engine that drives both business growth and operational efficiency.
Streamlined operations happen naturally when you implement compliance frameworks. These frameworks require structured processes and robust documentation, which helps us identify inefficiencies and eliminate redundant tasks. The result? Smoother workflows, clearer responsibilities, and improved productivity across your entire organization.
Eliminating manual tasks through automation is one of our favorite benefits to deliver. Modern compliance leverages tools and software that automate evidence collection, monitoring, and reporting. We’ve seen businesses achieve up to 90% faster evidence collection for audits, freeing up teams from tedious, repetitive work so they can focus on higher-value activities that actually grow the business.
Opening up new markets becomes possible when you achieve specific compliance certifications. Many industries—healthcare, finance, government contracting—require certifications like HIPAA, SOC 2, or CMMC before they’ll even consider working with you. These certifications don’t just meet requirements; they open up entirely new revenue streams that were previously inaccessible.
Winning contracts with enterprise clients becomes significantly easier when you can demonstrate robust compliance capabilities. Large organizations and government agencies have stringent security requirements for their vendors and partners. We’ve helped businesses win new clients and projects simply by being able to pass vendor information security requirements that their competitors couldn’t meet.
Building brand reputation and trust might be the most valuable long-term benefit. In an age where data breaches make headlines regularly, a proven commitment to data security and privacy sets you apart. Customers actively seek out businesses they perceive as secure and ethical, and they’re more likely to stay loyal once they find them.
The reduced business risk that comes with proactive compliance creates a stable foundation for innovation and expansion. When you’re not worried about fines, legal issues, or reputational damage, you can focus your energy and resources on growing your business with confidence.
The Role of Technology in Modern Comprehensive IT Compliance Services
Managing IT compliance manually is like trying to juggle flaming torches while riding a unicycle—technically possible, but why would you want to? Modern comprehensive IT compliance services rely heavily on technology to transform what was once a painful, error-prone process into something that actually works with your business instead of against it.
The technology landscape has completely changed how we approach compliance. Automation tools now handle the repetitive tasks that used to consume entire days of your team’s time. Instead of manually checking configurations and collecting evidence, these tools work around the clock, ensuring nothing slips through the cracks.
Compliance management software acts as your command center, bringing all your compliance activities into one place. Think of it as mission control for your regulatory requirements. These platforms track your progress across multiple frameworks simultaneously, manage all your documentation, and provide real-time visibility into your compliance status. We’ve watched businesses save hundreds of hours on compliance preparation thanks to these centralized systems.
The real game-changer is AI-powered solutions that can analyze massive amounts of data to spot patterns and predict potential compliance gaps before they become problems. Some of the most advanced platforms maintain real-time libraries covering regulatory obligations across over 150 global jurisdictions, using artificial intelligence to classify risks and keep you ahead of changes.
Centralized data management ensures you have a single source of truth for all compliance-related information. No more hunting through email chains or shared drives when an auditor asks for specific documentation. Everything lives in one secure, organized location.
Perhaps most importantly, real-time monitoring means compliance isn’t something you think about once a quarter. Your systems are continuously watching for configuration changes, access violations, or other compliance risks. When something needs attention, you know immediately rather than finding it during your next audit.
The speed improvement is remarkable. Automated evidence collection can gather audit materials up to 90% faster than manual processes. What used to take weeks of preparation can now happen in days or even hours.
Horizon scanning for regulatory changes keeps you informed about new requirements before they take effect. Technology monitors regulatory bodies and industry standards, alerting you to changes that might affect your business. This proactive approach means you’re never caught off guard by new compliance requirements.
Leveraging Automation for Comprehensive IT Compliance Services
Automation isn’t just a nice-to-have feature in modern compliance—it’s the difference between drowning in paperwork and actually having time to run your business. When we implement comprehensive IT compliance services, automation becomes the invisible workforce that keeps everything running smoothly.
Automated task tracking eliminates the sticky notes and spreadsheets that used to manage compliance activities. The system knows what needs to be done, when it’s due, and who’s responsible. Tasks don’t get forgotten, and nothing falls through the cracks because someone went on vacation.
Digital compliance checklists update themselves automatically when regulations change. Instead of wondering if you’re following the latest version of a standard, your checklist reflects current requirements. This dynamic approach means your compliance efforts are always aligned with the most recent guidance.
Continuous control validation is where automation really shines. Instead of periodic manual checks, your systems continuously verify that security controls are working correctly. Configurations are monitored, patches are tracked, and access rights are validated automatically. This real-time validation dramatically reduces your risk exposure.
Automated reporting for audits transforms the most stressful part of compliance into a simple process. When auditors request documentation, you can generate comprehensive reports with a few clicks. Executive summaries, detailed control evidence, and audit trails are all available instantly, saving countless hours of manual compilation.
Scalable patch management workflows ensure your systems stay current with security updates. These automated processes, often monitored around the clock, keep your infrastructure protected against known vulnerabilities without requiring constant manual intervention.
The biggest benefit is reduced manual effort and human error. When routine tasks are automated, your team can focus on strategic activities instead of repetitive compliance work. Plus, automation is consistent—it doesn’t have bad days or forget important steps.
Choosing the Right Technology Stack
Selecting the right technology for your compliance needs isn’t about finding the flashiest solution—it’s about choosing tools that work together seamlessly and actually make your life easier. When we help businesses across Michigan implement compliance technology, we focus on solutions that integrate naturally with how they work.
Integrated platforms are far more valuable than a collection of separate tools. When your compliance software talks to your security systems, which connect to your asset management tools, you get a complete picture of your compliance posture. This integration prevents the data silos that make compliance unnecessarily complicated.
Cloud-based solutions offer flexibility that on-premise systems simply can’t match. Your compliance data is accessible from anywhere, automatically backed up, and scales with your business needs. You don’t need to worry about server maintenance or software updates—the platform handles all of that behind the scenes.
Compatibility with existing infrastructure is crucial. The best compliance technology works with what you already have rather than forcing you to replace perfectly good systems. We carefully assess your current environment to ensure new solutions improve rather than disrupt your operations.
Real-time alerting capabilities keep you informed when attention is needed. Whether it’s a configuration change that affects compliance or a potential security incident, you’ll know immediately rather than finding issues weeks later. These alerts are designed to be informative, not overwhelming.
User-friendly dashboards make complex compliance data understandable at a glance. Your compliance status, key metrics, and progress toward goals are presented clearly, whether you’re a technical expert or a business leader who just needs to know if everything’s on track.
Support for multiple frameworks eliminates duplicate work. The same evidence and controls can often satisfy requirements for HIPAA, SOC 2, and other standards simultaneously. A versatile technology stack maps these relationships automatically, ensuring consistent compliance across all your regulatory obligations.
The right technology stack transforms compliance from a burden into a strategic advantage, providing clear visibility and automated processes that keep you compliant while freeing your team to focus on growing your business.
How to Implement and Maintain Your Compliance Strategy
Building a solid compliance foundation doesn’t have to feel like climbing Mount Everest without a guide. With the right approach and experienced partner, implementing comprehensive IT compliance services becomes a strategic journey that strengthens your business rather than slowing it down.
The implementation process follows a structured path, but it’s not a one-size-fits-all solution. Your business has unique challenges, whether you’re a growing healthcare practice in Grand Rapids or a manufacturing company in Lansing. That’s why choosing the right provider matters so much – they become your guide through the regulatory landscape.
Many businesses, especially smaller organizations, find that a vCISO (Virtual Chief Information Security Officer) service offers the perfect balance. Instead of hiring a full-time security executive, you get access to seasoned leadership that can translate complex frameworks into clear, actionable steps. A vCISO helps bridge the gap between technical requirements and business priorities, ensuring your compliance strategy actually makes sense for your organization. Explore our IT solutions to see how this expertise integrates seamlessly with your broader technology strategy.
The key insight we’ve learned after years of helping Michigan businesses is that ongoing compliance isn’t just about checking boxes – it’s about building systems that adapt as regulations evolve. This means your strategy needs to be living and breathing, not gathering dust on a shelf.
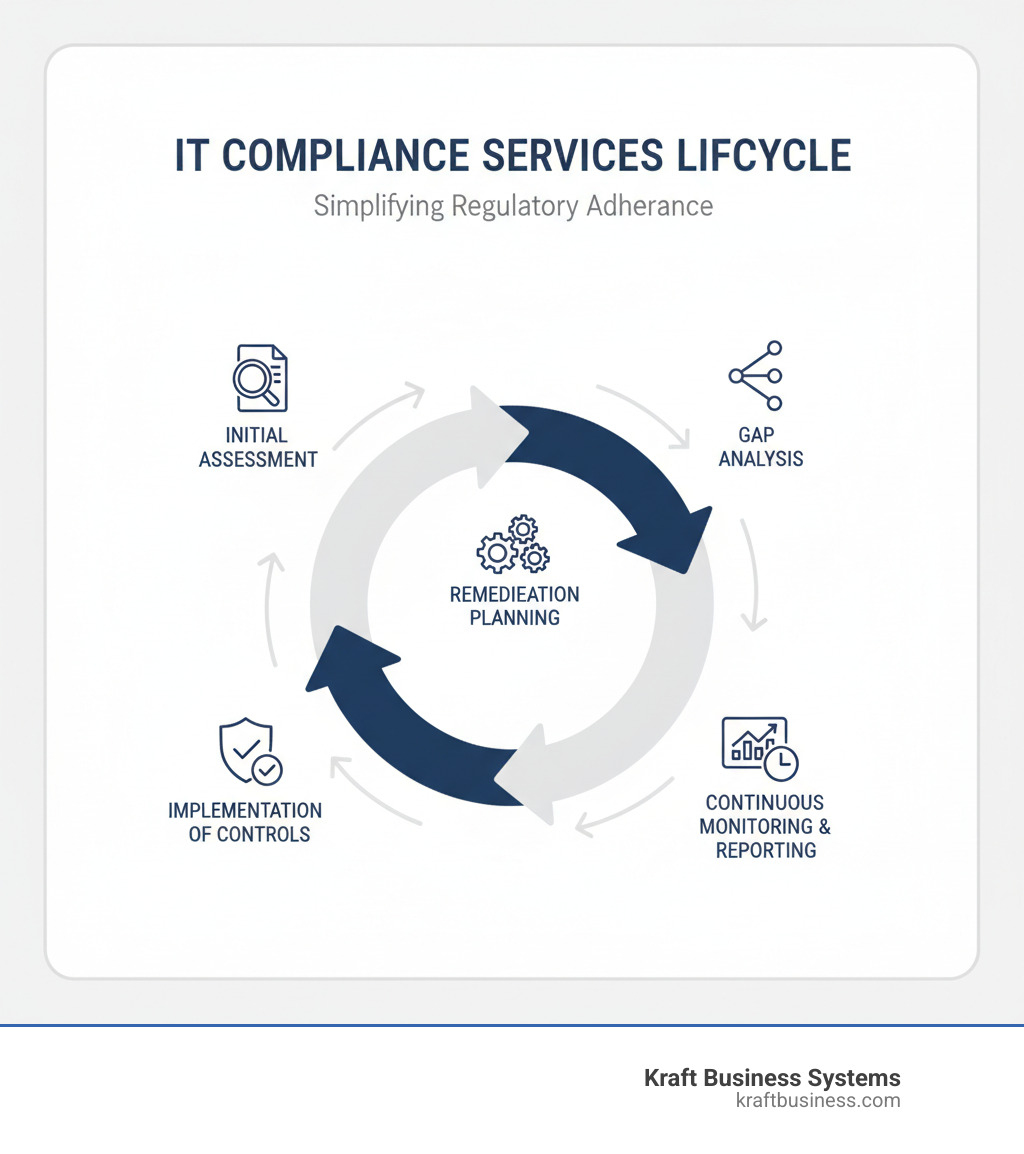
The Typical Process for Implementing Comprehensive IT Compliance Services
Think of implementing comprehensive IT compliance services like renovating your home – you need a clear plan, the right tools, and someone who knows where all the electrical wires are hidden. Our structured approach takes the mystery out of compliance, breaking down what can seem like an overwhelming project into manageable phases.
The journey begins with an Initial Assessment, where we dive deep into your current IT infrastructure, data handling practices, and existing policies. This isn’t just a surface-level review – we’re looking at everything from how your team accesses sensitive files to where your backup data lives. Understanding your current state and specific requirements gives us the foundation for everything that follows.
Next comes the Gap Analysis, which is where things get interesting. We compare your current practices against the specific requirements of relevant regulatory frameworks like HIPAA, PCI DSS, or SOC 2. This step often surprises business owners – sometimes you’re closer to compliance than you think, and other times there are gaps you never knew existed. We pinpoint exactly where your organization needs attention and what the priorities should be.
Armed with this knowledge, we develop a Remediation Roadmap that’s both realistic and strategic. This isn’t a generic checklist – it’s a customized plan that considers your budget, timeline, and business priorities. We prioritize the most critical gaps first, ensuring you get the biggest security improvements while working toward full compliance.
The Implementation phase is where the real change happens. We work alongside your team to deploy new security controls, update policies, and implement technological solutions. But here’s what many providers miss – we also focus heavily on training your staff. The best security controls in the world won’t help if your team doesn’t understand how to use them properly.
Finally, Ongoing Monitoring & Auditing ensures your compliance efforts don’t become yesterday’s news. We establish systems for continuous monitoring, conduct regular compliance checks, and prepare you for both internal and external audits. We typically recommend quarterly compliance reviews with more comprehensive annual assessments to keep everything current and audit-ready.
How to Choose the Right IT Compliance Service Provider
Choosing a compliance partner is a bit like choosing a doctor – you want someone with the right expertise, a proven track record, and the ability to explain complex topics in plain English. The wrong choice can leave you vulnerable, while the right partner becomes an extension of your team.
Industry-specific expertise should be your first consideration. A provider who understands your sector’s unique challenges will speak your language from day one. If you’re in healthcare, they should know HIPAA inside and out. If you’re a DoD contractor, CMMC should be second nature to them. At Kraft Business Systems, we’ve spent years serving diverse sectors across Michigan, from manufacturing companies in Flint to healthcare practices in Grand Rapids, which gives us deep insight into industry-specific requirements.
A proven track record tells you everything about reliability and quality. Look for metrics that matter – client retention rates (we maintain a 97% client retention rate since 2003), positive reviews (our EXCELLENT rating is based on 67 reviews), and years of combined experience (our team brings over 100 years of combined expertise). These numbers aren’t just marketing fluff – they represent real businesses that trust their compliance to this provider year after year.
Scalability becomes crucial as your business grows. Your compliance needs will evolve, regulations will change, and your technology environment will expand. The right provider adapts with you, whether you’re a startup in Grand Rapids or an expanding enterprise with locations across Michigan. You don’t want to outgrow your compliance partner in two years.
Modern compliance demands technology and automation capabilities. Providers who leverage advanced automation tools, compliance management software, and AI-powered solutions deliver faster results – sometimes up to 90% faster evidence collection – and more accurate monitoring. This isn’t just about efficiency; it’s about reducing the manual burden on your team.
Communication and support can make or break the relationship. Compliance involves complex topics, but your provider should explain everything in terms that make sense for your business. You want a partner who responds promptly, provides clear updates, and treats you like a valued client, not just another account number.
The best providers understand that alignment with business objectives matters more than technical perfection. They view compliance as an opportunity to improve your security posture, streamline operations, and even drive business growth. They’re not just checking regulatory boxes – they’re helping you build a stronger, more resilient organization.
For Michigan businesses, having a local presence offers unique advantages. A provider who understands the local business environment can offer personalized, on-site support when you need it most. Whether you’re in Ann Arbor, Traverse City, or Wyoming, having someone who can be there in person makes a real difference when challenges arise.
The right compliance partner doesn’t just implement systems and walk away – they become invested in your long-term success, ensuring your compliance strategy evolves with your business and the regulatory landscape.
Frequently Asked Questions about IT Compliance Services
When businesses first explore comprehensive IT compliance services, they often have similar concerns and questions. We’ve been helping companies across Michigan steer these waters for over two decades, so we understand the hesitation and curiosity that comes with this important decision.
Let’s address the most common questions we hear from business owners who are considering taking this crucial step for their organization.
How long does it take to become IT compliant?
This is probably the first question on every business owner’s mind, and honestly, it’s like asking “how long is a piece of string?” The timeline varies significantly based on several key factors.
For smaller businesses with relatively straightforward IT environments and some existing security measures, achieving compliance for a specific framework like PCI DSS might take just 2-6 weeks. We’ve helped many Grand Rapids businesses get their compliance house in order surprisingly quickly when they have a solid foundation to build upon.
Larger enterprises or organizations tackling multiple frameworks simultaneously are looking at a different timeline entirely. A comprehensive compliance program addressing HIPAA, SOC 2, and NIST standards could take several months to fully implement. The complexity increases when you’re dealing with multiple locations, diverse systems, and extensive documentation requirements.
The good news? Our initial assessment gives you a realistic timeline custom to your specific situation. We don’t believe in cookie-cutter approaches or unnecessary complexity. Every business is different, and we focus on practical, business-friendly solutions that get you compliant efficiently without disrupting your operations more than necessary.
Will implementing IT compliance solutions slow down my team?
This concern comes up in nearly every conversation we have with potential clients, and we completely understand why. Nobody wants to implement security measures that turn their efficient team into frustrated employees fighting with cumbersome systems all day.
Here’s the reality: well-designed compliance solutions should actually improve productivity, not hinder it. When we implement comprehensive IT compliance services, we’re not just throwing up roadblocks and calling it security. We’re streamlining processes, automating repetitive tasks, and creating secure pathways that make your team’s work easier and more efficient.
Think about it this way – instead of manually tracking security updates or spending hours preparing for audits, automated systems handle the heavy lifting. Your team gets secure, efficient access to everything they need without the friction of poorly implemented security measures.
Our approach focuses on protecting your business while maintaining productivity. We implement solutions that work with your team’s natural workflow, not against it. The goal is simple: robust security that feels invisible to daily operations while providing rock-solid protection for your data and systems.
How do IT compliance services help businesses avoid penalties?
The penalties for non-compliance can be absolutely devastating for businesses of any size. We’re talking about fines that can reach into the millions, legal fees that pile up quickly, and reputational damage that takes years to repair.
Our comprehensive IT compliance services work as a proactive shield against these risks. We start with thorough risk assessments that uncover potential issues before they become expensive problems. It’s much easier and cheaper to fix a compliance gap during a routine review than after a regulator finds it during an investigation.
Continuous monitoring is another crucial piece of the puzzle. Compliance isn’t a “set it and forget it” situation – regulations change, new threats emerge, and business operations evolve. Our systems keep a constant watch on your compliance status, alerting us immediately if something drifts out of alignment.
We also maintain audit-ready documentation at all times. When regulators come knocking (and they will eventually), having organized, comprehensive documentation readily available demonstrates your commitment to compliance. This preparation often means the difference between a routine audit and a lengthy, expensive investigation.
Perhaps most importantly, we keep your business updated on regulatory changes as they happen. The regulatory landscape shifts constantly, and what was compliant last year might not meet this year’s standards. By staying ahead of these changes, we ensure your business never falls behind the curve.
The result? A robust compliance program that creates a strong defense against violations and the costly penalties that follow. It’s not just about avoiding fines – it’s about building a foundation of trust and reliability that supports long-term business growth.
Conclusion: Turn Compliance into Your Competitive Edge
Comprehensive IT compliance services are more than just a regulatory requirement—they’re a foundation for building a resilient, efficient, and trustworthy business. By changing compliance into a strategic framework for operational excellence, you can safeguard critical data, improve your reputation, and open up new opportunities for growth.
The change begins when you stop viewing compliance as a burden and start seeing it as an opportunity to streamline operations. Well-designed compliance programs eliminate inefficiencies, automate tedious tasks, and create clear processes that actually make your team more productive. Instead of slowing down your business, the right approach to comprehensive IT compliance services becomes an engine for growth.
Building customer trust is perhaps one of the most valuable outcomes of robust compliance. Where data breaches make headlines regularly, customers actively seek businesses they can trust with their sensitive information. When you can demonstrate strong compliance credentials—whether it’s HIPAA for healthcare data, PCI DSS for payment processing, or SOC 2 for service delivery—you’re not just meeting requirements. You’re showing customers that their security matters to you.
Opening doors to new markets is another powerful benefit that many businesses find. Government contracts often require CMMC certification. Enterprise clients frequently mandate SOC 2 compliance. Healthcare partnerships need HIPAA adherence. Each certification you achieve doesn’t just check a box—it open ups revenue opportunities that weren’t available before.
For businesses in Grand Rapids and across Michigan, partnering with an experienced provider like Kraft Business Systems can simplify this journey, ensuring your technology is a secure asset that drives you forward. With our local presence and deep understanding of Michigan’s business landscape, we’re not just another vendor—we’re your neighbors, committed to your long-term success.
The reality is that compliance will only become more important as regulations evolve and cyber threats grow. The businesses that thrive will be those that accept this reality and turn regulatory requirements into competitive advantages. They’ll be the ones with streamlined operations, loyal customers, and access to the most lucrative markets.
Don’t let compliance be a source of stress or confusion. Instead, let it become the foundation for a stronger, more secure, and more profitable business. Contact us today to schedule a technology review and find how our comprehensive IT compliance services can transform your approach to security and growth.