AI Overview:
In today’s digital-first world, cyber threats and compliance requirements evolve faster than most businesses can keep up. Small and mid-sized companies, once overlooked by attackers, are now prime targets for ransomware, phishing, and cloud misconfigurations. Meanwhile, failing to meet regulatory standards like HIPAA, PCI DSS, or GDPR can mean crippling fines and loss of customer trust.
That’s where IT security and compliance services come in—helping businesses stay secure, compliant, and audit-ready without the overwhelming burden of doing it all in-house.
Why IT Security and Compliance Services Are Essential for Modern Businesses
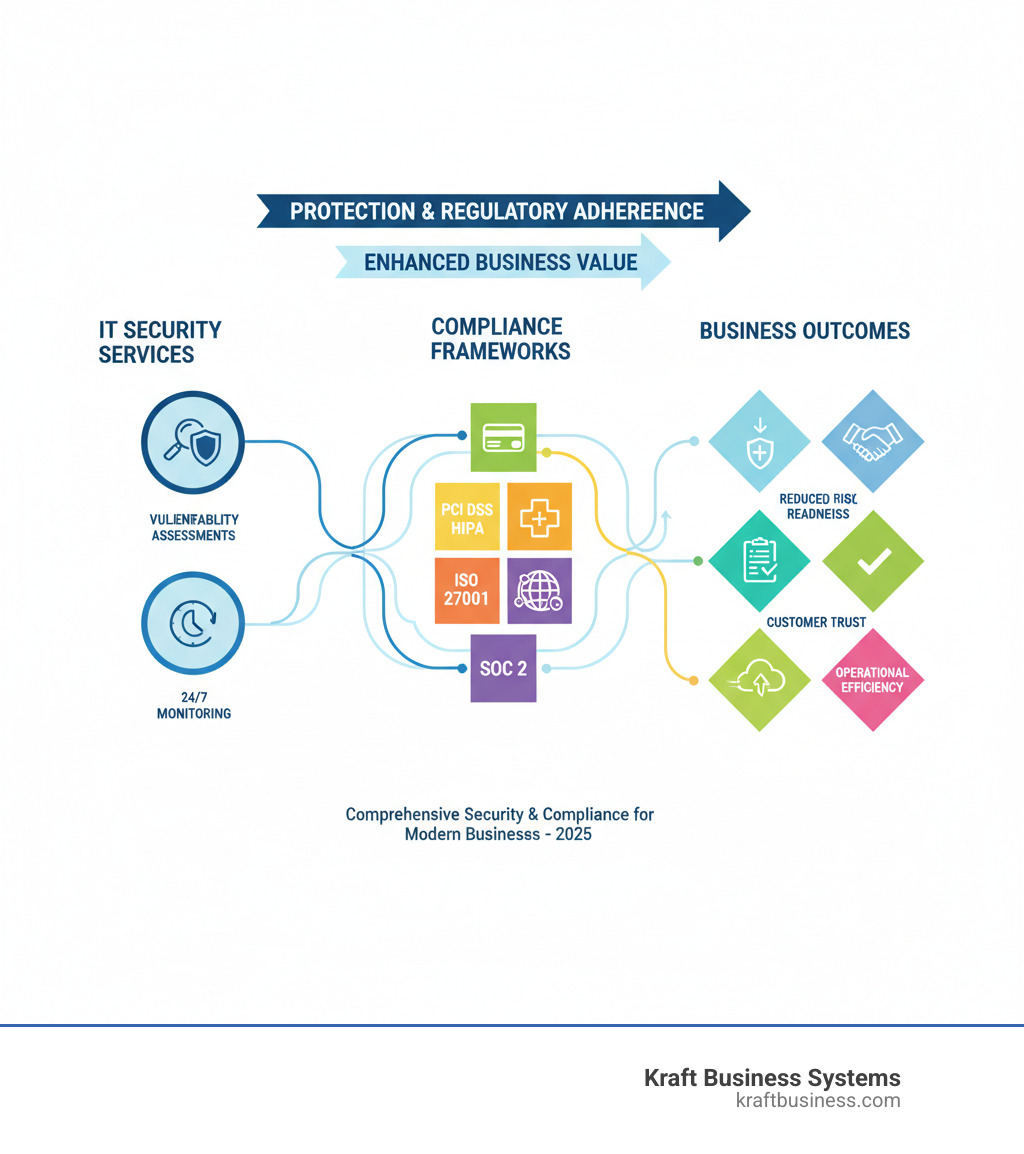
IT security and compliance services help businesses protect against cyber threats while meeting regulatory requirements. Here’s what you need to know:
Core Services Include:
- Security Assessments – Vulnerability testing, penetration testing, risk analysis
- Compliance Management – Framework alignment (PCI DSS, HIPAA, ISO 27001), audit preparation
- Ongoing Protection – 24/7 monitoring, threat detection, incident response
- Strategic Guidance – Virtual CISO services, policy development, security training
Key Benefits:
- Reduce cyber risk and prevent costly breaches
- Simplify complex compliance requirements
- Access expert knowledge without hiring full-time staff
- Stay audit-ready year-round
Let’s be honest – cybersecurity and compliance can feel like a foreign language. One day you’re running your business, the next you’re drowning in acronyms like SOC 2, PCI DSS, and NIST frameworks.
But here’s the reality: cybercrime costs are growing by 15% per year, and 71% of data breaches happen to small businesses. Meanwhile, compliance violations can trigger hefty fines and destroy customer trust.
The good news? You don’t need to become a cybersecurity expert overnight. IT security and compliance services exist to handle this complexity for you – from protecting against threats to preparing for audits.
This guide breaks down exactly what these services include, which compliance standards matter for your business, and how the right partner can turn security from a headache into a competitive advantage.
Handy it security and compliance services terms:
Why Security and Compliance Matter for Every Business
Picture this: You’re running your business smoothly when suddenly, your systems lock up with a ransom demand on every screen. Or maybe you get a letter from auditors demanding proof of compliance with regulations you’ve barely heard of. Sound like a nightmare? For many business owners, it’s becoming reality.
Cyber threats are evolving at breakneck speed, and they’re not just targeting big corporations anymore. Sophisticated ransomware attacks can encrypt your entire business in minutes. Phishing schemes are so convincing they fool even tech-savvy employees. And the numbers don’t lie – with cybercrime costs growing by 15% annually and 71% of small businesses experiencing breaches, no company is too small to be a target. The aftermath? Data loss, financial devastation, and customers who’ll never trust you again. You can read more about the impact of data breaches to see just how serious this gets.
But here’s what makes it even trickier – regulations are complex and constantly changing. One day you’re compliant, the next day there’s a new rule about how you handle customer data. It’s like trying to hit a moving target while blindfolded.
Most businesses, especially smaller ones, simply don’t have the in-house expertise to handle this complexity. Hiring a full-time cybersecurity expert or Chief Information Security Officer can cost more than many companies’ entire IT budgets. Yet the alternative – going without proper protection – can be catastrophic.
Non-compliance isn’t just a slap on the wrist either. PCI DSS violations alone can cost $5,000 to $10,000 per month until you fix the issues. Beyond the fines, a single breach can destroy years of customer trust and shut down operations for days or weeks.
Top Security and Compliance Challenges
From our work with businesses across Grand Rapids, Traverse City, and Detroit, we see the same pain points everywhere. Advanced cyberattacks are hitting companies of all sizes because criminals know smaller businesses often have weaker defenses but still valuable data.
The shift to remote and hybrid work has made everything more complicated. Suddenly, your sensitive business data is being accessed from home networks, coffee shops, and co-working spaces – each one a potential entry point for attackers.
Cloud and SaaS vulnerabilities add another layer of complexity. As more business operations move online, a single misconfiguration can expose everything. Many companies don’t even realize how much sensitive data they have scattered across different cloud services.
Meanwhile, keeping up with regulatory changes feels like a full-time job. GDPR, HIPAA, PCI DSS – these aren’t static rules you learn once. They evolve, and you need to evolve with them or face consequences.
Perhaps most stressful of all is demonstrating compliance to auditors and clients. It’s not enough to have good security – you need to prove it with documentation, reports, and evidence that can take months to compile.
How IT Security and Compliance Services Help
This is where IT security and compliance services become your lifeline. Instead of playing defense against threats you can’t see coming, these services shift you into proactive threat detection and response mode. Imagine having a security team watching your systems 24/7, catching problems before they become disasters.
Professional services excel at identifying and closing security gaps you didn’t even know existed. Through comprehensive assessments, they map out exactly where you’re vulnerable and provide clear, actionable steps to fix those weaknesses.
The goal isn’t just to patch holes – it’s about building a defensible security posture that can withstand whatever comes next. This means creating multiple layers of protection so that if one fails, others are there to catch potential threats.
Most importantly, these services focus on protecting your sensitive data and business assets – the customer information, financial records, and intellectual property that make your business valuable. When these are secure, you can focus on what you do best: running your business.
Learn more about managed cybersecurity services and find how the right partner can transform security from your biggest worry into your competitive advantage.
What Do IT Security and Compliance Services Include?
Think of IT security and compliance services as your all-in-one security department – minus the hefty overhead. A comprehensive provider walks alongside you from that first security check-up all the way through to round-the-clock protection. It’s like having a team of cybersecurity experts on speed dial, ready to jump in whenever you need them.
The beauty of these services lies in their layered approach. Rather than throwing random security tools at the wall and hoping something sticks, professional providers create a coordinated defense strategy that grows with your business. Let’s break down what this actually looks like in practice.
Core Assessments and Testing
Before a doctor prescribes treatment, they need to understand what’s wrong. The same principle applies to cybersecurity. Vulnerability assessments serve as your IT system’s annual physical exam. Our team scans your networks, applications, and systems to uncover known security weaknesses before the bad guys find them. It’s detective work that reveals exactly where your digital doors might be open uped.
But knowing where the weak spots are is just the beginning. Penetration testing takes things a step further by actually testing those vulnerabilities. Think of it as hiring friendly burglars to try breaking into your house – they’ll show you exactly how someone could get in and what they could steal once inside. These ethical hackers simulate real-world attacks, giving you a crystal-clear picture of your actual risk level.
Risk assessments zoom out to look at the bigger picture. They combine detective work with strategic thinking, helping you understand not just what could go wrong, but how likely it is and what the real-world impact would be on your business. This isn’t about creating fear – it’s about making smart decisions with limited resources.
Your written policies matter just as much as your technical defenses. A Policies, Procedures, and Practices Assessment (PPPA) ensures your documented IT policies actually align with best practices and regulatory requirements. It’s often the crucial first step toward achieving compliance with standards like HIPAA, SOC, PCI, and NIST.
Since humans are often the weakest link in any security chain, social engineering testing checks how your team responds to phishing emails, suspicious phone calls, and other manipulation tactics. The results help identify who needs additional training and strengthen your human firewall. Meanwhile, Web Application Security Assessment (WASA) focuses specifically on the web applications your business relies on daily, ensuring they can’t be exploited by attackers.
Strategic Planning and Policy Development
Finding problems is only half the battle – you also need a roadmap for fixing them and preventing future issues. This is where strategic planning becomes invaluable.
For many Michigan businesses, hiring a full-time Chief Information Security Officer simply isn’t realistic. Virtual CISO (vCISO) services bridge this gap beautifully. A vCISO provides expert cybersecurity leadership on demand, helping you build compliance roadmaps, align security risks with business priorities, and handle audits without the full-time salary expense. As Forbes noted, this approach is becoming increasingly popular among small and medium-sized businesses looking for budget-friendly expert guidance.
Good security starts with clear rules that everyone understands. Security policy creation and review ensures your team knows exactly what’s expected of them. These aren’t dusty documents that sit in a drawer – they’re living guidelines that reflect current best practices and regulatory requirements.
Nobody wants to think about worst-case scenarios, but incident response planning ensures you’re ready when something goes wrong. A well-crafted plan outlines exactly who does what during a security incident, minimizing damage and getting you back to business as quickly as possible. Similarly, business continuity and disaster recovery strategy preparation extends beyond cybersecurity to cover natural disasters, power outages, and other disruptions that could bring your operations to a halt.
Ongoing Monitoring and Management
Security isn’t a “set it and forget it” proposition – it requires constant vigilance. The threat landscape changes daily, and your defenses need to evolve accordingly.
24/7 security monitoring means cyber threats are met with immediate response, regardless of when they occur. Our team watches your systems around the clock, looking for suspicious activity while you focus on running your business. This continuous surveillance feeds into our Security Operations Center (SOC), where security experts analyze threats and coordinate responses from a centralized location.
SIEM (Security Information and Event Management) technology acts like a security nerve center, collecting and analyzing data from across your entire IT environment. It provides a bird’s-eye view of your security posture and alerts our team to potential threats in real time. Managed Detection and Response (MDR) services go beyond simple alerts by providing expert analysis, active threat hunting, and rapid response to security incidents.
The unglamorous but critical work of patch management and updates ensures your software stays current with the latest security fixes. Our team manages this process systematically, deploying patches and updates through automated workflows monitored 24/7 by our Cyber Fusion Center. Endpoint protection rounds out the defensive strategy by securing every device connected to your network – from laptops and desktops to servers and mobile devices.
This comprehensive approach transforms security from a reactive headache into a proactive business advantage. Explore more IT solutions that can strengthen your overall business operations and give you the peace of mind you deserve.
Making Compliance Simple: How to Achieve and Maintain It
Let’s face it – compliance feels like navigating a maze blindfolded. One wrong turn and you’re facing hefty fines, failed audits, or worse. But here’s the thing: it security and compliance services can turn that confusing maze into a clear, well-lit path to success.
The secret isn’t working harder during audit season (nobody wants those sleepless nights). It’s about making compliance a natural part of your daily operations. Think of it like maintaining your car – regular oil changes are much easier than rebuilding the engine after it breaks down.
Continuous Monitoring and Proactive Defense
Remember when compliance meant frantically gathering documents once a year? Those days are over. Modern it security and compliance services work around the clock, so you don’t have to.
Real-time threat detection and response means we’re watching your systems 24/7, catching problems before they become disasters. Instead of finding out about a security issue during your annual audit, we identify and fix threats as they emerge. It’s like having a security guard who never takes a coffee break.
Full asset visibility and coverage ensures we know about every device, application, and system in your environment. You can’t protect what you can’t see, so we maintain 100% visibility across your on-premises systems and cloud infrastructure. This complete picture makes compliance reporting much more accurate and comprehensive.
Reducing attack surfaces happens naturally when you’re monitoring continuously. We don’t just wait for hackers to find vulnerabilities – we actively hunt them down and eliminate them. This proactive approach makes your business less attractive to cybercriminals and helps you maintain compliance standards more easily.
The shift from reactive to proactive security changes everything. Instead of scrambling to respond after something goes wrong, you’re preventing problems before they start. This approach aligns perfectly with frameworks like the NIST Cybersecurity Framework, which emphasizes prevention and continuous improvement.
Streamlining Audit Preparation
Nobody enjoys audit season, but it doesn’t have to be a nightmare. With the right approach, audits become routine check-ins rather than stressful ordeals.
Automated evidence collection can speed up your audit preparation by up to 90%. Instead of manually hunting through files and systems, automated platforms continuously gather and organize the documentation auditors need. It’s like having an incredibly organized assistant who never loses track of important papers.
Centralized compliance documentation means everything lives in one place. No more frantic searching through different systems or wondering if you have the latest version of a policy. When auditors ask for something, you know exactly where to find it.
Gap analysis and readiness assessments happen regularly, not just before audits. We continuously compare your current security posture against regulatory requirements, identifying issues while there’s still time to fix them. Think of it as practice tests that help you ace the real exam.
The ultimate goal is staying “audit-ready” year-round. When compliance becomes part of your daily routine rather than an annual crisis, audits transform from stressful events into routine conversations. You’ll sleep better knowing that whenever auditors call, you’re ready for them.
Understanding Key Compliance Standards
The compliance world can feel like alphabet soup—PCI DSS, HIPAA, CMMC, SOC 2, GDPR. Each acronym represents a set of rules designed to protect specific types of data, but they all share one thing in common: they’re essential for maintaining trust and avoiding hefty penalties.
This section demystifies common regulations and shows how a trusted provider helps you meet them without the confusion and stress.
Major Compliance Frameworks at a Glance
Think of compliance frameworks as different types of security blueprints. Each one protects specific information and applies to different industries. Here’s a quick comparison of the three most common ones:
| Framework | Who It Applies To | What It Protects | Key Requirements |
|---|---|---|---|
| PCI DSS | Businesses handling payment cards | Cardholder data | Secure storage, regular testing, network segmentation, strong access control, data encryption |
| HIPAA | Healthcare providers, insurers, and business associates | Patient health info (ePHI) | Privacy, security, breach notification, administrative, physical, and technical safeguards |
| CMMC | Defense contractors and their supply chain | Controlled Unclassified Information (CUI) | Maturity levels (1-5), ranging from basic cyber hygiene to advanced persistent threat protection, access controls, incident response |
Other Important Standards
Beyond these big three, several other standards might apply to your business depending on your industry and customer base.
PCI DSS for payment security affects virtually any business that accepts credit or debit cards. Whether you’re a small retail shop in Grand Rapids or a growing e-commerce company, if you handle cardholder data, PCI DSS compliance is mandatory. The good news? Our PCI-Qualified Security Assessors (QSAs) can guide you through the requirements, including self-assessment questionnaires and attestations of compliance, making the annual process much more manageable.
HIPAA for healthcare data governs how medical information is protected. If you’re a healthcare provider, health plan, or even a business associate who handles protected health information (PHI), HIPAA compliance isn’t optional—it’s the law. The HITECH Act strengthened these requirements, making IT security and compliance services even more critical for healthcare organizations.
ISO 27001 for information security management is an international gold standard that demonstrates your commitment to robust security practices. Unlike some compliance requirements that focus on specific data types, ISO 27001 looks at your entire information security management system. Achieving certification can open doors with clients who require this level of security assurance.
CMMC for defense supply chain is particularly relevant for Michigan businesses involved in defense contracting. As a Registered Practitioner Organization accredited by the CMMC Accreditation Board, we understand the unique challenges of this framework. CMMC uses a maturity model approach, with five levels ranging from basic cyber hygiene to protection against advanced persistent threats.
SOC 2 for service organizations comes into play if your business provides services to other companies and stores their data in the cloud. This framework focuses on five trust principles: security, availability, processing integrity, confidentiality, and privacy. It’s become increasingly important as more businesses rely on cloud-based service providers.
GDPR for data privacy extends far beyond European borders. If your business processes personal data of EU citizens—even if you’re based in Michigan—GDPR requirements may apply. This regulation emphasizes individual rights over personal data and requires explicit consent for data processing.
Our security experts bring decades of experience with various standards including NIST, GLI-33, and WLA-SCS: 2020. We’ve learned that each organization’s compliance journey is unique, shaped by their industry, size, and specific business requirements. That’s why our IT security and compliance services are designed to meet you where you are, providing the exact level of support you need to achieve and maintain compliance without overwhelming your team or budget.
Building a Resilient, Trustworthy Business
Here’s something many business owners don’t realize: security and compliance aren’t just about avoiding risk—they’re powerful tools that enable innovation, build deeper customer trust, and create real competitive advantages. When your business is truly resilient, it doesn’t just survive challenges; it thrives through them.
Think about it this way: would you rather spend your time worrying about whether your systems are secure, or would you prefer to focus on growing your business knowing your digital foundation is rock-solid? That’s the difference IT security and compliance services can make.
Empowering Your Team: The Human Element
Even the most sophisticated firewalls and monitoring systems can’t protect against one thing: human error. But here’s the good news—your employees can become your strongest line of defense with the right approach.
Security awareness training transforms your team from potential vulnerabilities into security champions. We’re not talking about boring annual videos that everyone clicks through while checking email. Effective training makes cybersecurity relevant and engaging, teaching employees to spot phishing emails, understand why strong passwords matter, and know exactly what to do when something seems suspicious.
The results speak for themselves. After implementing comprehensive training programs, we consistently see 80% of employees report feeling more aware of cybersecurity and their role in protecting their company. That’s not just a feel-good statistic—it translates to real protection.
Phishing simulations and drills take this training from theory to practice. By sending harmless test phishing emails, we help employees recognize threats in a safe environment where mistakes become learning opportunities rather than security breaches. The improvement is dramatic: average phishing success rates drop from 25% to less than 8% after consistent training and simulations.
But the real magic happens when you foster a security-first culture throughout your organization. When employees understand that security isn’t just IT’s job—it’s everyone’s responsibility—they start making better decisions naturally. They think twice before clicking links, they report suspicious activity promptly, and they become active participants in keeping your business safe.
This human-centered approach to security delivers measurable results. Beyond the dramatic reduction in phishing success rates, many of our clients see return on investment in less than a year through reduced help desk tickets and fewer security incidents that require IT intervention.
Choosing the Right IT Security and Compliance Partner
Deciding to partner with a managed service provider for your security and compliance needs is smart business, especially for Michigan companies who want to focus on what they do best. But not all providers are created equal.
Proven experience and expertise should be your starting point. Look for partners with strong track records and relevant certifications in the frameworks that matter to your business. If you’re a healthcare provider in Grand Rapids or a manufacturer in Lansing, does your potential partner understand the unique compliance challenges you face?
Industry-specific knowledge makes all the difference. A provider who’s helped businesses like yours steer PCI DSS requirements or HIPAA compliance will understand your pain points and can offer practical, tested solutions rather than generic advice.
You’ll also want scalable, flexible service offerings that can grow with your business. Maybe you need a full virtual CISO service today, or perhaps targeted vulnerability assessments are the right starting point. The best partners meet you where you are and evolve their services as your needs change.
Don’t overlook the importance of a modern technology stack. Your partner should leverage cutting-edge security tools and platforms for monitoring, threat detection, and compliance management. After all, you’re partnering with them partly to access technology and expertise you couldn’t afford to build in-house.
Most importantly, look for a collaborative, partnership-focused approach. You want someone who communicates clearly, understands your business goals, and works alongside your internal team rather than operating in isolation. Positive client feedback and testimonials from businesses similar to yours can give you confidence you’re making the right choice.
How IT Security and Compliance Services Contribute to a Business’s Overall Resilience and Ability to Innovate
Here’s where things get exciting. Far from being a cost center that slows you down, robust IT security and compliance services actually accelerate your business growth and innovation capacity.
Improved resilience means your business can weather any storm. When cyber incidents occur—and they will—a resilient organization detects them faster, responds more effectively, and recovers quickly with minimal downtime. Your operations continue smoothly, your customers remain served, and your reputation stays intact.
Increased trust and reputation open doors you might not even know existed. Customers, partners, and investors increasingly evaluate businesses based on their security posture and compliance adherence. When you can demonstrate strong protections, you differentiate yourself from competitors and build the trust that leads to stronger relationships and new opportunities.
Perhaps most importantly, security and compliance give you the freedom to innovate. When you’re confident in your security foundation, you’re more willing to explore new technologies, adopt cloud solutions, and pursue digital change initiatives. Instead of asking “What could go wrong?” you can focus on “What’s possible?”
This confidence becomes a genuine competitive advantage. Businesses that prioritize security and compliance are often seen as more reliable and professional. This perception is especially valuable in regulated industries or when working with larger clients who demand stringent security standards from their partners.
By investing in comprehensive IT security and compliance services, you’re not just protecting your business—you’re empowering it to grow, adapt, and thrive in our increasingly digital world. That’s the kind of foundation every successful business needs.
Frequently Asked Questions (FAQ)
Let’s tackle the most common questions we hear from business owners in Grand Rapids and across Michigan about IT security and compliance services. These are the real concerns that keep people up at night – and the good news is, they all have straightforward answers.
What's the difference between IT security and IT compliance?
Think of IT security as your digital bodyguard - it's all the practical stuff you do to protect your systems and data from the bad guys. We're talking firewalls, antivirus software, encryption, and monitoring tools that actively defend against threats like hackers, malware, and data breaches.
IT compliance, on the other hand, is about following the rules. It's meeting those specific legal and regulatory requirements that govern how you must handle certain types of data. Whether it's HIPAA for healthcare information, PCI DSS for credit card data, or GDPR for customer privacy, compliance is about proving you're doing what the law requires.
Here's a simple way to remember it: security is the "how" you protect your business, while compliance is the "what" you're required to protect. You need both working together - great security without compliance can still land you in legal trouble, while compliance without proper security is just paperwork that won't stop a real attack.
How much do IT security and compliance services cost?
This is probably the first question every business owner asks, and honestly, it's like asking "how much does a car cost?" The answer depends on what you need and where you're going.
Costs vary based on several key factors: your business size, industry requirements, how complex your IT setup is, which compliance standards apply to you, and the scope of services you need. A small retail shop in Traverse City will have very different needs than a healthcare practice in Detroit.
The good news is that most providers, including us, offer flexible options that work for different budgets. You might choose a comprehensive package, specific services like vulnerability assessments, or a virtual CISO model that gives you expert guidance without the full-time salary expense.
What we can tell you is that these services are typically much more affordable than hiring full-time cybersecurity staff - and you get access to a whole team of specialists instead of just one person. Plus, you can treat it as a predictable monthly expense rather than worrying about salary, benefits, and training costs.
Can my internal IT team handle security and compliance?
Your internal IT team is absolutely valuable - they know your systems, understand your business, and keep everything running day to day. But here's the reality: modern cybersecurity and compliance require specialized expertise that most internal teams simply don't have time to develop.
Think about it this way - your IT person might be great at fixing computers and managing your network, but do they have experience with penetration testing, threat hunting, or navigating complex compliance audits? Do they have time to monitor your systems 24/7 while also handling help desk tickets and system updates?
Most internal teams, especially in small to medium businesses, face three major challenges: they lack the specialized security tools needed for comprehensive protection, they don't have the deep regulatory knowledge required for complex compliance standards, and they're already stretched thin with daily operational tasks.
IT security and compliance services don't replace your internal team - they boost it. Your IT staff can focus on what they do best while security specialists handle threat detection, compliance management, and incident response. It's like having a whole cybersecurity department without the overhead, and your existing team gets to learn from industry experts along the way.
The bottom line? Your internal IT team is essential, but partnering with specialists gives you the best of both worlds - local knowledge combined with cutting-edge security expertise and round-the-clock protection.
Conclusion
The digital landscape isn’t getting any safer, and the regulatory maze isn’t getting any simpler. But here’s what we’ve learned: IT security and compliance services aren’t just about avoiding the bad stuff—they’re about building something better.
When your business has robust protection and stays ahead of compliance requirements, something remarkable happens. You stop worrying about “what if” and start focusing on “what’s next.” Your customers trust you more. Your team innovates freely. Your competitors wonder how you make it look so easy.
The shift from reactive scrambling to proactive confidence doesn’t happen overnight, but it doesn’t have to take years either. With the right partner, you can transform security and compliance from business headaches into genuine competitive advantages.
At Kraft Business Systems, we’ve seen this change countless times across Michigan—from small businesses in Grand Rapids to growing companies in Detroit. Our diverse team of consultants and industry experts understands that every business faces unique challenges, and we’re dedicated to delivering innovative and secure technology solutions that actually make sense for your specific situation.
The question isn’t whether you need better security and compliance—it’s whether you’re ready to turn them into strengths that drive your business forward.
Ready to turn security and compliance into a business advantage? Contact Kraft Business Systems today.
Author:
Kraft Business Systems Security & Compliance Team
Trusted IT partner for Michigan businesses