Why Modern Businesses Can’t Afford to Ignore Cybersecurity
IT security solutions for businesses are more critical than ever. Cyber threats have evolved from simple viruses to sophisticated attacks that can cripple operations. The digital workplace, while transformative, has opened new doors for cybercriminals.
Essential IT Security Solutions for Businesses:
- Endpoint Protection: Antivirus, EDR, and device management
- Network Security: Firewalls, VPNs, and intrusion detection
- Data Protection: Encryption, backups, and access controls
- Email Security: Anti-phishing and gateway protection
- Identity Management: Multi-factor authentication and user controls
- Employee Training: Security awareness and phishing simulation
- Monitoring Services: 24/7 threat detection and response
The numbers are sobering. Research shows that 64% of cyberattacks target small businesses, with the average breach costing around $200,000. Ransomware demands for SMBs are also climbing.
What’s more, 82% of all breaches now involve data in cloud environments, and 63% of organizations lack AI governance policies to protect against new AI-driven threats. Relying solely on antivirus software is no longer enough.
As one cybersecurity expert noted: “Your IT people cannot protect your corporate information, even if they do their jobs perfectly. To really protect it, you have to add company-wide security policies and physical security precautions.”
The shift to digital dangers requires a new mindset. Businesses need layered security to protect against everything from phishing to zero-day malware.
Simple guide to IT security solutions for businesses:
Building Your Fortress: Essential Components of a Security Strategy
Think of IT security solutions for businesses like a medieval castle – you need multiple layers of defense. If one mechanism fails, another is ready to catch the threat. This layered approach shifts security from a reactive posture to a proactive, offensive strategy. The goal is to balance robust security with usability, so your team can remain productive.
The foundation of any security strategy is a Business Impact Analysis (BIA) and a thorough risk assessment. These steps help you understand what assets are most critical to protect, whether you’re a home office or a large enterprise handling sensitive customer data.
Data Recovery and Incident Response Planning
It’s not a matter of if a data incident will occur, but when. Whether it’s a natural disaster, a cyberattack, or human error, your business must be prepared.
Threats are diverse and persistent. Power regulating systems like UPS units are essential for graceful shutdowns during outages. A data transport plan provides a secure way to physically move critical information if networks are down.
Most importantly, a documented incident response plan is crucial. When a breach occurs, your team must know exactly who to call, what systems to isolate, and how to contain the damage. Improvisation is not an option.
More info about IT solutions can help you understand how these pieces fit together.
The Core Pillars: People, Processes, and Technology
Effective IT security solutions for businesses rest on three pillars: People, Processes, and Technology.
- People: Your employees are a primary target for cybercriminals. Security awareness training is critical to turn your team into a line of defense, teaching them to spot phishing emails and other threats.
- Processes: These are your security policies, compliance procedures, and incident response protocols. Clear processes for data access, customer information handling, and employee offboarding reduce risk.
- Technology: This includes your firewalls, encryption, and monitoring tools. However, technology is only effective when supported by trained people and solid processes.
This holistic approach ensures all three pillars work together seamlessly.
Key Considerations for Your Business’s IT Security Solutions
Evaluating IT security solutions for businesses is not a one-size-fits-all process.
- Scalability: Your security must grow with your business without requiring costly overhauls.
- Integration: New tools should work seamlessly with your existing on-premise, cloud, or hybrid infrastructure.
- Vendor Support: When issues arise, you need responsive, knowledgeable help. Downtime is devastating for business.
- Ease of Use: Complex tools often lead to misconfigurations and vulnerabilities. The best solutions balance power with user-friendly management.
- Total Cost of Ownership (TCO): Look beyond the initial price. Factor in maintenance, support, and training costs to understand the true long-term investment.
A Roundup of Essential IT Security Solutions for Businesses
Think of IT security solutions for businesses as a digital toolkit. Each tool has a specific purpose, and together they create a fortress protecting your business, whether you’re in Bellaire MI or Detroit MI.
Endpoint and Device Security
Every laptop, smartphone, and server is a potential entry point for attackers. Endpoint protection has evolved far beyond basic antivirus.
- Endpoint Detection and Response (EDR): Continuously monitors devices for suspicious behavior, providing detailed forensic information during an attack.
- Next-Generation Antivirus: Uses machine learning and AI to detect new, never-before-seen threats, boasting protection rates as high as 99.9%.
- Mobile Device Management (MDM): Enforces security policies on all mobile devices, allowing for data encryption and remote wiping if a device is lost or stolen.
- Full Disk Encryption: Makes data on a physical device unreadable to unauthorized users, even if the device is stolen.
- Vulnerability and Patch Management: Continuously identifies and fixes software weaknesses before hackers can exploit them.
A modern approach is application allowlisting with solutions like ThreatLocker. This Zero Trust Endpoint Security model only permits approved programs to run and uses application ringfencing to prevent software from performing unauthorized actions. Explore our products.
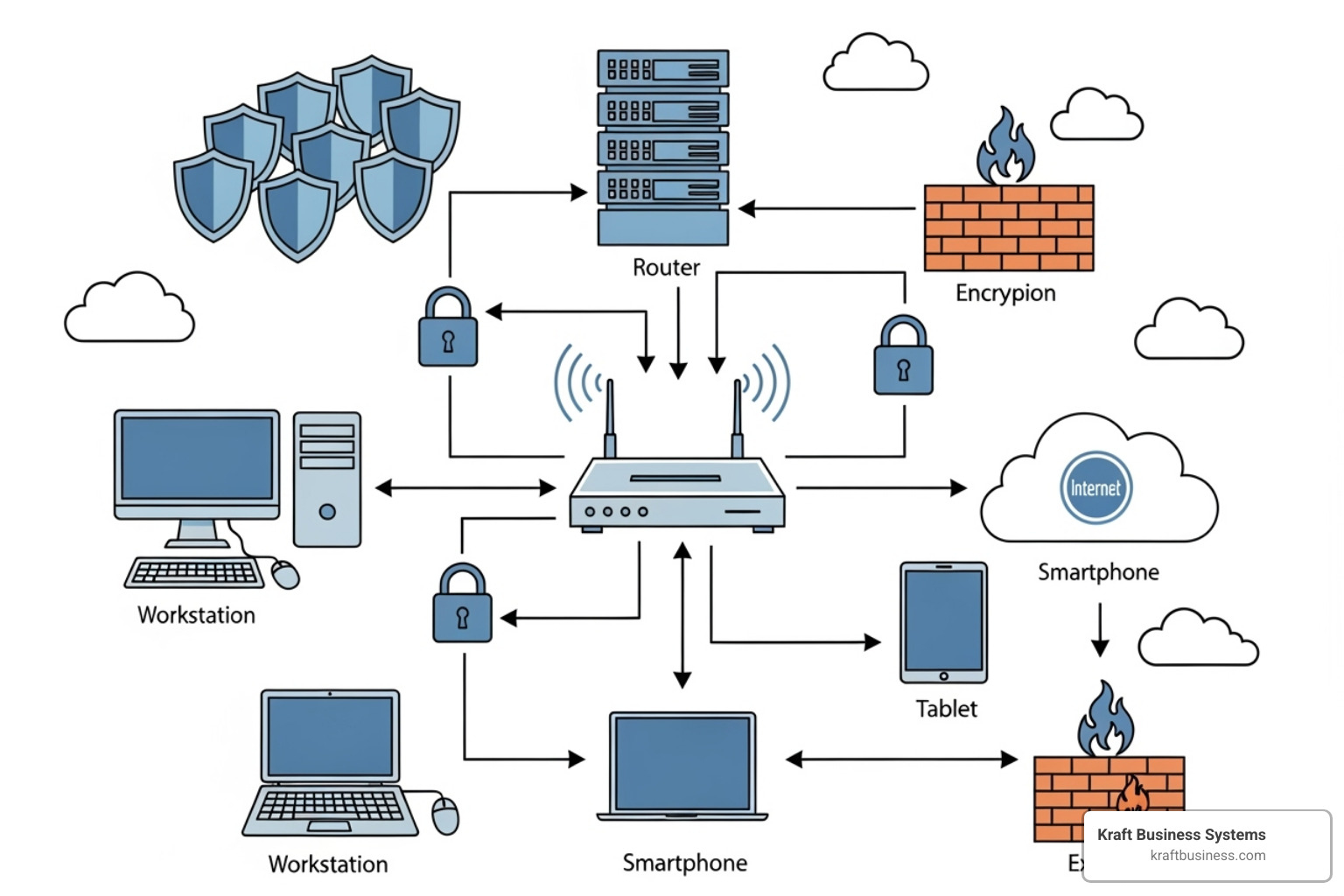
Network and Perimeter Security
Your network is the highway for your data; protecting it is vital.
- Next-Generation Firewalls (NGFW): Inspect data traffic using machine learning to identify and block sophisticated threats, including zero-day attacks.
- Intrusion Detection and Prevention Systems (IDS/IPS): Monitor network traffic for suspicious activity and can automatically block threats before they cause damage.
- VPN and Remote Access Security: Creates secure, encrypted tunnels for data, protecting remote workers and connections between multiple office locations.
- DNS Protection: Prevents users from accessing malicious websites by blocking known phishing sites and dangerous domains.
- Web Application Firewalls (WAF): Provide specialized protection for web-based applications against attacks like SQL injection and cross-site scripting.
Cloud and Data Security
With 82% of breaches involving cloud data, securing your information wherever it resides is critical.
- Cloud Access Security Brokers (CASB): Act as gatekeepers, enforcing your security policies as employees access cloud applications.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving the company network without authorization, whether through email or cloud uploads.
- Email Gateway Security: Filters spam, phishing attempts, and malware from emails before they reach user inboxes, addressing the #1 attack vector.
- Secure Backups: Your insurance policy against disaster. Regular, tested backups stored in the cloud ensure you can recover from ransomware or data deletion.
- Identity and Access Management (IAM) & Multi-Factor Authentication (MFA): IAM ensures the right people have the right access. MFA adds a second verification step beyond a password, preventing 99.9% of account compromise attacks.
The Human Element: Policies, Training, and Compliance
You can have the most advanced IT security solutions for businesses, but a single click on a phishing email can undermine it all. The human element is often the weakest link, but with the right training, your team can become your strongest line of defense. Cybercriminals are adept at exploiting human nature, making employee education essential.
Creating a Security-Aware Culture Through Employee Training
Building a security-aware culture is about empowering employees with knowledge, not instilling fear.
- Phishing Simulations: We send simulated phishing attacks to provide teachable moments, helping employees recognize red flags in a safe environment. It’s like a fire drill for cybersecurity.
- Social Engineering Awareness: Training extends beyond email to phone calls and in-person interactions, teaching staff to spot manipulation attempts.
- Secure Password Practices: We teach why strong, unique passwords matter and how password managers can make security convenient.
- Data Handling Policies: Clear, practical policies ensure your team knows what information can be shared, with whom, and how.
- Insider Threat Prevention: This involves creating systems that catch mistakes and encourage employees to report suspicious activity without fear of blame.
- Ongoing Education: Cybersecurity threats evolve constantly, so training must be continuous and relevant to current attack methods.
Ensuring Regulatory and Security Compliance
Compliance frameworks like HIPAA, HITECH, GDPR, PCI-DSS, and NIST are more than legal problems; they are roadmaps for building secure organizations.
- HIPAA/HITECH: Essential for healthcare providers to protect patient data and maintain trust.
- PCI-DSS: Required for any business handling credit card information to protect customer financial data and brand reputation.
- GDPR: Affects any business handling data from EU citizens, focusing on giving individuals control over their personal information.
- NIST Framework: A comprehensive guide for businesses of all sizes to manage cybersecurity risk across the organization.
- Security Audits: Regular audits are like health checkups for your security, identifying gaps before they become breaches and demonstrating your commitment to security.
We help businesses steer these complex requirements, breaking them down into manageable steps. HIPAA and HITECH Compliance Whitepaper.
Advanced Strategies: Zero Trust and Managed Security Services
Once the fundamentals are in place, advanced IT security solutions for businesses can lift your protection. These strategies are designed to proactively prevent threats from gaining a foothold, moving beyond reactive defense to stay ahead of sophisticated attackers.
Adopting a Zero Trust Security Model
The Zero Trust security model operates on a simple principle: “never trust, always verify.” It assumes no user or device is inherently trustworthy, whether inside or outside your network. Every access request is scrutinized every time.
- Micro-segmentation: This divides your network into small, isolated segments. If a breach occurs in one area, it is contained and cannot easily spread across the entire system.
- Principle of Least Privilege: Users and applications are granted only the minimum access required to perform their functions. This limits the potential damage a compromised account can cause.
- Identity-Centric Security: Verification focuses on who is accessing resources, not where they are. The same strict authentication applies whether a user is in the office or working remotely.
- Continuous Validation: Unlike traditional models that verify once, Zero Trust continuously validates credentials and context throughout a session, ensuring ongoing security.
Leveraging Managed Security Service Providers (MSSPs)
Building an effective in-house cybersecurity team is expensive and complex. A CISO’s salary alone can exceed $200,000, not including the cost of analysts, engineers, and tools.
Managed Security Service Providers (MSSPs) like Kraft Business Systems offer a practical alternative. We provide the expertise, tools, and processes so you don’t have to build them from scratch.
- 24/7 Monitoring: Our Security Operations Center (SOC) watches your systems around the clock, as threats don’t adhere to business hours. We detect and respond to suspicious activity immediately.
- Access to Specialized Expertise: You gain access to a team of specialists who stay current on the latest threat intelligence and security technologies.
- Virtual CISO (vCISO): For strategic leadership, our vCISO services provide executive-level guidance on policy, risk assessment, and incident response planning.
- Cost-Effectiveness for SMBs: An MSSP gives you access to an entire team of experts and enterprise-grade tools for a fraction of the cost of hiring internally.
Learn about managed IT support.
Frequently Asked Questions about Business IT Security
Business owners across Michigan often ask the same questions when trying to balance security, cost, and complexity. Here are answers to some of the most common concerns.
Why is IT security so important for a small business?
Cybercriminals see small businesses as easy targets, with 64% of all cyberattacks aimed at them. Many owners mistakenly believe they are too small to be noticed. The financial impact of a breach is severe, averaging $200,000 in direct costs, not including reputational damage. Critically, 60% of customers don’t return after a breach, which can be a fatal blow to a small company. IT security solutions for businesses are not just about protecting data; they are about protecting your livelihood.
What is the single most effective security measure a business can implement?
While a layered defense is best, the single most effective measure is Multi-Factor Authentication (MFA). MFA can prevent up to 99.9% of account compromise attacks. Even if a criminal steals a password, they cannot access the account without the second verification factor (like a code from a phone app). It is a low-cost, high-impact solution that most business applications already support.
How do I start building a cybersecurity plan if I have a limited budget?
You don’t need a massive budget to improve your security. Start with a risk assessment to identify your most critical data and vulnerabilities. Then, focus on high-impact, low-cost actions:
- Implement MFA on all accounts.
- Conduct basic employee training on recognizing phishing emails.
- Ensure you have regular, tested data backups.
Prioritize protecting your most valuable assets first. Building effective IT security solutions for businesses is a marathon, not a sprint. Start with the basics and add more layers as your business grows.
Conclusion: Securing Your Business for Tomorrow
The cybersecurity landscape is constantly accelerating. The key takeaway is that security isn’t a one-time purchase but an ongoing partnership between your people, processes, and technology.
Threats evolve daily. The rise of AI-driven attacks and sophisticated phishing campaigns means your security strategy must be dynamic. This is where “future-proofing” becomes critical. Future-proofing isn’t about predicting every threat; it’s about building a resilient foundation that can adapt to new challenges. Implementing MFA, training employees, maintaining secure backups, and partnering with experts for 24/7 monitoring prepares you for tomorrow’s unknowns.
Choosing the right security partner makes all the difference. At Kraft Business Systems, we understand that security must be effective without hindering productivity. We find the sweet spot where robust protection meets practical usability.
A data breach costs more than money; it costs the trust you’ve built with customers and your peace of mind. You don’t have to steer this complex landscape alone. Whether you’re just starting or looking to mature your security posture, the right partner can guide you.
Your business deserves protection that grows with you. By taking proactive steps today, you ensure your business can thrive in any digital future.
Ready to take the next step? Explore our managed cybersecurity services to get started and learn how we can help secure your business.