Cloud security management solutions help organizations protect their data, applications, and infrastructure across cloud environments through continuous monitoring, threat detection, and automated remediation. These comprehensive platforms address the growing complexity of cloud security by providing unified visibility and control over multi-cloud deployments.
Key cloud security management capabilities include:
- Continuous monitoring – Real-time visibility into cloud assets and configurations
- Threat detection – Automated identification of security risks and vulnerabilities
- Compliance management – Ensuring adherence to regulatory standards like HIPAA and GDPR
- Identity and access control – Managing user permissions and preventing unauthorized access
- Automated remediation – Fixing security issues without manual intervention
- Incident response – Coordinated response to security events and breaches
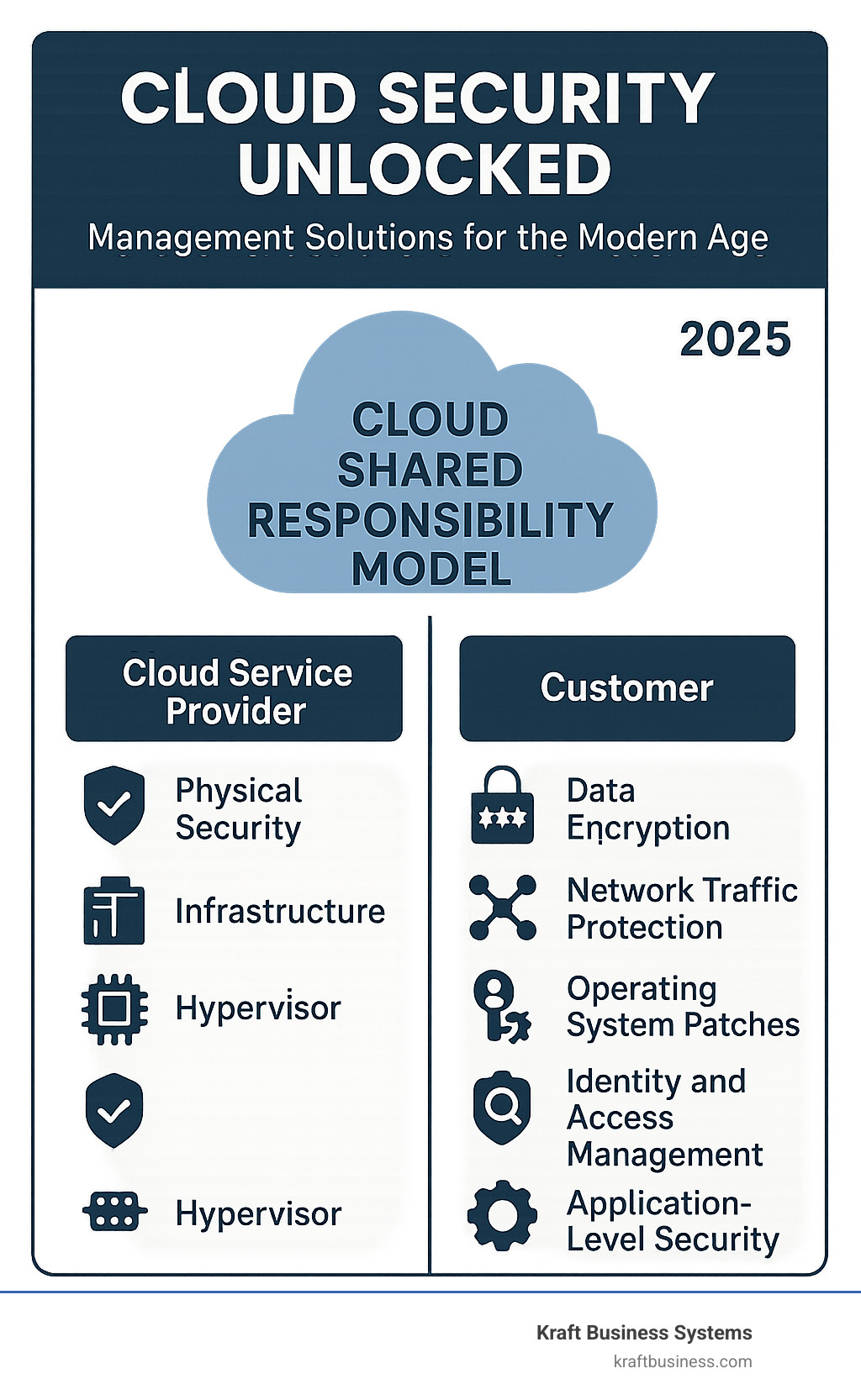
The shared responsibility model makes cloud security more complex than traditional IT security. While cloud providers secure the infrastructure, you’re responsible for protecting your data, applications, and user access. This division creates gaps that attackers exploit through misconfigurations, excessive permissions, and unpatched vulnerabilities.
Organizations that implement proactive risk identification strategies, including cloud security management solutions, experience 60% fewer security breaches compared to those that don’t. This dramatic reduction stems from continuous monitoring and automated threat detection capabilities that catch issues before they become major incidents.
“Remediating cloud risks is a huge challenge for security teams, especially in a world where DevOps is the norm,” notes industry research. The speed of cloud deployment often outpaces security reviews, creating dangerous configuration gaps.
Modern cloud environments span multiple providers and services, making manual security management impossible. Without unified visibility, security teams lack the context needed to prioritize risks effectively. This leads to alert fatigue and missed threats that could have been prevented.
Cloud security management solutions terms explained:
Understanding the Need for Cloud Security Management Solutions
The shift to cloud computing offers incredible agility and scalability, but it also introduces new security challenges. Our reliance on cloud environments means that securing them is no longer optional; it’s a fundamental requirement for business continuity and trust. We’ve seen how vulnerabilities, misconfigurations, identity risks, and compliance violations can lead to severe consequences.
One of the most pressing concerns is data breaches. Cloud environments, by their very nature, are distributed and connected to the internet, creating a larger attack surface than traditional data centers. This increased exposure means a greater potential for cybersecurity risk. Misconfigurations, for example, are a leading cause of data breaches, often leaving sensitive data exposed unintentionally. Without proper cloud security management solutions, organizations risk unauthorized access to critical information, leading to financial losses, reputational damage, and legal repercussions.
Beyond data breaches, compliance violations pose a significant threat. Many industries are subject to stringent regulatory standards like HIPAA (for healthcare), GDPR (for data privacy in Europe), and PCI DSS (for payment card information). Cloud environments must adhere to these regulations, and non-compliance can result in hefty fines and legal action. Ensuring continuous compliance across a dynamic cloud infrastructure requires constant vigilance, which is nearly impossible to achieve manually.
Operational downtime is another critical impact of inadequate cloud security. Ransomware attacks, DDoS attacks, or even simple misconfigurations can render cloud services unavailable, halting business operations. This downtime translates directly to lost revenue, decreased productivity, and frustrated customers.
At Kraft Business Systems, we understand these challenges intimately. Our goal is to help you steer the complexities of cloud security, ensuring your cloud assets are protected and your operations remain uninterrupted. We believe that robust cloud security management solutions are essential for any business leveraging the cloud. For a deeper dive into protecting your cloud assets, explore our insights on Cloud Security for Businesses.
What is Cloud Security Posture Management (CSPM)?
Navigating the complexities of cloud security requires a proactive and strategic approach, and Cloud Security Posture Management (CSPM) solutions are essential in this journey. So, what exactly is CSPM, and why is it so crucial for cloud environments?
A Cloud Security Posture Management (CSPM) solution is designed to provide organizations with a comprehensive view of their cloud security status. It achieves this by continuously scanning cloud infrastructures for misconfigurations, compliance risks, and security vulnerabilities. Think of it as an ever-watchful guardian that ensures your cloud environment aligns with security best practices and regulatory requirements.
The core of CSPM lies in its ability to offer:
- Continuous Monitoring: CSPM tools provide real-time visibility into your cloud assets and configurations. They maintain an up-to-date inventory of all cloud resources—whether in Infrastructure as a Service (IaaS), Platform as a Service (PaaS), or Software as a Service (SaaS) environments—for proactive analysis and risk assessment. This continuous assessment helps detect configuration drifts from desired states.
- Automated Finding and Prioritization: These solutions automatically identify security issues like overly permissive access controls, unencrypted storage buckets, or publicly exposed network ports. They often leverage machine learning to prioritize these findings based on severity and potential impact, allowing security teams to focus on the most critical risks first.
- Misconfiguration Remediation Guidance: Once misconfigurations are detected, CSPM tools not only alert you but also provide actionable guidance or even automated remediation options to fix the issues. This helps ensure that security controls are developed and implemented effectively.
- Compliance Auditing: CSPM solutions are instrumental in ensuring continuous compliance with regulatory requirements and security frameworks. They map your cloud configurations against standards like GDPR, HIPAA, PCI DSS, and CIS Benchmarks, providing automated reports and alerts on non-compliance. This feature is invaluable for maintaining a strong security posture and passing audits.
The cruciality of CSPM stems from the dynamic nature of cloud environments. Resources are spun up and down rapidly, often by multiple teams, making manual auditing impractical. Without CSPM, it’s easy for misconfigurations to slip through, creating security gaps that attackers can exploit. By automating the detection and remediation of these flaws, CSPM significantly strengthens cloud infrastructure resilience and helps mitigate risks before they escalate. It shifts security left, enabling us to address issues earlier in the cloud lifecycle. For more detailed insights into CSPM, refer to our dedicated resource on Cloud Security Posture Management.
Why Cloud Security Management Solutions Are Essential
Understanding and Assessing Your Cloud Security Posture
Think of your cloud security posture like the foundation of your house. You wouldn’t build on shaky ground, and you shouldn’t run your business on an insecure cloud foundation. The challenge is that unlike a physical foundation, your cloud environment changes constantly—new resources appear, configurations shift, and access permissions evolve daily.
Effective cloud security management solutions start with understanding exactly what you’re protecting. This means creating a complete picture of your cloud landscape, identifying where vulnerabilities might be hiding, and understanding the risks that could impact your business.
Asset inventory forms the cornerstone of this assessment. Your CSPM solution maintains a real-time catalog of everything in your cloud environment—virtual machines, storage buckets, databases, serverless functions, and network configurations across AWS, Azure, Google Cloud, and any other providers you use. It’s like having a security guard who knows every door, window, and entry point in your building.
But knowing what you have is just the beginning. Vulnerability scanning goes deeper, continuously examining these assets for security weaknesses. This includes checking operating systems for unpatched flaws, scanning applications for known vulnerabilities, and inspecting container images for security gaps that attackers could exploit.
Perhaps most critically, Identity and Access Management (IAM) analysis examines who has access to what in your cloud environment. This is where many organizations face their biggest risks. Cloud environments often accumulate permissions over time—employees get access for specific projects, service accounts are created for automation, and roles expand beyond their original scope. Without proper oversight, you might have former employees with active accounts or applications with excessive privileges they don’t actually need.
Modern CSPM tools excel at identifying and helping remediate risks across all types of cloud services—Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS). They work continuously in the background, maintaining that current inventory while proactively analyzing configurations and assessing risks. This automation allows your team to focus on fixing problems rather than hunting for them. For a comprehensive look at how we approach these assessments, explore our IT Security Risk Assessment services.
Continuous Visibility and Monitoring
Your cloud environment never sleeps, and neither should your security monitoring. Cloud resources spin up and down at lightning speed—what was secure this morning might have a dangerous misconfiguration by afternoon. Manual security checks simply can’t keep pace with this rapid change.
Cloud security management solutions provide the always-on vigilance your environment needs. Real-time alerts act like smoke detectors for your cloud infrastructure. When someone accidentally makes a storage bucket public, when a security group opens dangerous ports to the internet, or when suspicious login activity occurs, you get immediate notifications. This speed matters—the difference between catching a misconfiguration in minutes versus days can mean the difference between a close call and a data breach.
Configuration drift detection solves a common headache for IT teams. You establish secure configurations, but over time, things change. Developers deploy updates, administrators make quick fixes, and automated systems modify settings. Before you know it, your carefully crafted security policies have drifted away from their intended state. Continuous monitoring catches these deviations automatically, ensuring your environment stays aligned with your security standards.
Threat intelligence feeds add another layer of protection by connecting your monitoring to the broader cybersecurity community. When researchers find new attack techniques or identify malicious IP addresses, this intelligence flows into your monitoring system. Your security posture stays current with emerging threats rather than always playing catch-up.
Log analysis brings everything together by centralizing activity logs from across your cloud services. Instead of manually checking dozens of different log sources, your security team gets a unified view of what’s happening. This comprehensive visibility makes it much faster to spot anomalies, investigate incidents, and understand the full scope of any security events.
The beauty of continuous monitoring lies in its ability to turn reactive security into proactive protection. Rather than finding problems during quarterly audits or after incidents occur, you’re identifying and addressing issues as they happen. Learn more about our approach to ongoing protection through our Cloud Security Monitoring Solutions.
Ensuring Compliance and Governance
Compliance isn’t just about avoiding fines—it’s about building trust with your customers and partners. When you can demonstrate that your cloud environment meets rigorous security standards, you’re showing the world that you take data protection seriously.
Regulatory standards like HIPAA, GDPR, and PCI DSS each bring specific requirements for how you handle sensitive data. HIPAA demands encryption of healthcare information, GDPR requires strict controls over personal data, and PCI DSS mandates secure handling of payment card information. Cloud security management solutions understand these requirements and continuously verify that your configurations meet them.
Automated compliance checks transform the traditional audit process from a stressful, time-consuming ordeal into an ongoing, manageable process. Instead of scrambling to gather evidence and fix issues when auditors arrive, your CSPM solution runs hundreds or thousands of policy checks continuously. It verifies that sensitive data is encrypted, access controls are properly configured, and logging is enabled where required.
This automation doesn’t just save time—it improves accuracy. Manual compliance checks are prone to human error and can miss subtle configuration issues. Automated systems catch these details consistently, providing more reliable compliance assurance.
Policy enforcement takes compliance a step further by automatically correcting violations when they occur. If someone accidentally disables encryption on a database that contains sensitive information, the system can re-enable it automatically or immediately alert administrators to fix the issue. This prevents compliance violations from persisting and reduces the window of risk.
The integration of security and compliance early in your cloud journey prevents costly surprises down the road. It’s much easier to build compliance into your cloud architecture from the beginning than to retrofit it later. Our team specializes in helping organizations steer these complex requirements through comprehensive Governance Risk Assessment and Cybersecurity GRC services.
Core Capabilities of Cloud Security Management Solutions
Think of cloud security management solutions as your comprehensive security command center. These aren’t just individual tools working in isolation—they’re integrated platforms that work together seamlessly to protect your entire cloud environment from threats, misconfigurations, and compliance violations.
Modern cloud security platforms bring together multiple specialized capabilities under one roof. Cloud Security Posture Management (CSPM) handles continuous monitoring and compliance checks, while Cloud Workload Protection Platforms (CWPP) focus on securing your actual workloads—whether they’re virtual machines, containers, or serverless functions—throughout their entire lifecycle.
Cloud Access Security Brokers (CASB) step in to enforce security policies for your cloud applications, particularly those Software-as-a-Service tools your team uses daily. Meanwhile, Cloud Detection and Response (CDR) capabilities actively hunt for threats that might already be lurking in your environment.
Two newer but equally important capabilities are Cloud Infrastructure Entitlement Management (CIEM), which keeps tabs on who has access to what (and whether they really need it), and Data Security Posture Management (DSPM), which finds and protects your sensitive data wherever it lives in the cloud.
API Security rounds out the core capabilities, protecting the application programming interfaces that power modern cloud-native applications. Since APIs are often the front door to your applications and data, securing them is absolutely critical.
Many vendors now package these capabilities into what’s called a Cloud-Native Application Protection Platform (CNAPP). This unified approach eliminates the headache of managing multiple disconnected security tools while giving you better visibility and control over your entire cloud security posture.
Our team at Kraft Business Systems understands that managing all these moving parts can feel overwhelming. That’s why we focus on implementing Cybersecurity Technology Solutions that work together harmoniously, giving you robust protection without the complexity.
Proactive Threat and Vulnerability Management
Nobody wants to be the organization that finds a security breach through a phone call from a reporter. That’s why proactive threat and vulnerability management sits at the heart of effective cloud security management solutions. We’re talking about finding and fixing problems before the bad guys even know they exist.
Vulnerability scanning forms the foundation of this proactive approach. Modern solutions continuously scan every corner of your cloud infrastructure—virtual machines, container images, serverless functions, and more. The best part? Many use agentless technology that can scan your entire environment quickly without slowing things down, backed up by lightweight agents that provide detailed, real-time insights.
But here’s where it gets smart: not every vulnerability deserves a red alert at 3 AM. Remediation prioritization uses contextual risk assessment to rank vulnerabilities based on what actually matters—how easily they can be exploited, what sensitive data they might expose, and how accessible they are from the internet. This means your security team can focus their energy where it will make the biggest difference.
Managed threat detection and response takes things a step further by actively monitoring for suspicious behavior and potential intrusions. Think of it as having a security guard who never sleeps, equipped with host-based intrusion detection capabilities that provide deep visibility into what’s happening inside your workloads.
The beauty of this approach lies in its continuous improvement cycle. By constantly detecting, prioritizing, and fixing security issues, your cloud environment becomes more resilient over time. It’s like building up your immune system—each threat you successfully defend against makes you stronger for the next one.
We’ve seen how this proactive approach transforms our clients’ security posture. If you’re curious about the specific benefits, check out our insights on 5 Ways Businesses Benefit from Managed Threat Detection and Response.
Identity, Access, and Data Security
Here’s a truth that might surprise you: your network perimeter isn’t your castle wall anymore. Your identities are. Every user, application, and service in your cloud environment has an identity, and each identity comes with permissions. Managing these permissions effectively can make or break your security posture.
The least privilege principle sounds fancy, but it’s really just common sense: people and systems should only have access to what they absolutely need to do their jobs. IAM analysis within cloud security solutions continuously examines your identity configurations, hunting for excessive permissions, unused access rights, and potential paths that attackers could use to escalate their privileges.
This analysis goes beyond just checking who has access to what. It monitors all the actions carried out by various users and systems, helping you spot when someone’s doing something they probably shouldn’t be doing. It’s like having a very polite but vigilant security guard who notices when the intern from accounting is trying to access the CEO’s files.
Data encryption protects your information both when it’s sitting in storage and when it’s traveling across networks. Modern cloud security management solutions ensure that sensitive data in your cloud storage buckets, databases, and other services uses strong cryptographic methods that would take a supercomputer centuries to crack.
Data Loss Prevention (DLP) capabilities add another layer by finding and classifying your sensitive data, then monitoring and blocking any unauthorized attempts to share or transfer it. Think of it as a smart bouncer who knows exactly which information is too sensitive to leave the building.
The reality is that managing identities, access, and data in the cloud requires constant vigilance and sophisticated tools. Our team specializes in implementing comprehensive Cloud Data Protection Solutions that keep your most valuable assets safe without getting in the way of productivity.
Automated Remediation and Incident Response
Cloud environments move fast—really fast. Resources get spun up and torn down in minutes, configurations change constantly, and threats can emerge and spread before a human security analyst even knows they exist. That’s why automation isn’t just helpful in cloud security; it’s absolutely essential.
Automated workflows handle many security issues without human intervention. When the system detects a misconfigured storage bucket that’s accidentally public, it can automatically fix the permissions or trigger a predefined workflow to address the issue. This isn’t just about speed—it’s about consistency. Automated responses don’t have bad days or forget steps.
Policy-as-code takes this automation even further by embedding security checks directly into your development pipelines. If a developer tries to deploy a vulnerable container image or a misconfigured infrastructure template, the system can stop the deployment automatically. This “shift-left” approach catches problems before they ever reach production.
When a real security incident occurs, incident containment capabilities can automatically isolate compromised workloads, block malicious IP addresses, or revoke suspicious credentials faster than any human could react. Minutes matter during a security incident, and automation can buy you precious time while your security team mobilizes.
Modern cloud security management solutions integrate seamlessly with the tools your development and operations teams already use—GitHub, JIRA, Slack, and others. Security findings and remediation tasks get automatically routed to the right people, creating a smooth collaboration flow that accelerates resolution without creating chaos.
We’ve found that organizations using automated remediation can detect, prioritize, and fix security issues dramatically faster than those relying on manual processes. Our expertise in Security Incident Management and comprehensive Cyber Incident Response Services helps ensure your business stays protected even when things go sideways.
Best Practices for Implementation and Management
Successfully implementing cloud security management solutions is like building a house—you need a solid foundation, the right materials, and a clear plan. We’ve seen too many organizations rush into deployment only to find themselves overwhelmed by alerts they don’t understand or tools that don’t fit their workflow.
The secret to success lies in taking a measured approach. A phased rollout is your best friend here. Think of it as testing the waters before diving in. Start with a non-critical environment where you can experiment, make mistakes, and learn without impacting your core business operations. This gives your team time to understand how the solution works and how it fits into your existing processes.
Stakeholder training is absolutely crucial, and we can’t stress this enough. Security isn’t just the IT team’s job anymore—it’s everyone’s responsibility. Your developers need to understand how security findings relate to their code. Your operations team needs to know how to respond to alerts. Even your leadership needs to grasp what the dashboards are telling them about your organization’s risk posture.
Performance tuning comes next, and this is where patience pays off. Your cloud security management solutions should improve your security without grinding your operations to a halt. Fine-tune your policies to reduce false positives, adjust alert thresholds to match your environment, and optimize scanning schedules to minimize performance impact.
We’ve helped countless organizations steer this journey through our comprehensive Managed IT Services Cybersecurity Solutions, and we know that taking the time to do it right upfront saves countless headaches down the road.
Integrate Security into the Development Lifecycle (DevSecOps)
Here’s where things get really exciting. Integrating security into your development lifecycle—what we call DevSecOps—transforms security from a roadblock into a competitive advantage. Instead of finding vulnerabilities right before launch (or worse, after a breach), you catch them while the code is still warm from the developer’s keyboard.
Shift-left security is the heart of this approach. Picture your development process as a timeline moving from left to right. The further left you can push security checks, the cheaper and easier they are to fix. A vulnerability caught during development might take minutes to resolve. The same vulnerability finded in production could take days and cost thousands.
CI/CD pipeline integration makes this magic happen automatically. Every time a developer commits code or builds a new container image, your cloud security management solutions spring into action. They scan for vulnerabilities, check configurations, and verify compliance requirements. If something’s not right, the pipeline stops, and the developer gets immediate feedback.
Infrastructure-as-Code (IaC) scanning takes this concept even further. Before your infrastructure even exists in the cloud, the security tools are already reviewing your Terraform templates or CloudFormation scripts for potential misconfigurations. It’s like having a security expert review your blueprints before you start building.
This approach creates what we love to see—a strong Culture of Cybersecurity Awareness where security becomes second nature rather than an afterthought.
Automate and Prioritize
Let’s be honest—cloud environments generate more security alerts than any human team can reasonably handle. Without smart automation and prioritization, you’ll either burn out your security team or miss critical threats while chasing false alarms.
Risk-based prioritization is your lifeline here. Not every alert deserves the same level of attention. A misconfigured development server might be worth noting, but a publicly exposed database containing customer information demands immediate action. Effective cloud security management solutions understand this context and help you focus your energy where it matters most.
Automated policy enforcement handles the routine stuff so your team can focus on the complex challenges. When the system detects a storage bucket that’s accidentally been made public, it can automatically fix the permissions and notify the relevant team. When a virtual machine is missing critical security patches, it can schedule the updates during the next maintenance window.
Reducing alert fatigue is perhaps the most important benefit of smart automation. We’ve seen security teams become so overwhelmed by low-priority alerts that they start ignoring all notifications—including the critical ones. By automatically handling routine issues and intelligently prioritizing genuine threats, your team stays sharp and responsive.
This approach aligns perfectly with our commitment to implementing robust Network Security Best Practices that work smarter, not harder.
Regularly Review and Refine
Security isn’t a destination—it’s a journey. Your cloud security management solutions need regular care and feeding to stay effective as your environment evolves and new threats emerge.
Security audits should become a regular part of your routine, not something you do only when compliance requires it. Use the data from your security tools to conduct thorough reviews of your cloud environment. Look for patterns in the types of issues you’re seeing. Are developers consistently making the same configuration mistakes? Are certain teams struggling with access management? These insights help you improve your processes, not just fix individual problems.
User access reviews deserve special attention because permissions have a way of accumulating over time. Someone gets temporary access to a project and never gets removed. A contractor’s account stays active long after their engagement ends. Regular access reviews, supported by automated tools that flag dormant accounts and excessive permissions, keep your access controls tight and current.
Updating security policies is essential as your business grows and changes. New cloud services, evolving regulations, and emerging threats all require policy adjustments. Your cloud security management solutions should make it easy to update and test these policies without disrupting operations.
Incorporating feedback from your teams is perhaps the most valuable part of this process. The people using these tools daily have insights that dashboards can’t capture. Maybe the alert notifications are too frequent, or perhaps certain types of findings need better context. Regular feedback sessions help you tune your security program to work better for everyone involved.
The human element remains crucial throughout this process. We offer comprehensive Cybersecurity Training for Employees because even the best technology is only as effective as the people using it.
Choosing and Integrating the Right Tools
Selecting the right cloud security management solutions can feel overwhelming at first. With so many vendors and options available, it’s easy to get lost in the technical jargon and marketing promises. The key is to approach this decision strategically, focusing on what truly matters for your organization’s unique needs.
Think of it like building a custom security system for your home. You wouldn’t just buy random components and hope they work together. Instead, you’d consider factors like scalability – will this system grow with your needs? If you’re planning to expand your cloud footprint, your security solution needs to handle that growth without breaking a sweat.
Multi-cloud support is another crucial consideration. Many organizations use multiple cloud providers to avoid vendor lock-in or leverage specific services. Your security solution should provide a unified view across AWS, Azure, Google Cloud, and any other platforms you use. Nobody wants to juggle multiple dashboards just to understand their security posture.
Don’t overlook vendor reputation either. Look for companies with a solid track record, responsive customer support, and a commitment to innovation. The best solutions consistently improve and deliver focused insights with meaningful context, not just endless alerts that create more work for your team.
At Kraft Business Systems, we understand that choosing security tools isn’t just about features – it’s about finding solutions that fit seamlessly into your existing operations. Our expertise in Hybrid Cloud Security Solutions helps businesses create cohesive security strategies that actually work in the real world.
Key Factors in Choosing Cloud Security Management Solutions
When you’re evaluating cloud security management solutions, it helps to think beyond the flashy demo presentations and focus on the fundamentals that will make or break your security program.
Compatibility and integration should be at the top of your list. Your new security solution needs to play nicely with your existing tools – your development pipelines, incident response platforms, and other security systems. Solutions that create new data silos or require months of custom development work will only add to your headaches. Look for platforms that can pull information from various sources and present it in a unified way.
Comprehensive security features matter because piecemeal solutions often leave gaps. The best platforms combine Cloud Security Posture Management (CSPM) with Cloud Workload Protection (CWPP), Identity and Access Management analysis, and Data Security Posture Management. When these capabilities work together, you get better context for decision-making and fewer blind spots in your security coverage.
Automation and AI capabilities aren’t just buzzwords – they’re essential for managing modern cloud environments. Manual security processes simply can’t keep up with the pace of cloud deployment. Look for solutions that offer automated policy enforcement, intelligent risk prioritization, and remediation workflows that actually reduce your team’s workload rather than adding to it.
Total cost of ownership goes far beyond the license fees. Consider deployment time, training requirements, ongoing maintenance, and the hidden costs of managing multiple tools. Solutions that offer quick onboarding and immediate value can often justify higher upfront costs through improved efficiency and reduced breach risk.
Regulatory compliance support becomes critical if you operate in regulated industries. Make sure your chosen solution provides robust support for HIPAA, GDPR, PCI DSS, or whatever frameworks apply to your business. Automated compliance checks and reporting capabilities can save countless hours during audit season.
Vendor reputation and support services can make the difference between a successful implementation and a frustrating experience. Strong, responsive support teams become invaluable when you’re dealing with critical incidents or complex integrations.
For a deeper dive into selecting governance, risk, and compliance tools, our IT Governance, Risk, and Compliance Tools Guide provides additional insights to help guide your decision-making process.
Understanding Different Tool Types
The world of cloud security management solutions includes several distinct categories, each designed to address specific security challenges. Understanding these different tool types helps you build a more effective overall security strategy.
Cloud Security Posture Management (CSPM) tools focus on configuration management and compliance. They continuously scan your cloud environments for misconfigurations, policy violations, and security risks. Think of them as your cloud environment’s health monitor, constantly checking that everything is configured securely.
Cloud Workload Protection Platforms (CWPP) take a different approach, focusing on protecting the actual workloads – your virtual machines, containers, and serverless functions. These platforms offer vulnerability management, runtime protection, and host-based intrusion detection throughout the entire workload lifecycle.
Cloud-Native Application Protection Platforms (CNAPP) represent the next evolution in cloud security. Rather than managing separate tools for different security functions, CNAPP integrates multiple capabilities into a single platform. This unified approach covers everything from code security to runtime protection, making it particularly valuable for organizations with complex cloud-native applications and DevOps environments.
Security assessment and monitoring tools round out the landscape with capabilities like vulnerability scanning, penetration testing, security information and event management (SIEM), and data loss prevention (DLP). These tools provide the continuous monitoring and analysis capabilities needed to detect threats and investigate incidents.
The industry trend is moving toward consolidation and unification, with CNAPP platforms leading the charge. Instead of juggling multiple dashboards and trying to correlate data from different tools, organizations can leverage a CNAPP to get a single, comprehensive view of their security posture. This approach simplifies operations while improving security effectiveness.
The Future: AI and Unified Platforms
The future of cloud security management solutions is being shaped by artificial intelligence and the drive toward unified security platforms. These developments promise to make cloud security more intelligent, automated, and effective.
AI-driven threat detection is revolutionizing how we identify and respond to security threats. Machine learning algorithms can analyze massive amounts of security data, spot subtle patterns that humans might miss, and detect sophisticated threats that bypass traditional security measures. This capability is particularly valuable for identifying zero-day attacks and advanced persistent threats.
Machine learning for anomaly identification works by establishing baselines of normal behavior in your cloud environment. When something deviates from these established patterns – even slightly – the system can flag it for investigation. This approach is especially effective at catching insider threats and subtle attack techniques that might otherwise go unnoticed.
The rise of CNAPP represents more than just a trend – it’s the future direction of cloud security. By consolidating CSPM, CWPP, Cloud Infrastructure Entitlement Management (CIEM), and other critical security capabilities into a single platform, CNAPP simplifies management while improving security context. This integration makes it easier to prioritize risks and streamline security workflows from development through production.
Predictive security analytics takes things a step further by using AI and machine learning to anticipate potential vulnerabilities and attack paths before they’re exploited. Instead of just reacting to threats, organizations can proactively strengthen their defenses based on predictive insights.
These advances are changing cloud security from a reactive discipline to a proactive, intelligent practice. At Kraft Business Systems, we stay current with these developments to ensure our clients benefit from the most advanced and effective security solutions available. The goal isn’t just to keep up with threats – it’s to stay ahead of them.
Conclusion
The journey through cloud security doesn’t end with deployment—it’s an ongoing commitment that requires vigilance, adaptation, and the right partnerships. Throughout this guide, we’ve seen how cloud security management solutions transform the complex challenge of cloud protection into manageable, automated processes that actually strengthen your business operations.
The path forward becomes clearer when you understand that cloud security isn’t just about preventing bad things from happening. It’s about enabling your business to innovate confidently, knowing that your data, applications, and infrastructure are protected by intelligent systems that work around the clock.
Your success depends on embracing a proactive approach that treats security as a business enabler, not a roadblock. This means prioritizing Cloud Security Posture Management (CSPM) for that essential continuous visibility and compliance assurance, while embracing comprehensive capabilities that cover everything from threat detection to automated remediation.
Adopting DevSecOps principles shifts security left in your development process, building protection into your applications from the ground up rather than trying to add it later. Meanwhile, automating and prioritizing your security responses helps your team focus on what matters most, reducing alert fatigue and improving response times.
The commitment doesn’t stop there. Continuous improvement through regular reviews and policy updates keeps your defenses sharp against evolving threats. Choosing the right tools based on compatibility, features, and vendor support ensures your investment pays dividends for years to come. And looking to the future means preparing for AI-driven security and unified platforms that will make cloud protection even more effective.
We understand that navigating these waters can feel overwhelming. That’s exactly why Kraft Business Systems exists. Located in Grand Rapids, MI, and serving businesses across Michigan including Acme, Ann Arbor, and Traverse City, we’ve built our reputation on making complex technology challenges simple and manageable for our clients.
Our team of consultants and industry experts doesn’t just implement solutions—we partner with you to understand your unique business challenges and craft security strategies that make sense for your organization. We believe that the best cloud security management solutions are the ones that work seamlessly in the background, protecting your business while empowering your team to focus on what they do best.
The stakes are real, but so are the solutions. With the right approach and trusted partners, your cloud environment can become your competitive advantage rather than a source of worry.
Ready to take control of your cloud security? We’re here to help you build defenses that grow with your business. Strengthen your defenses with our Managed Cybersecurity Services and find how partnership with Kraft Business Systems can transform your approach to cloud security.