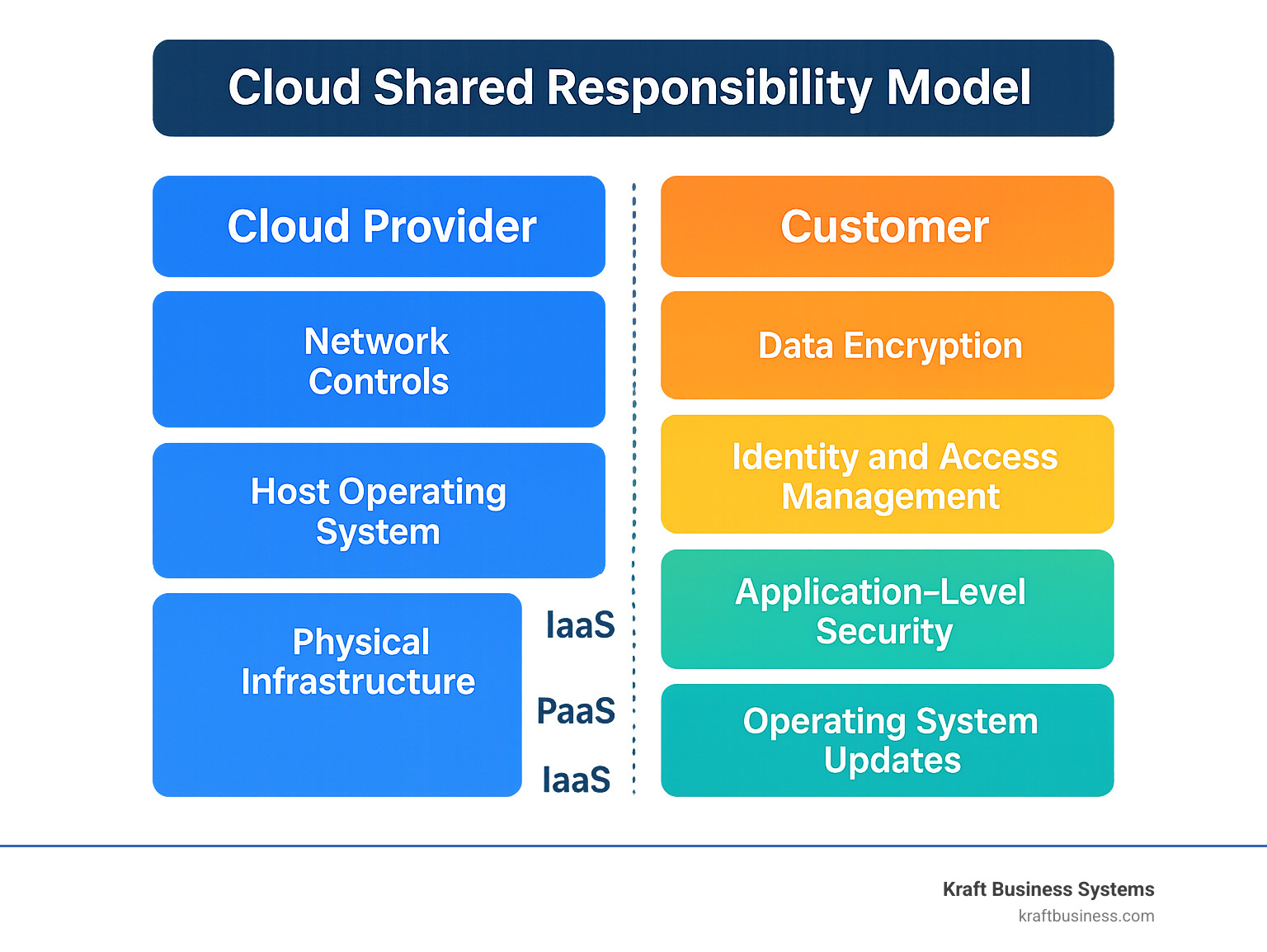
Cloud security solution providers are specialized companies offering comprehensive security tools and services to protect cloud-based data, applications, and infrastructure from cyber threats. They deliver solutions ranging from threat detection and vulnerability management to compliance monitoring and incident response.
Leading cloud security solution providers include:
- Palo Alto Networks (Prisma Cloud)
- CrowdStrike (AI-powered endpoint protection)
- Zscaler (Zero trust architecture)
- Microsoft Defender for Cloud (Native Azure security)
- Wiz (Agentless cloud security)
- SentinelOne (Purple AI cybersecurity)
The cloud security landscape is increasingly complex. 76% of enterprises now use two or more cloud providers, creating new attack surfaces. Furthermore, 61% of organizations reported cloud security incidents in 2024, more than double the previous year.
Businesses face daily threats from misconfigurations, insecure APIs, and challenges in managing identity and access across multiple clouds. Traditional security tools are insufficient for this environment. A single breach can cost millions in damages and lost trust. The right cloud security provider provides the visibility and protection you need to operate confidently.
Cloud security solution providers terminology:
- cloud security challenges and solutions
- cloud security monitoring solutions
- cloud security posture management
The Modern Cloud Threat Environment: Why Standard Security Isn’t Enough
The move to the cloud has fundamentally changed business security. Cloud complexity has exploded, with most enterprises using multiple cloud providers. This creates a fragmented security environment, making it difficult to maintain consistent protocols.
Misconfigurations are a leading cause of cloud security incidents, often accidentally exposing critical business data. These aren’t minor oversights; they are significant vulnerabilities.
Threats are also evolving rapidly. Cybercriminals are innovating faster than many businesses can adapt, with new AI and GenAI risks emerging. Data poisoning, model theft, and AI-powered social engineering are real concerns that traditional security tools cannot handle.
Persistent threats like data breaches, often resulting from insecure APIs, continue to pose significant risks. A lack of visibility across cloud infrastructures means you can’t protect what you can’t see. The sharp increase in reported cloud security incidents underscores this reality. Standard security approaches are no longer sufficient. This is why specialized cloud security solution providers are essential partners for modern businesses, offering tools built to address these evolving threats.
Decoding Cloud Security Acronyms: Key Capabilities Explained
The cloud security world is full of acronyms like CNAPP, CSPM, and CWPP. Understanding them is key to evaluating cloud security solution providers.
What are Cloud Native Application Protection Platforms (CNAPP)?
Cloud Native Application Protection Platforms (CNAPP) unify multiple security tools into a single command center for your cloud environment. This integrated approach provides a comprehensive view of your security posture.
A CNAPP combines several key capabilities:
- Cloud Security Posture Management (CSPM): Continuously scans cloud settings for misconfigurations.
- Cloud Workload Protection Platform (CWPP): Protects running applications, virtual machines, and containers.
- Cloud Infrastructure Entitlement Management (CIEM): Manages user permissions and access.
- Data Security Posture Management (DSPM): Finds and protects sensitive data.
A core benefit of CNAPP is shift-left security, which integrates security checks early in the development lifecycle. This prevents vulnerabilities from reaching production. Learn more about our Cloud Security services.
Agentless vs. Agent-Based Security: What’s the Difference?
Cloud security solution providers use two main monitoring approaches:
- Agent-based security involves installing software (an agent) on servers and applications. This provides detailed, real-time data and is excellent for runtime protection. However, it requires managing agents, which can add overhead.
- Agentless scanning connects to cloud provider APIs to gather data without installing software. Techniques like SideScanning or eBPF sensors offer deep insights with no performance impact. This method offers ease of deployment and rapid visibility.
Many organizations use a hybrid approach, combining broad agentless scanning with targeted agent-based protection for critical assets.
The Importance of a Unified Platform Over Siloed Tools
Using multiple, disconnected security tools creates blind spots and inefficiencies. A unified platform offers significant advantages:
- Single source of truth: Provides one clear, consolidated view of your entire security posture.
- Reduced alert fatigue: Uses contextual risk analysis to connect events and prioritize the most critical threats, reducing noise from insignificant alerts.
- Simplified management: Consolidates vendor relationships, contracts, and support into a single point of contact, freeing up your IT team.
- Cost efficiency: Reduces operational overhead and eliminates redundant tools, leading to long-term savings and a lower risk of costly breaches.
What Sets Leading Cloud Security Solution Providers Apart
The top cloud security solution providers distinguish themselves through unified platforms, advanced protection, and innovation.
Unified Platform Approach
The best providers understand that scattered tools create security gaps. They offer a unified approach for comprehensive visibility and control.
Palo Alto Networks’ Prisma Cloud platform exemplifies this by combining Cloud Detection and Response (CDR) with comprehensive CNAPP capabilities. It focuses on proactive threat detection and excels at strong network security, monitoring for unusual traffic patterns.
Wiz, trusted by large enterprises, offers a “Cloud Operating Model” designed to unite engineering and security teams. Its Security Graph technology provides context-driven insights to prioritize critical fixes.
Both providers deliver excellent multi-cloud and hybrid support, securing workloads across AWS, Azure, and Google Cloud with a single solution. This unified view helps businesses strengthen their security posture. Our Cybersecurity Solutions can guide these complex decisions.
Advanced Endpoint and Workload Protection
Protecting individual workloads, containers, and virtual machines is critical. Leading providers offer protection that goes far beyond traditional antivirus.
CrowdStrike’s Falcon platform uses AI-powered threat detection to analyze system behavior and identify novel attacks. This real-time threat hunting capability can stop threats that have never been seen before.
SentinelOne’s Singularity platform features “Purple AI,” a virtual analyst that provides continuous threat analysis. It is particularly effective at securing containerized applications.
These leaders combine agent-based and agentless protection, offering a dual approach that ensures enterprise-grade security without sacrificing performance. The goal is to stop threats like ransomware and nation-state attacks before they cause damage.
Innovation in Agentless Security
Innovative providers are proving that you can achieve deep visibility without the complexity of installing agents on every system.
Orca Security pioneered an agentless-first approach with its SideScanning technology. It not only finds issues but also enables tracing risks to code, allowing developers to fix problems at the source. Its security graph technology improves risk prioritization by understanding the relationships between cloud assets, reducing alert fatigue.
Wiz also focuses on providing comprehensive, agentless coverage with fast onboarding, allowing organizations to gain full visibility in minutes. This innovation removes friction, allowing teams to build products securely and efficiently. For guidance on building security frameworks, see our guide on IT Security Policy Development.
Zero Trust and Secure Access
The old “castle-and-moat” security model is obsolete. Leading cloud security solution providers accept Zero Trust principles, which mandate verifying every access request.
This is crucial for securing remote workforces accessing data scattered across multiple clouds. Secure Access Service Edge (SASE) is a modern approach that combines networking and security into a single cloud-native platform. Key components include:
- Zero Trust Network Access (ZTNA): Replaces traditional VPNs with more granular access controls.
- Strong CASB capabilities: Protect data in cloud applications.
- Data Loss Prevention (DLP): Secures sensitive information regardless of user location.
Companies like Zscaler and Netskope are built on these principles, offering global enterprise support with consistent security policies worldwide. The move to Zero Trust is a fundamental shift that provides superior protection against both external and internal threats.
How to Choose the Right Cloud Security Partner for Your Business
Choosing the right cloud security solution provider is a critical business decision that requires careful evaluation of your unique needs.
Assessing Your Organization’s Needs
Before comparing vendors, you must understand your own requirements.
- Business model: A small agency’s needs differ greatly from a multi-state manufacturer. Our IT Support for Small Businesses can help identify appropriate solutions.
- Budget considerations: Don’t just choose the cheapest option. The cost of a breach far outweighs the investment in proper security.
- Scalability requirements: Select a solution that can grow with your cloud footprint and evolving services.
- Industry specifics: If you’re in a regulated sector like healthcare or finance, you need a provider with deep compliance expertise.
At Kraft Business Systems, we help Michigan businesses steer these challenges by understanding their specific situation before recommending solutions.
Integrating Security into Your Development Lifecycle (DevSecOps)
Modern security must be integrated into the development process, not added as an afterthought. The right provider enables this shift.
- CI/CD pipeline integration: Automates security checks as developers write and deploy code.
- Infrastructure as Code (IaC) scanning: Reviews cloud infrastructure templates for security issues before deployment.
- Secrets detection: Scans code repositories for accidentally exposed passwords or API keys.
The best solutions promote a developer-first security approach, providing actionable guidance that empowers developers to build securely without slowing them down. This proactive stance prevents vulnerabilities from ever reaching production. For more on optimizing development, see our post on Cloud Computing in Business Operations.
How Top Cloud Security Solution Providers Differentiate Themselves
Beyond technical features, top providers stand out in ways that impact your daily operations and long-term success.
- Customer support: Look for 24/7 support from knowledgeable staff who can resolve issues quickly.
- Innovation and R&D: A provider’s investment in R&D indicates its ability to stay ahead of emerging threats.
- Partnerships and integrations: A rich integration ecosystem ensures the solution works with your existing technology stack.
- Pricing models: Understand how costs will scale as your organization grows.
Key evaluation criteria include:
- Cloud-specific and hybrid environment expertise
- Responsive customer support
- Robust third-party integrations
- Compliance and cyber insurance support
Meeting Regulatory and Cybersecurity Compliance
Compliance is about demonstrating a commitment to data protection. The right provider turns this from a burden into a competitive advantage.
Whether you need to meet GDPR, HIPAA, PCI-DSS, or SOC 2 standards, leading providers offer automated compliance reporting. These tools continuously monitor your environment against relevant frameworks, providing real-time visibility and remediation guidance. This automation builds customer trust and can positively impact cyber insurance premiums. Our expertise in Cybersecurity Compliance can help you select solutions that support your compliance goals.
Frequently Asked Questions about Cloud Security
Here are answers to some of the most common questions we receive about cloud security.
What are the four pillars of cloud security?
A comprehensive cloud security strategy rests on four essential pillars:
- Identity and Access Management (IAM): This is your first line of defense. It ensures the right people have the right access at the right time through strong authentication, the principle of least privilege, and continuous monitoring.
- Data Protection: This involves protecting sensitive data at rest and in transit. Key practices include encryption, data classification, and data loss prevention (DLP) measures to ensure data resides in compliant locations.
- Visibility and Compliance: You cannot protect what you cannot see. This pillar focuses on providing a clear view of your entire cloud environment to detect threats and misconfigurations, ensuring you meet regulatory and internal policy requirements.
- Threat Prevention and Response: This is your active defense system. It includes preventative controls like firewalls, rapid threat detection, and a solid incident response plan to minimize damage and ensure business continuity.
How do top cloud security solution providers handle AI-driven threats?
Leading cloud security solution providers are using AI to combat increasingly sophisticated, AI-driven cyberattacks.
- AI for security: Providers use machine learning and ML-based anomaly detection to identify unusual patterns and zero-day attacks that traditional systems would miss.
- Securing GenAI applications: As businesses adopt LLMs, providers are developing specific protections against data poisoning, model theft, and other risks unique to generative AI.
- AI Security Posture Management (AI-SPM): This extends traditional CSPM to cover AI services, helping organizations find and fix security issues in their AI deployments.
- AI-driven remediation: Some platforms now use AI to simplify and accelerate the process of fixing security issues, providing clear, actionable steps for remediation.
What is the role of a managed security service provider (MSSP) in cloud security?
Cloud security is complex, and many businesses lack the in-house resources to manage it effectively. A Managed Security Service Provider (MSSP) can bridge this gap.
- Expert management: An MSSP like Kraft Business Systems brings specialized knowledge to correctly configure and optimize complex cloud security solutions.
- 24/7 monitoring: We provide continuous, around-the-clock monitoring to detect and respond to threats as they happen.
- Bridging the skills gap: An MSSP gives you access to a team of security experts without the high cost and difficulty of hiring them directly.
- Cost-effectiveness: Outsourcing security is often more cost-effective than building an in-house team, providing enterprise-level expertise and tools for a fraction of the cost.
Our Managed Cybersecurity Services are designed to remove the complexity from cloud security, allowing you to focus on your business.
Conclusion: Securing Your Cloud with the Right Partner
The cloud has transformed modern business, but it also introduces a shared responsibility for comprehensive cloud security. Traditional security methods are no longer adequate for today’s dynamic, multi-cloud environments.
We’ve explored the modern threat landscape, key security capabilities like CNAPP and Zero Trust, and what sets top cloud security solution providers apart. The message is clear: effective cloud security requires the right tools, a proactive approach, and a knowledgeable partner. Success depends on choosing the right solutions and integrating them properly into your workflows.
The value of expertise is paramount. Cloud security is more than just buying software; it’s about expert configuration, integration, and incident response.
At Kraft Business Systems, we deliver innovative and secure technology solutions custom to our clients’ unique challenges. Our team of consultants and experts, serving Grand Rapids and clients across Michigan, takes the time to understand your specific needs, budget, and goals. We act as your trusted advisor, helping you steer complex security decisions and implement solutions that protect your business.
Your cloud environment should be a source of competitive advantage, not worry. With the right security partner, you can innovate with confidence.
Ready to transform your cloud security from a liability into a strategic asset? Secure your cloud environment with our expert Managed Cloud Security services and find how the right partnership makes all the difference.