AI Overview:
Cloud security risks don’t come from the cloud itself—they come from how businesses manage their data, access, and configurations. This guide explains the Shared Responsibility Model, outlines the eight most common cloud threats, and shows how misconfigurations, weak IAM, insecure APIs, insider risks, ransomware, and vendor breaches lead to real-world damage for Michigan industries.
You’ll also learn practical defenses like Zero Trust, encryption, monitoring, strong backups, and vendor vetting, along with why many SMBs rely on managed service providers for expert security, compliance, and 24/7 monitoring. The article ends with a simple action checklist and FAQ to help businesses quickly strengthen their cloud security posture.
When people talk about the security risks of the cloud, they’re usually missing the point. The cloud itself isn’t the problem; the real danger comes from how businesses manage their data and control who can access it once it’s there. Simple mistakes like misconfigured settings, sloppy identity management, and weak data protection can swing the door wide open for unauthorized access, data breaches, and major financial losses.
Understanding Your Cloud Security Responsibility
Moving your business to the cloud gives you incredible flexibility and the power to scale on demand. But it also flips the script on security, introducing a new model that catches a lot of business owners off guard.
Think of it like renting an office in a high-tech skyscraper. The building owner handles security for the lobby, the elevators, and the entire perimeter. They’ve got that covered. But you are still responsible for locking your own office door and deciding who gets a key.
This concept is called the Shared Responsibility Model. Your cloud provider—like Amazon Web Services or Microsoft Azure—secures the massive global infrastructure. That means the physical data centers, the servers, and the networking are all on them. Your job is to secure everything you put in the cloud:
- Your Data: This is your crown jewel. Protecting sensitive customer information, financial records, and intellectual property is entirely up to you.
- User Access: You control who can get into your cloud environment and what they are allowed to do once they’re inside.
- Applications: Any software you run in the cloud needs to be secured and kept up-to-date by your team.
- Configurations: Setting up your cloud services correctly is critical. One wrong click can accidentally expose your entire business.
This diagram does a great job of breaking down the division of security duties between you and your cloud provider.
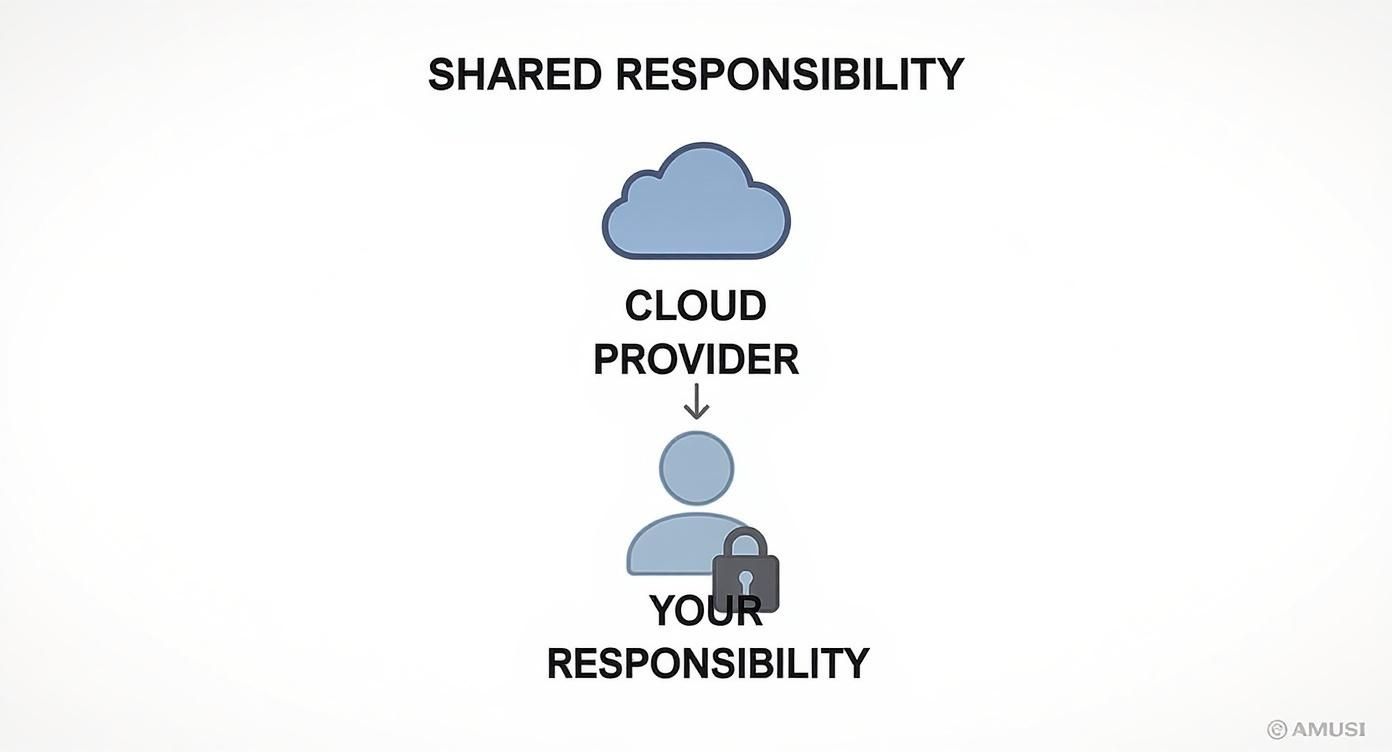
As you can see, while the provider manages the foundation, the most critical layers—the ones closest to your actual business—fall squarely on your shoulders.
Why This Matters for Michigan Businesses
Getting a handle on your security duties is the first, most important step toward building a real defense. This includes putting robust data security measures in place, a critical piece that often gets overlooked in the rush to the cloud. Ignoring these responsibilities can lead to devastating consequences, from crippling operational downtime to permanent damage to your reputation.
And this isn’t just a hypothetical threat. A staggering 83% of organizations worldwide have suffered at least one cloud security breach in recent years. Even more telling, 82% of all data breaches involved data that was stored in the cloud. That tells you exactly where attackers are focusing their energy.
This guide will walk you through the most pressing security risks of the cloud and give you a clear, practical roadmap for protecting your Michigan business.
The Eight Most Common Cloud Security Threats
Knowing you have security duties is one thing; knowing exactly what you’re up against is another. The risks that come with moving to the cloud aren’t just abstract concepts. They are specific, recurring issues that can grind your operations to a halt, expose sensitive data, and hit your bottom line hard.
Let’s break down the eight most common threats we see Michigan businesses face every day. By using clear analogies and real-world examples, we can cut through the technical jargon and show you how these vulnerabilities actually play out.
1. Cloud Misconfigurations
Think of a cloud misconfiguration as the digital version of leaving your office front door unlocked with a “Come on in!” sign hanging on it. It’s not some sophisticated hack; it’s a simple, preventable oversight where security settings aren’t implemented correctly, creating an accidental welcome mat for attackers.
These mistakes usually happen because cloud platforms are incredibly complex. A single unchecked box or a default setting left as-is can expose your most sensitive data to the entire internet. In fact, simple human error and setup mistakes are the main reasons cloud security fails. Research predicts that through 2025, a staggering 99% of cloud security failures will be the customer’s fault. Misconfigurations, like giving too much access or leaving storage buckets unsecured, account for roughly 27% of public cloud security incidents, as detailed in these cloud security statistics on Spacelift.io.
Here’s a classic example: a marketing team trying to share a file might accidentally set a cloud storage bucket full of customer lists to “public” instead of “private.” That one little mistake can spiral into a massive data breach, regulatory fines, and a complete loss of customer trust.
2. Poor Identity and Access Management
Identity and Access Management (IAM) is the gatekeeper of your cloud environment—it decides who gets to go where and do what. When your IAM is weak, it’s like giving every single employee a master key that opens every door in your building, from the front entrance to the CEO’s office and the server room.
When employees have far more access than they need for their job, it creates a huge, unnecessary risk. This goes against the principle of least privilege, but it’s a mistake we see all the time. If an employee’s account gets compromised, the attacker instantly gets all of their excessive permissions, letting them waltz through your systems like they own the place.
A recent study found that non-human identities—like those for automated services and applications—now outnumber human identities by an average of 50 to 1. If these accounts are unmanaged or have too many permissions, they create a massive, often invisible, attack surface.
3. Insecure APIs
An API (Application Programming Interface) is like a waiter at a restaurant. It takes your order (a request) to the kitchen (the server) and brings your food (the data) back to you. An insecure API is like a waiter who loudly announces every order, including your credit card number, to the entire restaurant.
APIs are the glue that connects different software applications, making modern business possible. But if they aren’t properly locked down, they become a favorite target for attackers.
Common API weaknesses include:
- Weak Authentication: Not properly checking who is making the request.
- No Rate Limiting: Failing to cap the number of requests, opening the door for denial-of-service attacks.
- Data Exposure: Sending back way more data than necessary, exposing sensitive info in the process.
4. Insider Threats
An insider threat comes from someone already inside your organization—an employee, a contractor, or even a former employee who still has access. These threats can be malicious, like a disgruntled worker who intentionally deletes critical files. More often, though, they’re accidental, like a well-meaning employee who falls for a phishing scam.
Accidental insider threats are far more common and just as dangerous. An employee might click a malicious link in an email without thinking, handing their login credentials straight to an attacker. Because the login looks legitimate, your security systems might not spot the breach right away, giving the attacker plenty of time to poke around and cause damage. Malicious insiders, on the other hand, use their built-in knowledge of your systems to bypass security and steal data for personal gain or revenge.
5. Advanced Ransomware Attacks
Ransomware isn’t just about locking your files anymore. Modern attackers use a multi-stage extortion strategy that’s far more sinister. First, they get into your cloud environment, usually through a misconfiguration or stolen credentials. Then, they quietly exfiltrate—or steal—your most sensitive data.
Only after they have a copy of your data do they encrypt your systems and demand a ransom. This gives them a powerful bargaining chip. Even if you have backups and can restore everything, they’ll threaten to leak your stolen data online if you don’t pay up. This “double extortion” tactic puts businesses under immense pressure to meet the attacker’s demands.
Using a public cloud is a bit like living in an apartment building. You have your own secure apartment, but you share the building’s foundation, plumbing, and electrical systems with everyone else. While cloud providers like AWS and Azure do an incredible job of keeping tenants isolated, a vulnerability in that shared infrastructure could theoretically affect multiple customers.
This risk is often called a shared tenancy or “noisy neighbor” issue. While the chance of an attacker “escaping” one virtual environment to attack another is extremely low (providers invest billions to prevent this), it’s not zero. A more common issue is resource contention, where one tenant’s massive workload could slow down performance for others sharing the same physical hardware.
7. Data Breaches and Data Loss
A data breach is the end goal of many cyberattacks. It’s what happens when an unauthorized person gets their hands on your sensitive information. In the cloud, a breach is often the result of another security failure—a misconfiguration, a compromised account, or an insecure API. Once an attacker is in, they hunt for the good stuff: customer records, financial reports, or your company’s intellectual property.
Data loss is a little different. It’s when data is destroyed or becomes unrecoverable, sometimes without any malicious intent. This can happen because of a hardware failure, an employee accidentally deleting a critical folder, or even a natural disaster hitting a data center. The only real defense against permanent data loss is a rock-solid backup and disaster recovery plan.
8. Supply Chain Compromises
Your business doesn’t operate in a silo; you rely on dozens of third-party vendors for everything from payment processing to your CRM software. A supply chain compromise happens when an attacker breaches one of your trusted vendors as a stepping stone to get into your systems.
Think of it this way: if your trusted HVAC company got hacked, an attacker could use their legitimate credentials to walk right into your building. In the digital world, attackers target things like software update tools or vendor support portals to push malicious code to all of their customers at once, leading to a widespread and devastating breach.
To help put these risks into perspective, the table below connects these technical issues to the real-world business consequences they can cause.
Common Cloud Security Risks and Their Business Impact
| Security Risk | Technical Vulnerability | Potential Business Impact |
|---|---|---|
| Cloud Misconfiguration | Unsecured storage, overly permissive network rules | Massive data breaches, regulatory fines (HIPAA, GDPR), public loss of trust |
| Poor IAM | Excessive user permissions, unmanaged service accounts | Unauthorized data access, internal fraud, system-wide compromise from one stolen password |
| Insecure APIs | Weak authentication, no rate limiting | Data theft, service disruption, attackers using your API to attack your customers |
| Insider Threats | Malicious or accidental actions by employees/contractors | Data theft, sabotage of critical systems, intellectual property loss |
| Advanced Ransomware | Data exfiltration followed by encryption | Operational shutdown, massive financial loss from ransom, public data leaks, brand damage |
| Supply Chain Compromise | Breach of a third-party software vendor or service provider | Widespread infection, loss of control over your own environment, significant reputational harm |
| Data Breach / Loss | Unauthorized access or accidental/malicious deletion | Stolen customer PII, compliance violations, permanent loss of critical business records |
Understanding these connections is the first step toward building a defense that protects not just your data, but your entire business operation.
How Cloud Risks Impact Michigan Industries
These cloud security risks aren’t just abstract tech problems—they have real-world, bottom-line consequences for businesses right here in Michigan. When a cloud environment gets hit, the fallout can snap supply chains, expose our neighbors’ private data, and completely wreck public trust.
To bring this home, let’s walk through how these threats could play out in some of our state’s most important sectors. Each scenario connects a specific cloud vulnerability to a local business, showing just how urgent it is to get cloud security right.
Healthcare in Detroit: A Misconfiguration Nightmare
Picture a busy healthcare clinic in Detroit. They’ve moved their electronic health records (EHR) to the cloud to make patient care smoother. A well-meaning IT staffer, trying to get a new telehealth app running, accidentally leaves a cloud storage bucket wide open to the public. Inside? Thousands of patient records.
This is a textbook cloud misconfiguration, and it’s a disaster waiting to happen.
Within hours, a cybercriminal stumbles upon the exposed data. We’re talking names, addresses, private diagnoses, and Social Security numbers—a goldmine for identity thieves. The clinic is now staring down a devastating crisis.
Security reports paint a grim picture for healthcare, showing it’s one of the industries most likely to suffer from sensitive data exposure. In fact, more than half (51%) of healthcare organizations with sensitive data in the cloud also have those databases exposed to the public internet.
That one simple mistake kicks off a catastrophic chain reaction. The clinic has to notify every single patient, handle a PR nightmare, and report the breach to federal regulators. The HIPAA investigation that follows could easily lead to millions of dollars in fines, not to mention the trust they’ve lost with the community—something you can’t put a price on.
Manufacturing in Grand Rapids: A Supply Chain Shutdown
Now, let’s head over to Grand Rapids. A Tier 1 automotive supplier there depends on a whole network of smaller vendors for crucial parts. They use a cloud-based portal to manage inventory and logistics, giving access to all those vendors. The problem is, one of those vendors—a small, local machine shop—has weak security and gets breached.
Using the shop’s legitimate login details, attackers pull off a supply chain compromise. They slip into the supplier’s cloud portal and unleash ransomware, locking up all the production schedules and shipping manifests. Just like that, the Grand Rapids factory grinds to a halt.
Without access to their logistics data, they can’t manage incoming parts or coordinate shipments. The shutdown sends shockwaves down the entire automotive supply chain, causing huge delays for the major automakers and costing the supplier hundreds of thousands of dollars for every single day of downtime. This is a perfect example of how the cybersecurity threats facing Michigan businesses can start far outside your own four walls.
Education in Traverse City: A Ransomware Crisis
Think about a mid-sized school district near Traverse City. They use a cloud platform for everything: student records, grades, parent communications. One morning, a teacher clicks a phishing email, and an attacker gains access to their account. Thanks to weak access controls, the attacker doesn’t stop there.
This is the start of an advanced ransomware attack. First, the attacker quietly copies sensitive student and faculty data. Then, they encrypt the entire system. The district gets a ransom note: pay up, or the stolen data gets leaked online.
The school is paralyzed. They can’t access attendance, medical records, or transcripts. This “double extortion” tactic puts immense pressure on the administration. Restoring from backups might be an option, but it’s slow, and it does nothing about the stolen data now in criminal hands. The district is left with an impossible choice that has severe financial and ethical consequences, all because of one compromised account.
Practical Controls to Mitigate Cloud Threats
Knowing the risks of the cloud is one thing, but actually putting up the defenses to protect your business is where the real work begins. Moving from theory to action means putting specific, practical controls in place to close security gaps and build an environment that can withstand an attack.
These aren’t complicated, one-off products you buy off a shelf. Instead, think of them as foundational principles that guide every security decision you make. Each one is a proactive, empowering step you can take to defend your data, your operations, and your reputation.
Adopt a Zero Trust Mindset
The core idea behind Zero Trust is powerful because it’s so simple: never trust, always verify. Think about a secure building where you need a keycard to get through the front door—that’s traditional security. Now, imagine needing to swipe that same keycard at every single door inside the building, from the breakroom to the server room. That’s Zero Trust.
It means nothing and no one gets a free pass, even if they’re already inside your network. Every single request to access a file or an application has to be authenticated and authorized, every single time. This approach massively shrinks your attack surface because even if a hacker compromises an account, they can’t move freely through your systems.
Enforce Strong Data Encryption
Encryption is your data’s best friend. It acts like a secret code, scrambling sensitive information so it’s completely unreadable to anyone who doesn’t have the correct key. To be effective, you need to apply it in two critical states:
- Encryption in Transit: This protects your data as it’s traveling—from a user’s laptop to the cloud, or between different cloud services. It’s like putting your mail in a locked briefcase before giving it to the courier.
- Encryption at Rest: This secures your data while it’s just sitting on servers or in databases. If a thief breaks into the data center and steals the physical hard drive, all they’ll get is a bunch of useless, scrambled data.
Despite how critical it is, encryption is shockingly underused. A recent study found that while 54% of all data stored in the cloud is classified as sensitive, a tiny 8% of organizations actually encrypt 80% or more of that data. That’s a huge gap leaving valuable information exposed. You can review key findings from the Thales Cloud Security Study to see the full picture of this disconnect.
Build Reliable Backup and Recovery Plans
Let’s be realistic: no security strategy is 100% foolproof. Data loss can and does happen, whether it’s from a ransomware attack, an employee accidentally hitting “delete,” or a hardware failure in the cloud provider’s data center. A rock-solid backup and disaster recovery (DR) plan is your ultimate safety net.
Your plan needs to ensure you can get your operations back up and running quickly with minimal data loss. This means regularly backing up your critical data and applications to a completely separate and isolated location.
Key Takeaway: Backups are useless if they don’t work. It’s essential to periodically test your recovery process to confirm you can actually restore your data when you need it most. This ensures your business can bounce back from an incident instead of being crippled by it.
A well-tested plan is often the only thing standing between a minor inconvenience and a business-ending catastrophe.
Implement Continuous Security Monitoring
You can’t protect your business from threats you can’t see. Continuous security monitoring is like having a 24/7 security guard who never sleeps, watching over your entire cloud environment for any suspicious activity, misconfigurations, or potential weak spots.
These systems are trained to automatically flag issues like:
- Someone trying to log in from an unusual location.
- A sudden, massive download of company data.
- Someone changing critical security settings without authorization.
- A newly discovered software vulnerability that needs patching.
Effective monitoring lets you spot the early warning signs of an attack and shut it down before real damage is done. For a deeper dive into this, our guide on Cloud Security Posture Management explains how these tools give you the visibility you need. And to ensure security is baked into your entire development pipeline, check out these essential DevOps security best practices.
Scrutinize Your Third-Party Vendors
Your security is only as strong as its weakest link, and that link could easily be one of your trusted vendors. Before you give any third-party software or service provider access to your cloud environment, you need to put them under the microscope with a thorough security assessment.
Don’t be afraid to ask tough questions about their security practices, their compliance certifications, and how they handle data. A breach on their end can quickly become a breach on yours, so understanding how they protect their own systems is non-negotiable. A strong vendor assessment process is your best defense against supply chain attacks and ensures your partners take security just as seriously as you do.
How Managed Services Simplify Cloud Security
Knowing the right security controls is one thing. Actually implementing and managing them around the clock? That’s a completely different ballgame. For a lot of small and medium-sized businesses here in Michigan, trying to handle complex cloud security in-house stretches their teams and budgets dangerously thin. It often leaves behind critical gaps that attackers are just waiting to find.
This is where bringing in a managed service provider (MSP) makes all the difference. An MSP bridges that huge gap between knowing what you should do and having the expert team to actually get it done right.
Think of an MSP as your dedicated, off-site security squad. They bring a level of specialized expertise and advanced tools that are usually out of reach for smaller companies—all without the staggering cost of hiring a full-time cybersecurity staff. It’s a smart investment in your company’s resilience, letting you focus on running your business, confident that your security is in expert hands.
Gaining Access to Specialized Expertise
Cloud security is a highly specialized field, and it changes by the minute. Good MSPs live and breathe this stuff. They’re constantly on top of the latest threats, new vulnerabilities, and the most effective defense strategies. Frankly, it’s a level of knowledge that’s nearly impossible for a small, generalist IT team to maintain.
That expertise pays off immediately. They can configure your cloud environment correctly from the start, manage intricate identity and access policies, and deploy sophisticated monitoring tools that catch threats your team might miss. Instead of asking your people to become cloud security gurus overnight, you get instant access to a team that already is.
Security teams face an overwhelming volume of risks. The average cloud asset has 115 vulnerabilities, and a shocking 76% of organizations have at least one public-facing asset that gives attackers a pathway to move deeper into their network. An MSP brings the manpower and the toolset needed to manage this massive scale.
Proactive Monitoring and Threat Hunting
One of the single biggest advantages of partnering with an MSP is 24/7/365 monitoring. Cyberattacks don’t work a 9-to-5 schedule. A threat actor could slip into your system at 2 a.m. on a Sunday, and without constant vigilance, you might not find out until Monday morning—long after the damage is done.
Managed service providers use advanced tools to keep a watchful eye on your environment around the clock. They actively hunt for suspicious activity, dig into alerts to see if they’re real threats, and jump on incidents in real-time. This proactive stance turns your security from a reactive scramble into a strategic defense, stopping threats before they can explode into a full-blown crisis.
Simplifying Compliance and Reporting
Meeting industry regulations like HIPAA or PCI DSS can be a massive headache for any business. The rules are dense, the documentation is exhausting, and the penalties for getting it wrong are steep. An MSP with experience in your specific industry can be a game-changer here.
They take the weight off your shoulders by:
- Implementing Compliant Controls: They make sure your cloud setup is built to meet the specific standards your industry demands.
- Generating Audit Reports: They provide the detailed, professionally formatted documentation you need to prove you’re compliant.
- Staying Current on Changes: As regulations shift and evolve, they keep your security posture aligned so you’re never caught off guard.
This kind of support takes the entire compliance lifecycle off your plate, cutting down on administrative busywork and minimizing the risk of costly fines. By working with a dedicated team, you can explore comprehensive cloud security solutions designed to handle these complexities, giving you true peace of mind.
Your Cloud Security Action Plan and Checklist
Knowing the risks is one thing, but stopping them requires action. All the theory in the world doesn’t mean much until you translate it into real-world defenses. This is where the rubber meets the road.
We’ve put together a straightforward, practical checklist to get you started. Think of it as your immediate action plan, designed specifically for Michigan SMBs who need to make meaningful security improvements right now.
Your Immediate Action Checklist
Use these steps as your starting point. Each one closes a common security gap and helps you build a much stronger defensive foundation.
- Conduct a Cloud Service Inventory
First things first: you can’t protect what you don’t know you have. Make a complete list of every single cloud service your business uses. This isn’t just about the big stuff like Microsoft 365; it includes every small, specialized app your team has signed up for. This inventory is your security map. - Review All User Access
Go through every user account with a fine-tooth comb. It’s time to enforce the principle of least privilege—a simple idea that says people should only have access to the data and systems they absolutely need to do their jobs, and nothing more. If an employee doesn’t need it, they shouldn’t have it. Revoke any permissions that are outdated or just plain excessive. - Test Your Data Backup Process
A backup plan is completely useless if it fails when you actually need it. Don’t wait for a crisis to find out. Schedule a test to restore a non-critical file or folder from your backups. This simple drill confirms your process works and gives you a realistic idea of how long a real recovery might take. - Launch a Phishing Awareness Drill
Since your employees are the first line of defense, you need to know how they’ll react under pressure. Run a simulated phishing campaign to see who takes the bait. Use the results to provide targeted, helpful training on how to spot and report suspicious emails. You’re not trying to catch people out; you’re trying to build a stronger human firewall.
Final Takeaway: Your security isn’t a “set it and forget it” project. It requires constant attention. This checklist isn’t a one-time task but the beginning of an ongoing discipline that will protect your business from threats that are always changing.
By tackling these tangible items, you move from just understanding cloud security risks to actively defending against them. For a more thorough evaluation, a professional security assessment can uncover the deeper vulnerabilities you might miss and help build a long-term strategy that’s a perfect fit for your business.
Frequently Asked Questions About Cloud Security
When you’re moving your business into the cloud, a lot of questions pop up. It’s completely normal. Let’s tackle some of the most common ones we hear from business owners so you can get some clear, straightforward answers.
Is My Cloud Provider Responsible For All Security?
No, and this is one of the biggest misconceptions out there. Cloud security works on what’s called a "shared responsibility model." Think of it like this: your provider (like AWS or Microsoft) is responsible for securing the building—the physical data centers, servers, and core infrastructure. But you are 100% responsible for securing everything you put inside your rented space. That includes your data, your applications, and, most importantly, who has the keys. They lock the front door of the apartment complex, but you still have to lock your own apartment door.
What Is The Most Important First Step I Can Take?
Without a doubt, the single most critical thing you can do right now is get a handle on your Identity and Access Management (IAM). This all comes down to enforcing the "principle of least privilege," which is just a formal way of saying people should only have access to the absolute minimum they need to do their jobs.
Why is this so crucial? Because non-human identities for automated services now outnumber human ones by an average of 50 to 1. Controlling every single one of those permissions is the fastest way to shrink your attack surface and prevent a small breach from turning into a catastrophe.
Getting IAM right stops a single compromised password from giving an attacker the keys to your entire kingdom. It’s your first and best line of defense.
How Much Should A Small Business Budget For Cloud Security?
How Much Should A Small Business Budget For Cloud Security?
There’s no magic number here. The right budget really depends on your specific situation—what industry you're in, how sensitive your data is, and what compliance rules you have to follow. A healthcare practice dealing with HIPAA will have very different security needs than a local manufacturing shop.
A better way to think about it is to see security not as a cost, but as an essential investment in keeping your business running. For most Michigan SMBs, the most cost-effective route is partnering with a managed services provider. This gives you access to a team of experts for a predictable monthly fee, which is almost always more affordable than trying to hire a dedicated security specialist in-house. It’s the smart way to tackle the real security risks of the cloud without blowing up your budget.
Don’t leave your cloud security to chance. The experts at Kraft Business Systems can build a robust defense strategy that protects your data and keeps your business running smoothly. Secure your cloud environment with Kraft Business Systems today.