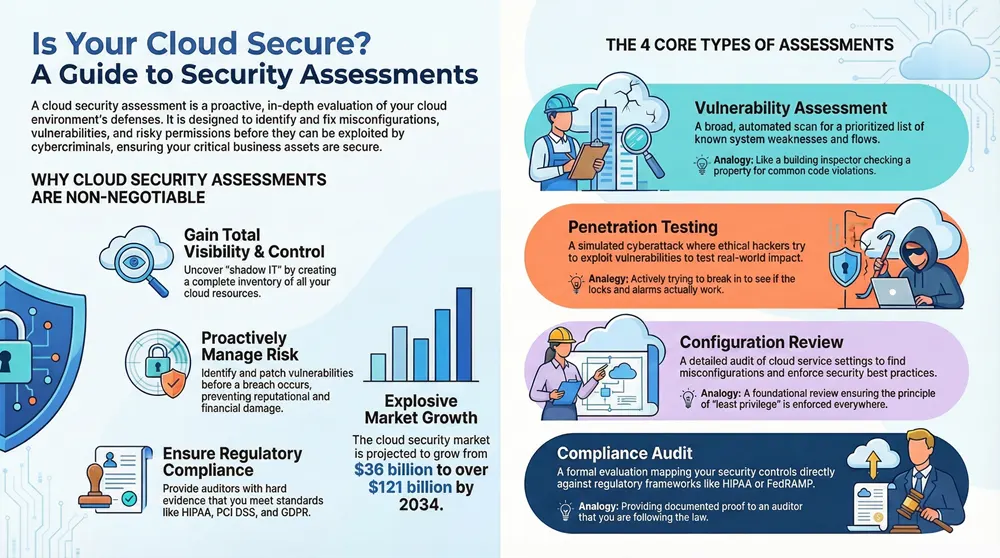
A cloud security assessment is a top-to-bottom evaluation of your digital infrastructure’s defenses. It’s designed to hunt down misconfigurations, vulnerabilities, and risky permissions across your entire cloud environment before a cybercriminal can. Think of it as a proactive, in-depth health check-up for your most critical business assets.
Understanding the Core Purpose of Cloud Security Assessments

Moving your operations to the cloud unlocks incredible flexibility and scale, but let’s be honest—it also brings new complexities and potential weak spots. A cloud security assessment cuts through the fog, giving you the clarity needed to manage these risks effectively. This isn’t just a simple scan; it’s a deep dive into your configurations, access controls, and data protection policies.
The process systematically combs through your cloud accounts and services to uncover security gaps and policy violations. By doing so, it helps your organization maintain a rock-solid security posture and protect sensitive information. It answers the one question that should keep every business owner up at night: “Are our cloud resources truly secure?”
Why These Assessments Are Essential
The value of a cloud security assessment goes way beyond just finding flaws. It’s about building a resilient and trustworthy foundation for your operations. With businesses moving to the cloud faster than ever, these evaluations have become a non-negotiable part of modern strategy.
Here’s why they’re so critical:
- Gaining Visibility and Control: Many companies have more cloud resources than they even realize—a phenomenon known as “shadow IT.” An assessment creates a complete inventory, making sure you can secure assets you didn’t even know you had.
- Proactive Risk Management: Instead of scrambling to respond to a breach, you can identify and patch vulnerabilities ahead of time. This preemptive approach saves money, time, and the headache of reputational damage.
- Ensuring Regulatory Compliance: Frameworks like HIPAA, PCI DSS, and GDPR don’t just suggest regular security checks; they often mandate them. Assessments provide the hard evidence needed to satisfy auditors and dodge costly penalties.
- Strengthening Incident Response: By understanding potential attack paths before they’re exploited, you can develop much more effective incident response plans and get your team ready for real-world threats.
A cloud security assessment transforms ambiguity into a clear, actionable roadmap. It moves your security strategy from a state of guesswork to one based on concrete data and validated findings, prioritizing the most critical risks first.
The market definitely reflects this growing need. The global cloud security market, valued at around USD 36 billion, is projected to rocket past USD 121 billion by 2034. This explosion is fueled by a 35% increase in cloud-specific security assessments from 2021 to 2023 alone, underscoring just how crucial they’ve become.
From Theory to Practice
At its core, an assessment helps you see your infrastructure through an attacker’s eyes. A vital part of this involves simulating real-world attacks to see how your defenses hold up. To get a better sense of this, you can learn more about cloud based penetration testing, which is a specific and aggressive form of assessment. This kind of active testing is the only way to validate whether your security controls actually work as intended.
Ultimately, these assessments are the bedrock of any robust security program. They deliver the insights needed to protect data, maintain customer trust, and ensure your business keeps running, no matter what. For a deeper look into foundational strategies, check out our guide on https://kraftbusiness.com/blog/cloud-security-for-businesses/.
What Are the Different Kinds of Cloud Security Assessments?
Trying to choose the right cloud security assessment can feel a bit like visiting a doctor. A general health check-up is one thing, but a specialized MRI is something else entirely. The same idea applies here. Not all assessments are built the same; each one has a specific job, ranging from broad, automated scans to deep, simulated attacks.
Knowing the difference is the first step toward making a smart decision to protect your cloud environment. Each type of assessment gives you a unique window into your security posture. Some are designed to find known cracks across your entire infrastructure, while others are built to see if your defenses can withstand a real-world attacker. Let’s break down the main categories so you can see which one fits your goals.
Vulnerability Assessments
Think of a vulnerability assessment as a thorough security checklist for everything you have in the cloud. It uses automated scanning tools to systematically check your systems against a huge database of known weaknesses, like software that’s out of date or common setup mistakes. The process is wide, but it doesn’t necessarily go very deep.
The main point here is to find and list potential weak spots as quickly and efficiently as possible. It’s a proactive check-up designed to catch the low-hanging fruit before an attacker does.
- What It Does: Scans for thousands of known vulnerabilities and spits out a prioritized list of things to fix.
- Analogy: It’s like a building inspector walking through a property and checking for common code violations—faulty wiring, missing smoke detectors, or leaky pipes.
- Best For: Getting a broad overview of your security hygiene and finding common, easily fixable flaws.
Penetration Testing
If a vulnerability assessment is the checklist, then penetration testing (or a pen test) is a simulated cyberattack. In this scenario, ethical hackers actively try to exploit the vulnerabilities found in an assessment to see just how far they can get. It answers the crucial question: “If a real attacker came after us, what damage could they actually do?”
This hands-on approach puts your defenses to the test in a real-world situation. Instead of just listing a potential weakness, a pen test demonstrates its actual impact by trying to breach systems, gain more privileges, and access sensitive data. It’s the ultimate validation of whether your security controls really work when things get real.
Configuration Reviews
Your cloud security is only as strong as its configuration. One single misplaced setting in AWS, Azure, or Google Cloud can leave your entire organization exposed. A configuration review is a painstaking audit of your cloud service settings to make sure they line up with security best practices and your own internal policies.
This kind of assessment focuses on the very foundation of your cloud infrastructure. Experts will comb through everything from Identity and Access Management (IAM) roles and network security group rules to your data encryption settings and logging configurations.
The whole point of a configuration review is to enforce the principle of least privilege and stamp out misconfigurations. Since these simple mistakes are responsible for a huge majority of cloud data breaches, this review ensures your environment is locked down by default.
Compliance Audits
For businesses in regulated industries like healthcare, finance, or government, security isn’t just a good idea—it’s the law. A compliance audit is a formal assessment specifically designed to prove that your cloud setup follows the security controls required by frameworks like HIPAA, PCI DSS, or FedRAMP.
This process involves gathering hard evidence to show that the required safeguards are in place and working as they should. It maps your current security controls directly to the regulatory requirements, flagging any gaps that could put you at risk of hefty fines or legal trouble.
The focus on these formal evaluations is clearly growing. Adoption of frameworks like the NIST Cybersecurity Framework shot up by 40% in the U.S. between 2020 and 2023. On top of that, 72% of firms now include their cloud infrastructure in routine security assessments, a big jump from just 54% in 2020. This trend shows a widespread understanding that continuous security validation is no longer optional. You can dig into the full research on the security assessment market for more details.
Your Step-by-Step Cloud Security Assessment Roadmap
So, you’re ready to tackle a cloud security assessment. It can sound like a huge, abstract task, but breaking it down into a clear, repeatable roadmap makes all the difference. Think of it less like a frantic audit and more like building a house—you need a solid blueprint before you can start looking for cracks in the foundation.
This roadmap is designed to move you logically from the big picture strategy all the way down to hands-on testing and, most importantly, making real improvements. Each phase builds on the last, creating a complete cycle of discovery, validation, and action.
Phase 1: Scoping and Planning
First things first: Scoping and Planning. This is easily the most critical part of the entire process. Before you touch a single line of code or look at a configuration file, you have to draw the lines on the map. Without a clear scope, your assessment will wander aimlessly, waste time, and probably miss the most important risks to your business.
This is where you answer a few fundamental questions:
- What are we protecting? Pinpoint the crown jewels—the critical applications, data stores, and cloud services that absolutely have to be included.
- What’s our goal here? Are you aiming to pass a specific compliance audit, hunt for general vulnerabilities, or stress-test your team’s incident response plan?
- What are the rules of engagement? If you plan on doing any active testing, you need to set clear guidelines to make sure you don’t accidentally knock over a critical system during business hours.
Nailing down the scope ensures every ounce of effort is focused on the assets that matter most. It’s the key to getting relevant, high-impact results.
Phase 2: Information Gathering
With the scope locked in, it’s time for Information Gathering. The mission here is simple: create a complete and accurate map of everything inside the boundaries you just defined. You can’t secure what you don’t know you have, and this phase is all about achieving total visibility.
This means finding and documenting every relevant asset. We’re talking virtual machines, storage buckets, databases, user accounts, and all the network plumbing that connects them. The process creates a detailed inventory of how everything is configured and interconnected, giving you the foundation for everything that comes next.
Phase 3: Threat Modeling
Okay, you have your asset inventory. Now we shift from “what we have” to “how could someone break it?” This is Threat Modeling, a structured exercise where security pros put on their black hats to analyze your architecture and data flows, hunting for potential attack paths and security flaws.
Threat modeling forces you to see your cloud setup through an attacker’s eyes. It helps answer questions like, “If an attacker got control of this user account, what’s the worst they could do?” By spotting plausible threats before they’re exploited, you can proactively build up your defenses around your most vulnerable points.
This forward-thinking process is what separates a good assessment from a great one. It allows you to anticipate potential attacks and prioritize your fixes based on the real-world business impact of a threat, not just a raw list of vulnerabilities.
Phase 4: Vulnerability Testing
This is where the rubber meets the road. During the Vulnerability Testing phase, we actively probe your environment to find and confirm weaknesses. It’s a mix of automated scanning to catch the low-hanging fruit and expert-led manual testing to uncover the subtle flaws that automated tools almost always miss.
This phase is hands-on and includes things like:
- Running vulnerability scans against servers and container images.
- Performing penetration tests to simulate how a real attacker would try to get in.
- Analyzing configurations to spot any deviations from security best practices.
This practical testing provides concrete proof of vulnerabilities, turning them from theoretical risks into confirmed issues that need to be addressed.
This infographic shows how these different layers of investigation come together in a comprehensive assessment.
The flow from discovering vulnerabilities to validating compliance shows how each type of testing builds a more complete picture of your security.
Phase 5: Reporting and Remediation
Finally, we arrive at what is arguably the most important phase: Reporting and Remediation. All the data you’ve gathered and the vulnerabilities you’ve found are pretty much useless without a clear plan to fix them. A quality assessment provider won’t just hand you a giant list of problems.
A good report prioritizes vulnerabilities based on risk, provides clear evidence for every finding, and gives you actionable, step-by-step guidance on how to fix things. This report becomes the blueprint for your security team to start closing the gaps. From there, a structured remediation process ensures that fixes are actually implemented, verified, and tracked, turning the insights from your assessment into real, measurable security improvements.
Meeting Compliance Demands with Cloud Assessments
For a growing number of businesses, strong cloud security isn’t just a good idea—it’s the law. Trying to untangle the complicated web of industry regulations and data protection laws can feel like a full-time job. This is where cloud security assessments come in. They act as the critical bridge between your technical security measures and your legal obligations.
Think of it this way: an assessment provides the documented proof you need to show auditors you’re doing your due diligence, helping you avoid crippling fines. It’s a systematic process of mapping your cloud setup directly against the specific rules of regulations like HIPAA or PCI DSS. This gives you clear, objective evidence that you’re protecting sensitive data the way you’re legally required to.
Healthcare And HIPAA Compliance
In healthcare, the Health Insurance Portability and Accountability Act (HIPAA) has incredibly strict rules for protecting electronic Protected Health Information (ePHI). Just moving your data to a “HIPAA-compliant” cloud provider like AWS or Azure isn’t enough. The responsibility for securing that data still lands squarely on your shoulders.
A HIPAA-focused cloud assessment is designed to verify that every required safeguard is not just in place but working correctly. This means taking a deep dive into a few critical areas:
- Access Controls: Making absolutely sure that only authorized staff can get to ePHI, usually by checking your Identity and Access Management (IAM) configurations.
- Data Encryption: Confirming that patient data is encrypted both when it’s sitting on a server (at rest) and when it’s moving across the network (in transit).
- Audit Trails: Ensuring that comprehensive logs are turned on to track every single time sensitive information is accessed or changed.
Without this kind of validation, a healthcare provider is essentially flying blind, risking not just a data breach but also massive regulatory penalties.
Government And FedRAMP Standards
If you’re a government agency or a contractor working with one, you’re playing in a different league with even tougher rules. The main one is the Federal Risk and Authorization Management Program (FedRAMP), which sets the standard for security assessment, authorization, and ongoing monitoring of cloud services.
A FedRAMP assessment is exceptionally rigorous. It evaluates hundreds of specific security controls, from system hardening and contingency planning to physical and environmental protections, ensuring that cloud environments meet the high bar set for handling government data.
Achieving and keeping a FedRAMP authorization is flat-out impossible without regular, detailed cloud security assessments. These evaluations are the bedrock for proving that your cloud deployment has the security posture needed for public sector work.
Finance And PCI DSS Requirements
For any business that touches cardholder data, the Payment Card Industry Data Security Standard (PCI DSS) is non-negotiable. This global standard is all about reducing credit card fraud by enforcing tight controls on how payment data is stored, processed, and sent.
A cloud security assessment built for PCI DSS compliance will put your environment under a microscope to:
- Build and Maintain a Secure Network: This involves reviewing firewall rules and making sure your network is segmented to keep the cardholder data environment isolated.
- Protect Cardholder Data: The assessment confirms that strong encryption is used for stored data and during transmission over public networks.
- Implement Strong Access Control Measures: This means meticulously checking who can access payment data and how that access is managed and monitored.
The global nature of finance means compliance is a worldwide concern. While North America currently holds 35% of the market share for security assessments, the Asia-Pacific region is projected to see growth exceeding 8.5% annually through 2030. This rapid expansion is driven by sectors like banking and healthcare that demand continuous risk management in their cloud operations. You can explore more about these market trends and their drivers in the full Mordor Intelligence industry report.
Ultimately, these industry-specific assessments are vital tools for managing risk. They provide the necessary validation to meet legal duties and satisfy auditors. To better understand the preparation involved, check out our IT compliance audit guide for practical tips.
A Practical Checklist for Your Next Cloud Assessment
Let’s be honest, “cloud security assessment” can sound intimidating. But when you break it down, it’s really just a structured way to poke and prod at your cloud setup to find the weak spots before someone else does. A good checklist turns this complex job into a series of manageable, focused reviews.
Think of this as your guide, whether you’re kicking the tires on your own setup or bringing in a third-party expert. Each category is a critical pillar of a strong cloud foundation, helping you systematically hunt down and fix potential problems.
Pre-Assessment Preparation
Before you start scanning for vulnerabilities, you need a game plan. This initial stage is all about setting the scope and making sure the assessment is actually focused on what matters most to your business. Skipping this is like starting a road trip without a map.
- Have you actually identified and inventoried all your critical cloud assets, apps, and data stores? You can’t protect what you don’t know you have.
- Is the scope of the assessment crystal clear? This includes the specific cloud accounts and services that are in or out.
- Has a security baseline been established using industry standards (like the CIS Benchmarks) and your own internal policies?
Identity and Access Management Controls
Who can access what? This is the absolute cornerstone of cloud security. It’s no surprise that misconfigured permissions are one of the top causes of data breaches, which is why this area needs your full attention. Your checklist should definitely include a deep dive into your access policies, and it’s a great time to make sure you’re following modern password manager best practices to keep user credentials locked down.
Strong Identity and Access Management (IAM) isn’t just about handing out permissions. It’s about relentlessly enforcing the principle of least privilege. Every single user and service should only have the bare-minimum access they need to do their job—and nothing more.
Here are the key questions you need to be asking:
- Is multi-factor authentication (MFA) mandatory for all users, especially anyone with admin-level keys to the kingdom?
- Are all privileged IAM roles documented and reviewed on a regular schedule (say, quarterly)?
- Do you have a solid process for immediately disabling or deleting inactive user accounts and old, unused credentials?
- Are you actively hunting for overly permissive roles, especially those using wildcard permissions (
*)?
Data Protection and Encryption
Your data is the prize. Making sure it’s protected, whether it’s just sitting there, moving across the network, or being actively used, is non-negotiable for any real security assessment.
- Encryption at Rest: Is data encryption switched on for all your storage services (think S3 buckets or Azure Blob Storage) and databases?
- Encryption in Transit: Is all data flying across the network protected using strong TLS encryption?
- Key Management: Are your encryption keys managed securely? Access should be locked down tight, and keys should be rotated regularly.
- Data Recovery: Have you enabled automated backups? More importantly, have you actually tested them recently to make sure you can restore the data when you need it?
Network Configuration Security
Your network setup is your first line of defense against the outside world. One sloppy firewall rule or a port left open by mistake can be an open invitation for an attacker. This part of the assessment puts your network perimeter and internal segmentation under the microscope.
- Are all security groups, firewalls, and network access control lists (ACLs) being reviewed to ensure they only allow traffic that is absolutely necessary?
- Is public access to services and resources shut off by default unless there’s a compelling business reason for it to be open?
- Are you using secure connections, like private endpoints or VPNs, for any and all administrative access?
This checklist gives you a solid framework to run an effective cloud security assessment. It empowers you to ask the right questions and, ultimately, build a much more resilient cloud environment.
How to Choose the Right Security Assessment Provider
Picking the right partner for your cloud security assessment is just as critical as the assessment itself. The wrong choice leaves you with a generic, jargon-filled report of low-priority issues. The right one, however, becomes a strategic ally who translates technical findings into a clear, business-focused security roadmap.
You need to look beyond the basic claims of “expertise.” A true cloud security specialist has deep, platform-specific knowledge of AWS, Azure, and Google Cloud. Sure, their team should have the right technical certifications, but what really matters is their proven experience in your industry, whether it’s healthcare, manufacturing, or government.
Evaluating Potential Partners
When you’re vetting potential partners, always ask to see sample reports. A quality report isn’t just a data dump of vulnerabilities. It should be clear, prioritized by business risk, and packed with actionable recommendations. Can you easily tell what the most critical threats are and what you need to do next?
This is where you separate the real experts from the automated scanners.
- Technical Depth: Do they have certified pros with hands-on experience in cloud platforms like AWS, Azure, or GCP?
- Industry Experience: Can they point to a track record of success with businesses in compliance-heavy sectors like yours?
- Actionable Reporting: Is their deliverable a clear, prioritized plan, or just a long list of findings without any context?
A great security partner doesn’t just find problems; they provide a clear pathway to fixing them. Their value is measured by how effectively they help you reduce real-world risk and strengthen your security posture over time, turning assessment findings into measurable improvements.
For businesses navigating complex compliance needs, it’s vital to choose a provider who gets your unique challenges. At Kraft Business Systems, for example, we specialize in security assessments designed for organizations where compliance isn’t just a checkbox—it’s paramount. Our entire approach is focused on aligning technical findings with your strategic business goals to build a cloud environment that’s not just secure, but resilient.
Choosing the right firm is the first step toward building a more secure future. For more insights on what to look for, check out our detailed guide on selecting cloud security solution providers.
Frequently Asked Questions About Cloud Security Assessments
When we start talking about cloud security assessments, a few key questions always come up. Let’s tackle them head-on, clearing up the common points of confusion so you can make smarter decisions for your business.
How Often Should We Conduct a Cloud Security Assessment?
We get this one a lot. The simple answer is at least once a year. Think of it as your annual security check-up.
But if you're in a heavily regulated industry like healthcare or finance, or your cloud setup is constantly changing with new features and services, you need to be more aggressive. In those cases, running a full assessment every quarter or twice a year is a much safer bet.
Between those deep dives, you should have continuous, automated scanning in place to catch any new issues that pop up day-to-day.
What Is the Difference Between a Cloud Security Assessment and a Traditional Audit?
This is a great question because the two sound similar but are worlds apart. A traditional security audit is a broad-strokes affair, looking at everything from your on-premise servers and physical office security to general IT policies.
A cloud security assessment, on the other hand, is a specialist's game. It zooms in on the unique, complex, and often confusing risks of platforms like AWS, Azure, or Google Cloud.
It’s specifically designed to scrutinize things that don't really exist in a traditional IT environment, like:
Identity and Access Management (IAM) policies, which are notoriously easy to misconfigure.
The security of serverless functions and containerized applications.
How well you're holding up your end of the shared responsibility model.
These elements are the heart and soul of cloud infrastructure, and a standard audit just isn't equipped to evaluate them properly.
The core distinction lies in focus. A traditional audit verifies broad compliance, while a cloud assessment validates the technical security of a dynamic, code-driven infrastructure where misconfigurations pose the greatest threat.
What Are the Most Common Vulnerabilities Found in the Cloud?
You might expect to hear about sophisticated hacks and zero-day exploits, but the reality is much more mundane—and preventable. The most frequent issues we uncover are almost always rooted in simple human error and basic misconfigurations.
Time and again, we find things like overly permissive access rights that give a user or service way more power than they need. We also see publicly exposed data storage buckets and unencrypted databases or backups far too often. Another big one is weak or completely missing multi-factor authentication (MFA) on critical administrator accounts, alongside poor logging that makes it impossible to spot suspicious activity.
Nailing these fundamental configuration settings is the single most important step you can take toward a truly secure cloud environment.
Partnering with the right experts can transform your security posture from reactive to resilient. The team at Kraft Business Systems provides specialized cloud security assessments that align with your business goals, ensuring your infrastructure is secure and compliant. Learn more by visiting https://kraftbusiness.com.