AI Overview:
Zero Trust is a modern cybersecurity framework that replaces implicit trust with continuous verification of every user, device, and access request—no matter the location. This guide explains why traditional perimeter-based security fails in today’s remote and cloud-driven environments and how Zero Trust shifts protection from the network to identity. It breaks down the core pillars—identity verification, device health validation, least-privilege access, and microsegmentation—and provides a practical roadmap for implementation. The article also shows how Zero Trust applies across industries like healthcare, manufacturing, education, and government, and emphasizes that Zero Trust is an ongoing strategy focused on reducing risk, limiting breach impact, and enabling secure business operations.
Switching to a Zero Trust security framework isn’t a small tweak; it’s a complete overhaul of your security mindset. You’re moving away from the old-school “implicit trust” model to a much smarter “never trust, always verify” posture. This means continuously validating every single user and device, no matter where they are, before letting them anywhere near your critical resources. It’s a foundational change that secures your business from the inside out.
Why Zero Trust Is a Modern Business Imperative
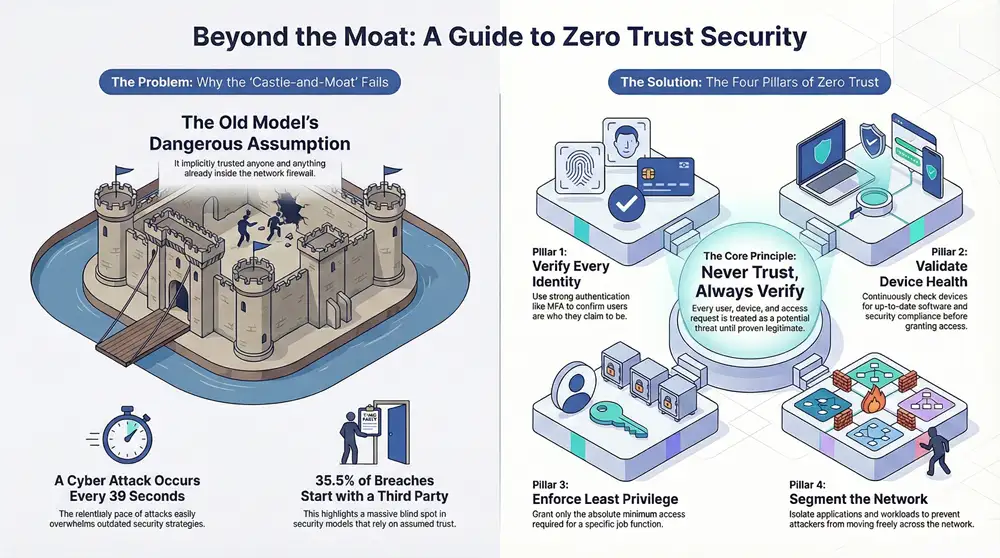
Rethinking your security isn’t just an upgrade anymore—it’s a core business necessity. The traditional “castle-and-moat” strategy, where a beefy firewall was supposed to be enough, is fundamentally broken. That old model made a dangerous assumption: anyone already inside the network was trustworthy. In an age of remote work and sophisticated cyber threats, that’s a gamble you can’t afford to take.
Modern workplaces do not have clear boundaries. Your employees, partners, and contractors are logging in from home offices, coffee shops, and personal devices. Every one of those connection points is a potential vulnerability that old-school security just can’t handle.
The Problem with Assumed Trust
When you assume trust, a single compromised password or device can give an attacker the keys to the kingdom. Picture this: a Michigan-based manufacturing firm works with a trusted third-party vendor. That vendor gets breached. If the vendor has standing, unchecked access to the manufacturer’s network, the attackers can waltz right in, moving laterally to steal sensitive IP or shut down production lines.
This isn’t just a hypothetical. The push for Zero Trust is happening for good reason. Cyber attacks are relentless, with a new incident happening every 39 seconds worldwide. It’s no surprise that 76% of enterprises are now actively implementing Zero Trust strategies. Digging into breach data reveals that a staggering 35.5% of all breaches start with a third party, highlighting a massive blind spot in security models that don’t verify every single access request.
Shifting from Perimeter to Identity
Zero Trust flips the old model on its head. It makes identity the new security perimeter. Instead of trusting a device just because it’s on the “right” network, this framework puts every access request under a microscope.
Zero Trust operates on a simple but powerful principle: never trust, always verify. Every access request is treated as if it’s coming from a hostile network until the user and their device are proven to be legitimate and secure for that specific transaction.
This constant verification is the heart of implementing Zero Trust effectively. Before granting access, it checks several things:
- User Identity: Is this person who they claim to be? This is locked down with strong authentication like MFA.
- Device Health: Is the device they’re using secure? It checks for up-to-date software, malware protection, and proper configurations.
- Request Context: Is this request normal? Does this user typically log in from this location at this time of day?
Building your security around these principles directly tackles the realities of a distributed workforce and a constant barrage of threats. This guide will give you a practical, step-by-step roadmap to make this essential shift. For a deeper dive into the core concepts, check out this great read on What is Zero Trust Security and why it matters.
What Zero Trust Architecture Actually Looks Like
Let’s get one thing straight: Zero Trust isn’t a product you buy off the shelf. It’s a fundamental shift in your security mindset—a strategic framework built on the core principle of “never trust, always verify.” Each part of this framework works together to build a far more resilient security posture for your organization.
We have to move past the old-school “castle and moat” model where everything inside the network was trusted. In a Zero Trust world, it doesn’t matter if someone is logging in from your Michigan headquarters or a coffee shop in Traverse City. Every single access request gets the same level of scrutiny.
To pull this off, you need to understand the core pillars that hold the entire strategy together.
The Four Pillars of a Zero Trust Framework
Think of these pillars as the foundation for your security strategy. Each one addresses a critical piece of the puzzle, ensuring that trust is never assumed and always earned—every single time.
Let’s break down what each pillar does and see it in action.
| Pillar | Core Principle | Example in Action |
|---|---|---|
| Verify Every Identity | Assume no user is trusted by default. Identity is the primary security perimeter. | An engineer needs multi-factor authentication (MFA) to access a control system, not just a password. |
| Validate Device Health | A trusted user on a compromised device is still a major threat. | A doctor’s tablet is checked for an up-to-date OS and active antivirus before it can access patient records. |
| Enforce Least Privilege | Grant only the absolute minimum access required for a specific job function. | A marketing team member can’t access financial records, limiting the blast radius if their account is compromised. |
| Segment the Network | Isolate workloads and applications to prevent lateral movement by attackers. | A school’s student data application is “walled off” so a breach there can’t spread to other network systems. |
By building your security architecture around these four pillars, you create multiple layers of defense that are much harder for attackers to bypass.
Verify Every Identity
This is the absolute bedrock of Zero Trust. Your new security perimeter isn’t a firewall; it’s identity. We can no longer trust a connection just because it’s coming from inside the building. Every user, every service, every device has to prove who they are before they get access to anything.
And no, a simple username and password won’t cut it anymore.
We’re talking about strong authentication, with Multi-Factor Authentication (MFA) leading the charge. For example, when an engineer tries to log into a critical manufacturing control system, they can’t just type in a password. They might have to approve a push notification on their company phone or use a fingerprint scan to prove their identity in that exact moment. This simple step ensures a stolen password alone isn’t enough for an attacker to walk right through your front door.
For a deeper dive into making this first pillar a reality, check out our in-depth guide to identity and access management solutions.
Validate Device Health and Posture
Okay, so you’ve verified the user’s identity. But what about the device they’re using? A perfectly legitimate user on a malware-infected personal laptop is a huge risk. This is where the second pillar, device health validation, comes in. It continuously checks the security posture of every single endpoint trying to connect.
Picture a healthcare provider in Grand Rapids trying to access patient records from their personal tablet at home. Before the system grants access, it runs a quick checklist:
- Is the device managed by the organization?
- Is the operating system fully patched and up-to-date?
- Is endpoint protection software running and active?
- Are there any signs of an active threat on the device?
If that tablet fails any of these checks, access is denied. Period. This pillar treats every device as a potential threat until it can prove it’s trustworthy.
The momentum behind this framework is undeniable. Recent data shows 81% of organizations have already started implementing a Zero Trust model, with another 19% in the planning stages. This shift is particularly pronounced in cloud environments, where 84% are actively pursuing Zero Trust. Discover more insights about the state of Zero Trust adoption.
Enforce Least Privilege Access
The principle of least privilege is the third pillar, and it’s all about containment. It dictates that users and devices should only have the bare-minimum level of access needed to do their specific job—and nothing more. This dramatically limits an attacker’s ability to move around your network if they manage to compromise an account.
A marketing team member at a firm in Detroit, for instance, has no business accessing financial records or developer source code. Under a Zero Trust model, their access is surgically scoped only to marketing apps and data. If their account gets phished, the attacker is trapped in that small segment, unable to reach the company’s crown jewels. This pillar ensures a small breach doesn’t become a full-blown catastrophe.
Segment Networks with Microsegmentation
The final pillar, microsegmentation, involves breaking up your network into tiny, isolated zones. Instead of one big, flat network where everything can talk to everything else, you create granular security controls around specific applications and workloads.
Think of it like building secure, fire-walled rooms inside your data center. An application that processes sensitive student data at a Lansing school district would be placed in its own microsegment. It can only communicate with a few explicitly authorized services, like a secure database. This containment strategy means that even if one application gets breached, the threat is boxed in and can’t spread across the network, stopping an attack in its tracks.
Your Zero Trust Implementation Roadmap
Let’s be clear: transitioning to a Zero Trust model is a journey, not a weekend project. It’s a methodical shift that builds security wins along the way. Think of this roadmap less like a rigid checklist and more like a flexible guide to help your Michigan organization make real, tangible progress.
The secret is breaking this massive shift into manageable chunks. I’ve seen companies try to do everything at once, and it almost always leads to misconfigurations and frustrated teams. It’s far better to focus on building a solid foundation first, starting with your most valuable assets and expanding from there.
This infographic breaks down the core pillars of the Zero Trust journey. It’s all about continuously verifying Identity, Devices, and Networks.
A successful rollout addresses each of these pillars, creating layers of defense instead of relying on a single security checkpoint.
Start with Discovery and Asset Identification
You can’t protect what you don’t know you have. The very first step is all about discovery—figuring out what your organization’s most critical data, applications, and services are. We call this the “protect surface.”
For a healthcare provider in the Grand Rapids area, this is obviously patient data (ePHI) and the Electronic Health Record (EHR) system. For a manufacturing firm near Detroit, it’s the proprietary CAD designs and the Industrial Control Systems (ICS) running the factory floor.
Once you’ve identified these crown jewels, you need to map out the transaction flows. How does data move? Who accesses it? Which applications interact with it? This mapping process shows you what normal, legitimate traffic looks like and helps you pinpoint where your security policies need to be the tightest.
Establish Strong Identity and Access Management
With your critical assets mapped out, the most impactful next move is to lock down identity. This is the absolute cornerstone of Zero Trust. You have to be able to verify with high confidence that a person is who they claim to be, every single time they ask for access.
The number one tool for this is Multi-Factor Authentication (MFA). A simple password just doesn’t cut it anymore. By requiring a second form of verification—like a code from an app, a fingerprint, or a physical key—you effectively neutralize the threat of stolen passwords. In fact, studies show MFA can block over 99.9% of account compromise attacks.
A Zero Trust implementation isn’t about blocking access; it’s about enabling secure access. The goal is to make it seamless for the right people to get what they need, while making it incredibly difficult for attackers to gain a foothold.
Here’s what your game plan for this stage should look like:
- Deploy a centralized Identity Provider (IdP): This becomes the single source of truth for all user identities and authentication.
- Enforce MFA everywhere: Start with admins and privileged accounts, then roll it out to every user across every application, especially your cloud services.
- Implement Conditional Access Policies: These are smart rules that check the context of a login. For example, you can block logins from unfamiliar locations or demand a higher level of authentication for a risky sign-in.
This identity-first approach delivers the biggest security bang for your buck. If you need a hand, exploring managed cybersecurity services can provide the expert support to get these critical controls configured correctly from the start.
Validate Device Health and Trust
A verified user on a compromised device is still a massive security risk. The next piece of the puzzle is to ensure every single device connecting to your resources meets your minimum security standards. This is called device posture assessment.
This isn’t a one-and-done check during enrollment. A device’s health status must be re-validated with every access request. It’s a continuous process.
An effective device trust strategy includes several key checks:
- Device Management Enrollment: Is the device enrolled in your system so you can enforce policies?
- Operating System Health: Is the OS up-to-date with all critical security patches applied?
- Endpoint Protection Status: Is antivirus/antimalware software installed, running, and getting the latest threat definitions?
- Disk Encryption: Is the device’s hard drive encrypted to protect data if it gets lost or stolen?
If a device fails any of these checks, you can block or limit its access until the issue is fixed. This simple step prevents unhealthy or non-compliant endpoints from poisoning your network.
Implement Network Microsegmentation
Once you have a strong grip on identities and devices, you can turn your attention to the network itself. The goal of microsegmentation is to kill the threat of lateral movement, which is when an attacker gets into one system and then hops freely across your internal network.
Instead of one big, flat network where everything can talk to everything else, you create tiny, isolated zones around specific applications. Think of it as building secure digital walls around your most sensitive systems.
For a K-12 school district in Lansing, this could mean putting the student information system in its own microsegment. It would only be allowed to communicate with a few specific, authorized databases. If a threat ever compromised that application, it would be contained, unable to spread to financial systems or teacher resources.
This might sound complicated, but you can start small. Pick one critical application from your discovery phase and build a segment around it. This creates a powerful layer of containment that ensures a minor breach doesn’t turn into a major disaster. By following this phased roadmap, you can methodically build a resilient Zero Trust architecture that protects your business from modern threats.
Applying Zero Trust to Your Industry
A Zero Trust strategy isn’t something you can just buy off the shelf; it’s a security mindset that has to be molded to fit the real world you operate in. How you implement Zero Trust in a Michigan hospital is going to look completely different from how it’s done at a manufacturing plant in Detroit. The trick is to apply the core principles to your industry’s specific soft spots and compliance headaches.
This all starts with identifying your most critical assets—what we call your “protect surface”—and building the right controls to wall them off. For some, that’s patient data. For others, it’s the heavy machinery that keeps the production lines humming.
Securing Healthcare and Patient Data
For any healthcare provider in Michigan, the prime directive is protecting electronic protected health information (ePHI) under the ironclad rules of HIPAA. A data breach here isn’t just a financial hit; it shatters patient trust and brings down the full weight of regulatory penalties.
Putting Zero Trust to work in a clinical setting means looking far beyond the nurses’ station laptops. You have to treat every single connected device that touches patient data as a potential way in for an attacker.
- Medical Devices (IoMT): We’re talking about infusion pumps, MRI machines, and patient monitors that are all hooked into the network now. Microsegmentation is absolutely essential to isolate these devices, making sure a compromised pump can’t be used as a stepping stone to the central Electronic Health Record (EHR) system.
- EHR Access: Getting into patient records has to be governed by strict least privilege. A doctor needs different access rights than a billing administrator, and those permissions must be backed by strong MFA and smart access policies that check the user, device, and location for every single login attempt.
In a hospital, “never trust, always verify” has to apply to every user and every device, every time. A doctor pulling up records from a hospital-issued, compliant tablet should get a different set of access rules than if they tried logging in from a personal phone at a coffee shop.
Protecting Manufacturing and Operational Technology
Step onto a factory floor, and the biggest fear is a production halt. A cyberattack that stops the line can cost millions in downtime and wreck expensive Industrial Control Systems (ICS) and operational technology (OT). The problem is, many of these systems were designed decades ago with practically zero security built in.
Bringing Zero Trust to the plant requires a delicate touch that understands the unique world of OT.
- Securing ICS and OT: These systems control physical machines and processes; they can’t handle the latency that comes with traditional IT security tools. The answer is smart network segmentation. By creating secure zones around critical production cells, you can stop a threat from jumping from the corporate IT network over to the OT network where the real work happens.
- Remote Maintenance Access: When a third-party technician needs to dial in to service a piece of equipment, Zero Trust is your best friend. Instead of giving them broad VPN access, you should grant temporary, just-in-time access only to the specific machine they need, for the exact time they need it. This slashes your third-party risk.
Addressing Other Key Michigan Sectors
The principles of Zero Trust are just as critical for other industries that drive Michigan’s economy, each with its own set of security priorities.
- Education: K-12 schools and universities are sitting on a treasure trove of sensitive student data. Implementing least privilege ensures a teacher can only access records for their own students, while microsegmentation can build a digital fortress around the Student Information System (SIS).
- Government: Public sector agencies handle enormous amounts of sensitive citizen data. Strong identity verification with MFA is a non-negotiable first step to block unauthorized access, while continuous monitoring is key to spotting and stopping threats targeting public services.
The need to apply Zero Trust principles only grows as infrastructures become more complex. You can see how this plays out when looking at today’s cloud security challenges. Regardless of your industry, the goal is always the same: assume no one and nothing is safe until it has been explicitly verified.
Now, let’s break down how these priorities look across different industries.
Zero Trust Application Across Key Industries
While the core philosophy of “never trust, always verify” is universal, the starting point and specific focus can vary dramatically depending on your sector’s unique risks and regulatory environment. For a hospital, protecting patient data is paramount; for a factory, it’s keeping the production line from grinding to a halt. The table below illustrates how different industries might prioritize their Zero Trust rollouts.
| Industry | Primary Security Focus | Key Compliance Mandate | Zero Trust Priority |
|---|---|---|---|
| Healthcare | Patient Data (ePHI) Confidentiality | HIPAA | Strict Identity and Access Management for EHRs; IoMT device segmentation. |
| Manufacturing | Operational Technology (OT) Availability | N/A (often internal) | Network segmentation to isolate OT from IT; secure remote access for vendors. |
| Education | Student & Staff PII Protection | FERPA | Least privilege access to Student Information Systems (SIS); network segmentation. |
| Government | Citizen Data & Public Service Integrity | FISMA, CMMC | Strong multi-factor authentication (MFA); continuous monitoring and threat detection. |
Ultimately, this table shows that your industry dictates your “why.” The “how” comes from applying the right Zero Trust controls—like identity management, device validation, and network segmentation—to solve your most pressing security and compliance problems first.
How to Sustain and Mature Your Zero Trust Strategy
Getting the foundational pillars of Zero Trust in place is a huge win, but I have to be honest—that’s not the finish line. Far from it. Real security resilience comes from treating Zero Trust as a living, breathing program, not a one-and-done project you can check off a list. It’s a fundamental shift in your security posture that has to evolve right alongside your business and the threats coming at you.
The initial rollout is just the start. The real work—and the real value—is in sustaining that momentum and maturing your strategy over time. This is where you move from a set of static rules to a dynamic, data-driven security model that can adapt on the fly.
Embrace Continuous Monitoring and Analytics
Here’s a simple truth I’ve learned over the years: you can’t refine what you can’t see. A mature Zero Trust strategy is built on a bedrock of comprehensive logging and continuous monitoring. This means pulling in telemetry from every corner of your environment—identities, endpoints, applications, and network traffic.
Think of this constant stream of data as your security nervous system. Once you feed it into a Security Information and Event Management (SIEM) tool or a dedicated analytics platform, you can start to establish a clear baseline of what “normal” looks like in your organization. When something deviates—like a user logging in from an unusual location or a device trying to touch a resource it has no business touching—your team gets an immediate flag.
A mature Zero Trust model doesn’t just block bad requests; it learns from them. Every piece of telemetry is an opportunity to fine-tune policies, shrink the attack surface, and make your security posture more intelligent.
This data-driven approach is what lets you graduate from simple block-and-allow rules to smarter, context-aware policies. For example, you could automatically step up authentication requirements if a user’s behavior seems a bit off, even if it’s not overtly malicious.
Refine Policies with Real-World Data
Your initial access policies are really just your best educated guess based on discovery and planning. The data you get from continuous monitoring is the reality check that shows you how well those guesses are holding up. This feedback loop is absolutely essential for maturing your Zero Trust implementation.
You might discover, for instance, that a specific group in your finance department regularly needs access to a resource you hadn’t planned for. Instead of them hitting a dead end and flooding your help desk, your monitoring data reveals this legitimate business need. You can then surgically adjust their access policies for that one specific thing, without opening up a massive, unnecessary security hole. This is a perfect example of the kind of practical cybersecurity posture management services that keep your defenses aligned with how your business actually works.
On the flip side, you’ll almost certainly find accounts with permissions they never, ever use. This data is pure gold for enforcing least privilege. You can confidently revoke that dormant access, methodically shrinking your attack surface and reducing risk without anyone’s productivity taking a hit.
Automate Your Security Workflows
As your Zero Trust environment grows, trying to manage policies by hand becomes completely unsustainable. The sheer volume of logs, alerts, and access requests will bury even the most dedicated security team. This is where automation shifts from a “nice-to-have” to a critical component of a mature strategy.
Automating your security workflows does more than just save time. It slashes the risk of human error and dramatically shrinks your response time when a potential threat pops up.
Here are a few ways we see automation make a real difference:
- Automated Incident Response: If an endpoint is flagged as non-compliant—say, its antivirus gets disabled—an automated workflow can instantly quarantine it from the network. This stops a potential threat in its tracks before it has a chance to spread.
- Just-in-Time (JIT) Access: Instead of giving engineers standing administrator privileges (a huge risk), they can request temporary, elevated access to a specific server for a set amount of time. The system automatically grants and, more importantly, revokes this access, logging every single action taken.
- Policy Enforcement: Automation is the only way to ensure your security policies are applied consistently across thousands of users and devices. It eliminates the “configuration drift” that always creeps into manually managed systems.
By handing these routine tasks over to automation, you free up your security experts to focus on what humans do best: strategic work like threat hunting and digging into the data to refine policies even further. This constant cycle of monitoring, refining, and automating is how you build and sustain a Zero Trust strategy that truly protects your organization for the long haul.
Common Questions About Zero Trust Implementation
Shifting to a Zero Trust model is a big change, and it’s totally normal to have questions about where to start, if it’s even possible for your business, and how you’ll know if you’re getting it right. Let’s tackle some of the most common questions we hear from Michigan businesses making this move.
Where Is the Best Place to Start a Zero Trust Implementation?
Almost every single time, the answer is identity. Before you get tangled up in complex network diagrams, you absolutely have to be confident about who—and what—is on your network.
By zeroing in on Identity and Access Management (IAM) first, you get the biggest security bang for your buck. Rolling out Multi-Factor Authentication (MFA) across your entire organization is probably the single most impactful security move you can make. Once that identity foundation is rock-solid, building out more granular access rules becomes a whole lot easier.
Can Small Businesses Realistically Implement Zero Trust?
Absolutely. Zero Trust is a mindset, a set of principles—not some monolithic product that only giant corporations can afford. Small businesses can and should adopt this model through smart, incremental changes that fit their budget.
Zero Trust isn’t about buying a single, expensive box. It’s a strategic approach that starts with using the tools you probably already own, like the security features built right into Microsoft 365 or Google Workspace, and then layering on targeted improvements.
Here are a few practical first steps we see small businesses take:
Enforce MFA Everywhere: This is a low-cost, high-impact starting point. Seriously, do this first.
Deploy Modern Endpoint Protection: Make sure every single device has up-to-date endpoint detection and response (EDR) software.
Use Your Cloud’s Native Controls: Dig into the security policies available in your existing cloud platforms and turn them on.
The key is to take it one piece at a time. Focus on one pillar of Zero Trust, get it right, and then move to the next. Don’t try to boil the ocean.
How Do You Measure the Success of a Zero Trust Initiative?
Success isn’t just about preventing breaches; it’s also about enabling your team to work securely and productively. You’ll want to track a mix of security metrics and operational ones to see that the framework is actually working as intended.
A successful rollout shows up in a few key areas. You should see a measurable reduction in security incidents related to unauthorized access. We also look for faster incident detection and response times because threats get contained within tiny microsegments, unable to spread.
Operationally, you can track the percentage of users and devices that are fully covered by MFA and conditional access policies. When it’s all working, the end result is that verified users on trusted devices get secure, seamless access to what they need with minimal friction. That’s the real win.
At Kraft Business Systems, we live and breathe this stuff. We specialize in helping Michigan organizations navigate the complexities of modern security. Our experts can help you build and manage a Zero Trust framework that protects your business from the ground up. Find out how our managed IT and cybersecurity solutions can secure your operations at https://kraftbusiness.com.